Monday, May 14. 2012
Facebook's New App Center Promises Quality Over Quantity
Via ReadWrite
----- 
Last September, during the f8 Developers’ Conference, Facebook CTO Bret Taylor said that the company had no plans for a “central app repository” – an app store. Today, Facebook is changing its tune. The social giant has announced App Center, a section of Facebook dedicated to discovering and deploying high-quality apps on the company’s platform. The App Center will push apps to iPhone, Android and the mobile Web, giving Facebook its first true store for mobile app discovery.
The departure from Facebook’s previous company line comes as the social platform ramps up its mobile offerings to make money from its hundreds of millions of mobile users. This is not your father's app store, though.
Let's start with the requirements. Facebook has announced a strict set of style and quality guidelines to get apps placed in App Center. Apps that are considered high-quality, as decided by Facebook’s Insights analytics platform, will get prominent placement. Quality is determined by user ratings and app engagement. Apps that receive poor ratings or do not meet Facebook’s quality guidelines won't be listed.
Whether or not an app is a potential Facebook App Center candidate hinges on several factors. It must
• have a canvas page (a page that sets the app's permissions on Facebook’s platform)
• be built for iOS, Android or the mobile Web
• use a Facebook Login or be a website that uses a Facebook Login.
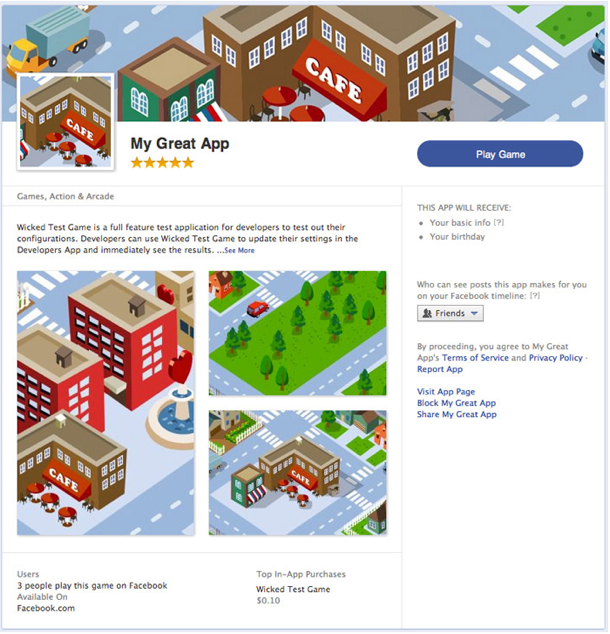
Facebook is in a tricky spot with App Center. It will house not only apps that are specifically run through its platform but also iOS and Android apps. Thus it needs to achieve a balance between competition and cooperation with some of the most powerful forces in the tech universe. If an app in App Center requires a download, the download link on the app’s detail page will bring the user to the appropriate app repository, either Apple's App Store or Android’s Google Play.
One of the more interesting parts of App Center is that Facebook will allow paid apps. This is a huge move for Facebook as it provides a boost to its Credits payment service. One of the benefits of having a store is that whoever controls the store also controls transactions arising from the items in it, whether payments per download or in-app purchases. This will go a long way towards Facebook’s goal of monetizing its mobile presence without relying on advertising.

Facebook App Center Icon Guidelines
Developers interested in publishing apps to Facebook’s App Center should take a look at both the guidelines and the tutorial that outlines how to upload the appropriate icons, how to request permissions, how to use Single Sign On (SSO, a requirement for App Center) and the app detail page.
This is a good move for Facebook. It will give the company several
avenues to start making money off of mobile but also strengthen its
position as one of the backbones of the Web. For instance, App Center is
both separate from iOS and Android but also a part of it. Through App
Center, Facebook can direct traffic to its apps, monitor who and how
users are downloading applications and keep itself at the center of the
user experience.
Friday, March 30. 2012
EU Votes To Lower Mobile Roaming Charges
Via CIO TODAY
-----
Business travelers -- and the enterprises that foot their phone bills -- have been complaining about high roaming fees in Europe for years. Now, some relief is finally in sight.
Indeed, both data roaming and phone calls travelers make while doing business (or taking a vacation) in Europe should be much cheaper this summer thanks to a deal done in the European Parliament this week.
Members of the European Parliament and the Danish Presidency of the Council of Ministers agreed to lower price caps on roaming. Parliament as a whole still needs to approve the deal. But if all runs smoothly the new rules will take effect July 1.
