Thursday, October 13. 2011
Nettop Round-Up: Four Tiny PCs, Benchmarked And Reviewed
Via Tom's Hardware
-----
We're testing four nettops: Arctic Cooling’s MC001-BD, ASRock’s CoreHT 252B, Giada’s i50, and Zotac’s Zbox AD03BR-PLUS. All of these tiny, quiet systems take a very different approach to compact computing, and we fill you in on what makes them unique.
Intel’s Atom CPU might have been the driving force behind the popularization of the nettop form factor, but manufacturers are squeezing more powerful hardware into these tiny machines. Sometimes, more potent graphics performance is added via a mobile chipset. Sometimes, processing m muscle is emphasized instead with a CPU designed for powerful notebook. And now, APUs belonging to AMD's Fusion initiative are an option, serving up efficient power use and higher-performance graphics on a single processor die.
Truly, the nettop is no longer a stripped-down machine barely capable of Web browsing and word processing. These tiny PCs are tailor-made to excel in specific applications, which often includes use in a home theater.

Click here to get the full survey
Wednesday, October 12. 2011
Android app puts 3D Large Hadron Collider in your hand
Via DailyMail
-----
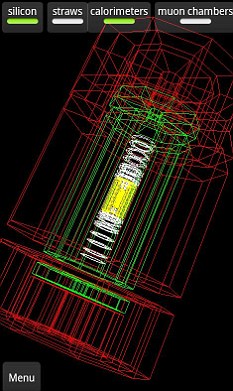
The app allows you to 'build' a 3D view of the reactions inside the LHC, and the huge banks of detectors surrounding the chamber, layer by layer. It's a spectacular insight into the machines at CERN
The new LHSEE app, free on Google Android phones and tablets, lets users see events unfolding live inside the particle accelerator in a 3D view. You can even see individual protons colliding.
The app has already been downloaded more than 10,000 times.
It was created by scientists at Oxford University, and has the full approval of CERN.
Naturally, it can't capture everything - the LHC produces gigabytes of data every second - but the view offers an exhilarating insight into 'Big Science'.
Tutorial videos about the ATLAS detector provide a relatively easy 'way in', and the 3D views allow you to view a stripped down version, then add layers of detectors.
It gives a very immediate, physical sense of the reactions going on inside - you can rotate the 3D model to view reactions from any angle.
It is pitched, according to Android market, at 'experts and non-experts alike', and offers the chance to explore different parts of the detector and learn about the reactions it's looking for.
Be warned, though - despite a game entitled 'Hunt the Higgs', it isn't exactly Angry Birds. You have to comb slides of reactions, guessing which subatomic particles are involved.
The app was built a team headed by Oxford University physicist Dr Alan Barr.'For ages I’d been thinking that with the amazing capabilities on modern smartphones we really ought to be able to make a really great app - something that would allow everybody to access the LHC data,' said Barr on the official Oxford science blog.
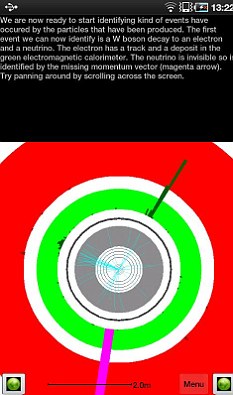
The app initially looks intimidating, but if you persist, the tutorial modes give a fairly gentle 'learning curve' towards understanding how the detectors surrounding the LHC work, and what they are looking for
'I’d sounded out a few commercial companies who said they could do the job but I found that it would be expensive, and of course I’d have to teach their designers a lot of physics. So the idea was shelved.'
'Then, a few months later, I had one of those eureka moments that make Oxford so wonderful.
'I was having a cuppa in the physics common room, and happened to overhear a conversation from Chris Boddy, one of our very many bright Oxford physics graduate students.'
'He was telling his friends that for fun he was writing some small test games for his Android phone. Well you just can’t let moments like that pass.'
By leading users through the coloured slides produced by the LHC, the app 'reverse engineers' the imagery so home users can understand the reactions - eventually. With the LHC predicted to either find the Higgs Boson or prove its non-existence next year, the capacity to watch events 'live' should also prove popular.
'With the app you can understand what these strange shapes and lines actually mean - in terms of the individual particles detected. Our hope is that people can now appreciate the pictures and the science all the more - and perhaps even be a little inspired,' said Barr.
As yet, the team has announced no plans for an iPhone version.
Monday, October 10. 2011
Japanese company "REAL-f" makes really f-ing accurate 3-D copies of your face
Via io9
-----
If 'Silence of the Lambs' gave you nightmares, you should probably just navigate away from this page right now. Otherwise, prepare to be impressed, intrigued, and deeply disturbed — all at the same time.
You're looking at the work of Japanese company REAL-f. REAL-f specializes in the production of "3-Dimensional Photo Forms," i.e. freakishly realistic masks and busts of just about anybody willing to throw down the cash to have one made of him/herself.
Those interested in possessing an exact replica of their face (down to the level of individual pores and eye vasculature, according to REAL-f's website) can get a 3D "face mask" for US $3,920. A copy of your entire head will set you back US $5,875. Additional face and head copies run $780 and $1,960, respectively.
Do I want one? Absolutely. Would I ever sleep in the same room as my mask? Absolutely not.
You can find more pictures on REAL-f's Website and Facebook Page
Saturday, October 08. 2011
Computer Virus Hits U.S. Drone Fleet
Photo courtesy of Bryan William Jones
A computer virus has infected the cockpits of America’s Predator and Reaper drones, logging pilots’ every keystroke as they remotely fly missions over Afghanistan and other warzones.
The virus, first detected nearly two weeks ago by the military’s Host-Based Security System, has not prevented pilots at Creech Air Force Base in Nevada from flying their missions overseas. Nor have there been any confirmed incidents of classified information being lost or sent to an outside source. But the virus has resisted multiple efforts to remove it from Creech’s computers, network security specialists say. And the infection underscores the ongoing security risks in what has become the U.S. military’s most important weapons system.
“We keep wiping it off, and it keeps coming back,” says a source familiar with the network infection, one of three that told Danger Room about the virus. “We think it’s benign. But we just don’t know.”
Military network security specialists aren’t sure whether the virus and its so-called “keylogger” payload were introduced intentionally or by accident; it may be a common piece of malware that just happened to make its way into these sensitive networks. The specialists don’t know exactly how far the virus has spread. But they’re sure that the infection has hit both classified and unclassified machines at Creech. That raises the possibility, at least, that secret data may have been captured by the keylogger, and then transmitted over the public internet to someone outside the military chain of command.
Drones have become America’s tool of choice in both its conventional and shadow wars, allowing U.S. forces to attack targets and spy on its foes without risking American lives. Since President Obama assumed office, a fleet of approximately 30 CIA-directed drones have hit targets in Pakistan more than 230 times; all told, these drones have killed more than 2,000 suspected militants and civilians, according to the Washington Post. More than 150 additional Predator and Reaper drones, under U.S. Air Force control, watch over the fighting in Afghanistan and Iraq. American military drones struck 92 times in Libya between mid-April and late August. And late last month, an American drone killed top terrorist Anwar al-Awlaki — part of an escalating unmanned air assault in the Horn of Africa and southern Arabian peninsula.
But despite their widespread use, the drone systems are known to have security flaws. Many Reapers and Predators don’t encrypt the video they transmit to American troops on the ground. In the summer of 2009, U.S. forces discovered “days and days and hours and hours” of the drone footage on the laptops of Iraqi insurgents. A $26 piece of software allowed the militants to capture the video.
The lion’s share of U.S. drone missions are flown by Air Force pilots stationed at Creech, a tiny outpost in the barren Nevada desert, 20 miles north of a state prison and adjacent to a one-story casino. In a nondescript building, down a largely unmarked hallway, is a series of rooms, each with a rack of servers and a “ground control station,” or GCS. There, a drone pilot and a sensor operator sit in their flight suits in front of a series of screens. In the pilot’s hand is the joystick, guiding the drone as it soars above Afghanistan, Iraq, or some other battlefield.
Some of the GCSs are classified secret, and used for conventional warzone surveillance duty. The GCSs handling more exotic operations are top secret. None of the remote cockpits are supposed to be connected to the public internet. Which means they are supposed to be largely immune to viruses and other network security threats.
But time and time again, the so-called “air gaps” between classified and public networks have been bridged, largely through the use of discs and removable drives. In late 2008, for example, the drives helped introduce the agent.btz worm to hundreds of thousands of Defense Department computers. The Pentagon is still disinfecting machines, three years later.