"I am satisfied that the Council approved Parliament's approach to tackle very high prices of phone calls, SMS and in particular of data roaming," said Angelika Niebler of Germany, Parliament's reporter for the draft legislation. "The proposed price caps ensure a sufficient margin between wholesale and retail prices to assure a level of competition that will enable new players to enter the market."
How Low Do They Go?
The agreement increases transparency and consumer protection to prevent bill shocks, Niebler said. That means European Union consumers no longer need to worry about accidentally running up huge bills when using their mobile devices both within and outside the EU. Of course, it's also a boon for consumers from other nations traveling to Europe.
How much savings are we talking about? According to the new rules, a downloaded megabyte would cost no more than 70 cents. That cost drops down to 45 cents in 2013 and 20 cents by July 2014. This is a big improvement, seeing as there is currently no price ceiling for mobile data services charged to consumers.
On the phone call front, the cost of a one-minute call would not exceed 29 cents under the new rules. That declines to 19 cents as of July 2014. That's down from 35 cents under the current legislation. Finally, an SMS would cost no more than 9 cents. That drops to 6 cents as by July 2014 and marks an 11 percent cut from current costs.
Nixing Roaming Altogether
"Mobile roaming charges in the EU are artificially high. Given the fact that they are trying to treat the entire continent like a single country, I don't understand why mobile roaming charges are so high between countries," said Mike Disabato, managing vice president of network and telecom at Gartner.
Practically speaking, the new rules mean that you only need one SIM card while traveling in Europe. Of course, you can't get a SIM card on an iPhone unless you buy an unlocked phone for $800. But if you do use a SIM card you will not have to change phone numbers every time you go to a different country.
"The new rules will make it a lot cheaper for people who actually have to do business in Europe. Any time you start reducing these types of rates it's a good thing," Disabato said. "We got rid of roaming charges a long time ago. It's about time they go in Europe. It will take until the EU decides they are going to make it happen."Wednesday, March 28. 2012
Anatomy of a leak: how iPhones spill the ID of networks they access
Via ars technica
-----
An Ars story from earlier this month reported that iPhones expose the unique identifiers of recently accessed wireless routers, which generated no shortage of reader outrage. What possible justification does Apple have for building this leakage capability into its entire line of wireless products when smartphones, laptops, and tablets from competitors don't? And how is it that Google, Wigle.net, and others get away with publishing the MAC addresses of millions of wireless access devices and their precise geographic location?
Some readers wanted more technical detail about the exposure, which applies to three access points the devices have most recently connected to. Some went as far as to challenge the validity of security researcher Mark Wuergler's findings. "Until I see the code running or at least a youtube I don't believe this guy has the goods," one Ars commenter wrote.
According to penetration tester Robert Graham, the findings are legit.
In the service of our readers, and to demonstrate to skeptics that the privacy leak is real, Ars approached Graham and asked him to review the article for accuracy and independently confirm or debunk Wuergler's findings.
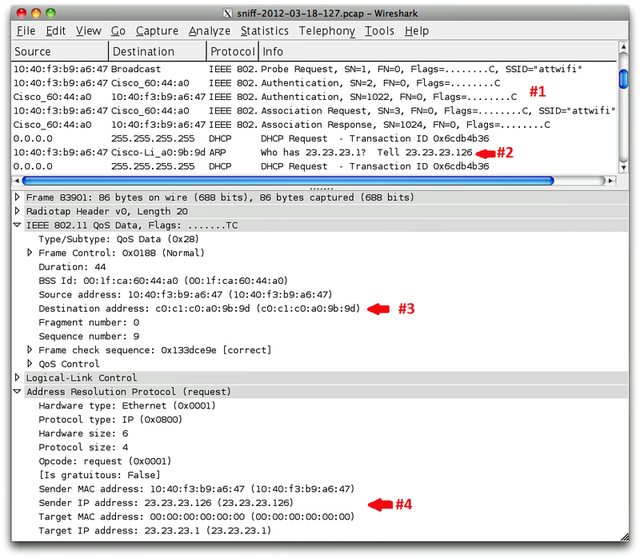
"I can confirm all the technical details of this 'hack,'" Graham, who is CEO of Errata Security, told Ars via e-mail. "Apple products do indeed send out three packets that will reveal your home router MAC address. I confirmed this with my latest iPad 3."
He provided the image at the top of this post as proof. It shows a screen from Wireshark, a popular packet-sniffing program, as his iPad connected to a public hotspot at a Starbucks in Atlanta. Milliseconds after it connected to an SSID named "attwifi" (as shown in the section labeled #1), the iPad broadcasted the MAC address of his Linksys home router (shown in the section labeled #2). In section #3, the iPad sent the MAC address of this router a second time, and curiously, the identifier was routed to this access point even though it's not available on the local network. As is clear in section #4, the iPad also exposed the local IP address the iPad used when accessing Graham's home router. All of this information is relatively simple to view by anyone within radio range.