Use of the drives is now severely restricted throughout the military. But the base at Creech was one of the exceptions, until the virus hit. Predator and Reaper crews use removable hard drives to load map updates and transport mission videos from one computer to another. The virus is believed to have spread through these removable drives. Drone units at other Air Force bases worldwide have now been ordered to stop their use.
In the meantime, technicians at Creech are trying to get the virus off the GCS machines. It has not been easy. At first, they followed removal instructions posted on the website of the Kaspersky security firm. “But the virus kept coming back,” a source familiar with the infection says. Eventually, the technicians had to use a software tool called BCWipe to completely erase the GCS’ internal hard drives. “That meant rebuilding them from scratch” — a time-consuming effort.
The Air Force declined to comment directly on the virus. “We generally do not discuss specific vulnerabilities, threats, or responses to our computer networks, since that helps people looking to exploit or attack our systems to refine their approach,” says Lt. Col. Tadd Sholtis, a spokesman for Air Combat Command, which oversees the drones and all other Air Force tactical aircraft. “We invest a lot in protecting and monitoring our systems to counter threats and ensure security, which includes a comprehensive response to viruses, worms, and other malware we discover.”
However, insiders say that senior officers at Creech are being briefed daily on the virus.
“It’s getting a lot of attention,” the source says. “But no one’s panicking. Yet.”
Wednesday, October 05. 2011
What is Apple’s Siri, and will anyone use her?
By Sebastian Anthony
-----
The Apple “Let’s Talk iPhone” event has concluded. Tim Cook and a slew of Apple execs have taken it in turns to tell us about the latest and greatest Apple goodies, and rather underwhelmingly there’s no iPhone 5 and just significant takeaways: a cheaper and faster iPhone 4S, and an interesting software package called Siri. You can read all about the iPhone 4S on our sister sites Geek and PC Mag — here we’re going to talk about Siri.
If we look past the rather Indian (and feminine) name, Siri is a portable (and pocketable) virtual personal assistant. She has a speech-recognition module which works out what you’re saying, and then a natural language parser combs through your words to work out what you’re trying to do. Finally, an artificial intelligence gathers the possible responses and works out which one is most likely to be accurate, given the context, your geographical location, iOS’s current state, and so on.
 Siri
is, in essence, a computer that you can interrogate for answers, kind
of like a search engine that runs locally on your phone. If you’ve seen IBM’s Watson play Jeopardy,
Siri is basically a cut-down version. She isn’t intelligent per se, but
if she has access to enough data, she can certainly appear intelligent.
Siri’s data sources are open APIs, like Wikipedia or Wolfram Alpha, and
in theory there’s no limit to the number of sources that can be added
(though it does require significant developer time to add a new data
set). For now you can ask Siri about the weather or the definition of a
word, but in the future, if Apple links Siri up to United Airlines,
you’ll be able to book a plane ticket, just by talking. Because Siri
runs locally, she can also send SMSes or set reminders, or anything else
that Apple (or app developers) allow her to do.
Siri
is, in essence, a computer that you can interrogate for answers, kind
of like a search engine that runs locally on your phone. If you’ve seen IBM’s Watson play Jeopardy,
Siri is basically a cut-down version. She isn’t intelligent per se, but
if she has access to enough data, she can certainly appear intelligent.
Siri’s data sources are open APIs, like Wikipedia or Wolfram Alpha, and
in theory there’s no limit to the number of sources that can be added
(though it does require significant developer time to add a new data
set). For now you can ask Siri about the weather or the definition of a
word, but in the future, if Apple links Siri up to United Airlines,
you’ll be able to book a plane ticket, just by talking. Because Siri
runs locally, she can also send SMSes or set reminders, or anything else
that Apple (or app developers) allow her to do.
Artificial intelligence isn’t cheap in terms of processing power, though: Siri is expected to only run on the iPhone 4S, which sports a new and significantly faster processor than its predecessors, the A5. Siri probably makes extensive use of Apple’s new cloud computer cluster, too, much in the same way that Amazon Silk splits web browsing between the cloud and the local device.
Noise
That’s enough about what Siri is and how it works. Let’s talk about whether anyone will actually use Siri, which is fundamentally a glorified voice control search engine. Voice commands have existed in some semblance since at least as far back as the Nokia 3310, which was released in 2000. Almost every phone since then has had the ability to voice dial, or in the case of modern smartphones, voice activate apps and features.
When was the last time you saw someone talk to their phone? Driving and other hands-otherwise-occupied activities don’t count. When was the last time you walked down the street and heard someone loudly dictate “call mom” into their phone? Can you really see yourself saying “Siri, I want a kebab” in public?
It might lose its social stigma if everyone talks to their phone, but isn’t it already annoying enough that people swan down streets with hands-free headsets, blabbing away? It’s not like voice recognition is at the stage where you can whisper or mumble a command into your phone, either: you’re going to have to say, nice and clearly, “how do I get to the bank?” in public. Now imagine that you’ve just walked past the guy who’s talking to Siri — is he asking you for directions, or Siri? Now imagine what it would be like if everyone around you is having a one-sided phone conversation or talking to Siri.
Finally, there’re practical implications to consider, which Apple usually ignores in its press events. For example, will Siri only recognize my voice? What if I leave my phone in the living room and my girlfriend shouts out “honey, we should go to that Italian restaurant” — will Siri then make a reservation? On a more nefarious note, will my wife be able to say “Siri, show me my husband’s hidden email.” When walking down a street, will Siri overhear other conversations and react accordingly?
Siri will be fantastic in the car, that’s for certain. She will also be very accommodating when you’re on your own — imagine shouting across the room “Siri, do I need to wear a jacket today?” or “Siri, download the latest episode of Glee.” Siri will be unusable in public, though, while on the move — and that’s the one time where you really don’t want to be looking down at that darn on-screen keyboard.
Unreal Engine 3 Now Works in Flash. Yes, the Same Flash That’s In Your Browser
Via Kotaku
-----

What if one of the world's most popular 3D engines, the same one used to power many of the most popular console games in the world, also ran in your web browser? That would be pretty interesting, right?
Things just got interesting: Epic Games has announced that their incredibly popular Unreal Engine 3 now works in Adobe Flash, demoing a version of Unreal Tournament 3 running inside the new Adobe Flash Player 11.
That means porting existing games to work in a browser-based solution—and there are a ton of games on Unreal Engine 3—would be more or less turnkey.
A quick look at the screenshots provided by Epic indicate that the engine isn't as powerful as a non-browser-based engine—no big surprise there—but that it's still very much a "real" 3D experience. (I haven't yet seen the engine in motion.)
Even better, developers will be able to migrate their games from, say, iOS over to a browser-based environment without much hassle, making it possible to easily sell browser-based games that play the same games as apps on mobile devices.
But the real thing that should make you arch an eyebrow is Facebook. Nearly every game you can play on Facebook runs on Flash. And now Flash can run hardware-accelerated 3D, just like Real Games.
Tuesday, October 04. 2011
15 cool things Windows 8 does that Windows 7 doesn't
Via TechRadar
By Mike Williams
-----
When Microsoft released the Windows 8 Developer Preview last month it warned that it was unstable, incomplete, a very early build which has a long way to go before it's ready for release.
That doesn't sound too promising - but on installing it we were surprised to see just how many great new features Windows 8 already contained.
From the shiny new Metro interface and interesting Explorer tweaks, to new applets and major performance enhancements, Windows 8 is - even at this early stage - packed with essential functionality.
Here are 18 cool things Windows 8 does that Windows 7 doesn't
1. Boot quickly - by default
Yes, we know - every version of Windows promises boot time improvements. But this time Microsoft has really delivered.
Our test Dell Inspiron 1090 (a seriously basic laptop) took 48 seconds to launch Windows 7 from the boot loader.
Choose the Windows 8 option, though, and the Metro screen appeared in only nine seconds - more than five times faster.
How does it work? There are many tweaks, but maybe the most important happens when the system shuts down. It closes all your programs as normal, but the kernel is now hibernated, its RAM contents saved to your hard drive. This doesn't take long, and when you reboot your system can be reinitialised far faster than before.
2. Display alerts immediately
Your Windows 8 laptop won't just load faster, it'll also display useful information right away, without you having to do anything at all.
And that's because your lock screen, where you'll normally log in, can now be customised with apps which show you details on waiting emails, your schedule, RSS feeds, whatever you like.
So Windows 8 means you won't necessarily have to turn on your laptop, wait for an age as it loads, then wait even longer to launch an application, just to discover some really basic item of data: it could be available on the lock screen in seconds.
3. Log on without passwords
If you already have more than enough passwords to remember, then the good news is that Windows 8 will offer you an unusual alternative: the picture password.
You'll be able to point Windows to a picture you'd like to use, which you then click, tap or draw on with your mouse or using a touch screen. So if you choose a picture of your house, say, you might draw an outline around the roof, then tap on a window and the front door. Windows will remember your gestures, and won't allow anyone to log in later unless they can repeat them.
If that doesn't sound appealing, don't worry - you can continue to log in with a regular alphanumeric password if you prefer, just as before.

4. Enjoy a dynamic desktop
The Windows 8 Metro interface doesn't give you static shortcuts to launch its applications. Instead you get dynamic tiles, which you can change in size to reflect an app's importance, and freely organise into whatever groups best suits your needs.
And, again, these tiles aren't just used to launch the apps. They can also display information from them, so if something interesting has just appeared on an RSS feed you're watching, then you'll get to see it right away.

5. Synchronise your settings
Of course, with so much functionality on the Metro desktop, it may take a while to set it up just the way you like. But don't worry, you only have to do this once, even if you've several Windows 8 PCs, because you'll be able to synchronise your Metro apps, their settings and application histories (as well as login details for applications and websites) across all your systems, entirely automatically.
6. Spot resource hogs
All this syncing, email-checking, RSS monitoring and so on could become a little expensive if you're using a metered 3G connection, of course. So it's just as well that the new Windows 8 Task Manager includes an App History feature which can show you exactly who's hogging all your network bandwidth (as well as your CPU time, hard drive and RAM).
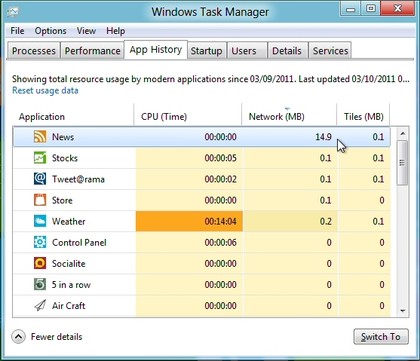
7. Close apps automatically
Traditionally Windows has left it up to you to manage the programs you run. So you can launch as many as you like, and the system won't complain: it'll just get slower, and slower, and slower as you run out of RAM and it starts swapping to disk.
Windows 8 is fortunately a little different, at least when running Metro apps. If you're running short of resources then it'll close down anything you've not used for a while, to try to help out. Don't worry, the app's state is saved first, so you don't lose anything; relaunch it and you'll carry on exactly where you left off.
8. Share easily
Sharing something you've found online is an everyday experience for most web users, and so it's great to see Microsoft build that idea into Windows 8. If you've discovered a great photo or web page in IE10 then simply hit the Share button and you'll be able to send its link via any compatible app you've installed - and they'll then update your Twitter, Facebook or other account right away.
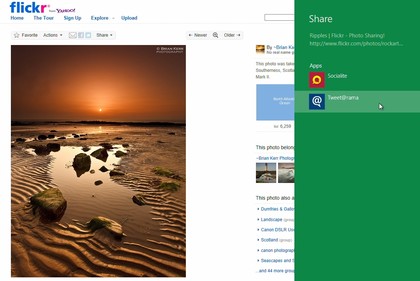
9. Work on files with ease
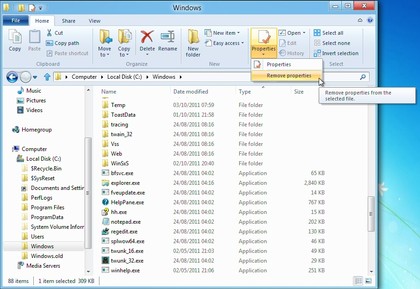
The Windows 8 Explorer now uses a ribbon-style interface, which brings many otherwise tricky to find options within very easy reach.
If you want to remove metadata containing personal information in Windows 7, for instance, you must right-click the file, select Properties, choose the Details tab, and click "Remove Properties and Personal Information".
In Windows 8, all you have to do is click the file and choose Remove Properties from the Properties list: much easier.
There are many similar shortcuts. But if they're not enough, then you can make any Explorer ribbon option even easier to access it by adding it to the Quick Access toolbar, which appears in the Explorer title bar. It'll then only ever be a couple of clicks away.
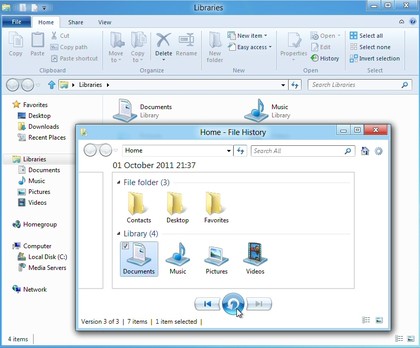
10. Back up automatically
Windows 8 includes a very easy-to-use File History feature, which can automatically back up whatever folders you like, at the frequency you specify.
This could be a complete system backup to a network drive, if you like. But it could also just save key folders like Documents and Pictures to a USB flash drive, and once you've set this up there's no further configuration required. Simply plug in the drive every few days, File History will automatically detect it, and your preferred files will automatically be backed up.
11. Download safely
Internet Explorer's SmartScreen filter is a handy technology which can check downloads against a database of known malicious sites and dangerous programs, blocking the file if it finds a match. Previously this was only available within IE, but in Windows 8 SmartScreen will be used system-wide, so you'll have an extra layer of protection no matter which browser you're using.
12. Mount ISO files
Windows 7 gained the ability to burn ISO images to disc, but if you just want to check or access their contents then Windows 8 goes one better. Just right-click the image, select Mount, and a new virtual optical drive will appear in Explorer. Double-click this to view the image contents, launch whatever programs it contains, or generally treat it just like any other disc.
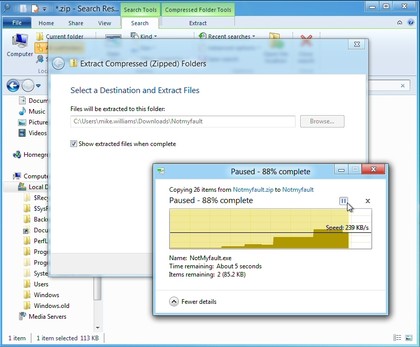
13. Pause file copies
Once you've started a Windows file copy operation, that used to be it: you had to wait until it was finished. But not any more. The new File Copy dialog includes a tiny pause button, so if you need to do something else for a moment, just click to pause the copies, click again to resume.
14. Fix problems easily
If your PC is in a bad way then you've always been able to reinstall Windows. But you'd have to find your Windows disc, first, and pay close attention to the installation options to make sure you choose the one you need.
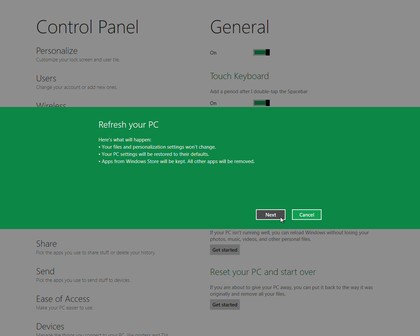
Windows 8 gets rid of all that hassle by introducing a "Refresh your PC" option (Control Panel > General). This also essentially reinstalls Windows, but there's no disc required, no complex options to consider, not even very long to wait: we've used it two or three times and it's quickly repaired any glitches we encountered.
15. Run other operating systems
If, despite all of this, you still feel that Windows 7 has some advantages - then that may not be a problem. Because Windows 8 now includes Microsoft's Client Hyper-V virtualisation platform, which allows you to install other operating systems onto virtual machines and run them on your desktop.
You will need to be running 64-bit Windows, however, and have a CPU which supports Second Level Address Translation (that's Intel's Core i3, i5 and i7 and AMD's Barcelona processors).
But if your system qualifies then you'll find this is a far better and more powerful solution than Microsoft's Virtual PC, or Windows 7's XP Mode, and should be ideal for running most legacy applications on your Windows 8 system.
Quicksearch
Popular Entries
- The great Ars Android interface shootout (131044)
- Norton cyber crime study offers striking revenue loss statistics (101656)
- MeCam $49 flying camera concept follows you around, streams video to your phone (100057)
- Norton cyber crime study offers striking revenue loss statistics (57885)
- The PC inside your phone: A guide to the system-on-a-chip (57446)