The image is consistent with one provided by Wuergler below. Just as Wuergler first claimed, it shows an iPhone disclosing the last three access points it has connected to.

Graham used Wireshark to monitor the same Starbucks hotspot when he connected with his Windows 7 laptop and Android-based Kindle Fire. Neither device exposed any previously connected MAC addresses. He also reviewed hundreds of other non-Apple devices as they connected to the network, and none of them exposed previously accessed addresses, either.
As the data makes clear, the MAC addresses were exposed in ARP (address resolution protocol) packets immediately after Graham's iPad associated with the access point but prior to it receiving an IP address from the router's DHCP server. Both Graham and Wuergler speculate that Apple engineers intentionally built this behavior into their products as a way of speeding up the process of reconnecting to access points, particularly those in corporate environments. Rather than waiting for a DHCP server to issue an IP address, the exposure of the MAC addresses allows the devices to use the same address it was assigned last time.
"This whole thing is related to DHCP and autoconfiguration (for speed and less traffic on the wire)," Wuergler told Ars. "The Apple devices want to determine if they are on a network that they have previously connected to and they send unicast ARPs out on the network in order to do this."
Indeed, strikingly similar behavior was described in RFC 4436, a 2006 technical memo co-written by developers from Apple, Microsoft, and Sun Microsystems. It discusses a method for detecting network attachment in IPv4-based systems.
"In this case, the host may determine whether it has re-attached to the logical link where this address is valid for use, by sending a unicast ARP Request packet to a router previously known for that link (or, in the case of a link with more than one router, by sending one or more unicast ARP Request packets to one or more of those routers)," the document states at one point. "The ARP Request MUST use the host MAC address as the source, and the test node MAC address as the destination," it says elsewhere.
Of course, only Apple engineers can say for sure if the MAC disclosure is intentional, and representatives with the company have declined to discuss the issue with Ars. What's more, if RFC 4436 is the reason for the behavior, it's unclear why there's no evidence of Windows and Android devices doing the same thing. If detecting previously connected networks is such a good idea, wouldn't Microsoft and Google want to design their devices to do it, too?
In contrast to the findings of Graham and Wuergler were those of Ars writer Peter Bright, who observed different behavior when his iPod touch connected to a wireless network. While the Apple device did expose a MAC address, the unique identifier belonged to the Ethernet interface of his router rather than the MAC address of the router's WiFi interface, which is the identifier cataloged by Google, Skyhook, and similar databases.
Bright speculated that many corporate networks likely behave the same way. And for Apple devices that connect to access points with such configurations, exposure of the MAC address may pose less of a threat. Still, while it's unclear what percentage of wireless routers assign a different MAC address to wired and wireless interfaces, Graham and Wuergler's tests show that at least some wireless routers by default make no such distinction.
Wuergler also debunked a few other misconceptions that some people had about the wireless behavior of Apple devices. Specifically, he said claims that iPhones don't broadcast the SSID they are looking for from Errata Security's Graham are incorrect. Some Ars readers had invoked the 2010 blog post from Graham to cast doubt on Wuergler's findings
"The truth is Apple products do probe for known SSIDs (and no, there is no limit as to how many)," Wuergler wrote in a post published on Friday to the Daily Dave mailing list. He included the following screenshot to document his claim.
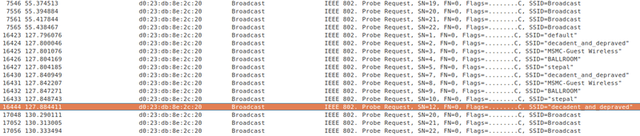
Connecting the dots
What all of this means is that there's good reason to believe that iPhones and other Apple products—at least when compared to devices running Windows or Android—are unique in leaking MAC addresses that can uniquely identify the locations of networks you've connected to recently. When combined with other data often exposed by virtually all wireless devices—specifically the names of wireless networks you've connected to in the past—an attacker in close proximity of you can harvest this information and use it in targeted attacks.
Over the past year or so, Google and Skyhook have taken steps to make it harder for snoops to abuse the GPS information stored in their databases. Google Location Services, for instance, now requires the submission of two MAC addresses in close proximity of each other before it will divulge where they are located. In many cases, this requirement can be satisfied simply by providing one of the other MAC addresses returned by the Apple device. If it's within a few blocks of the first one, Google will readily provide the data. It's also feasible for attackers to use war dialing techniques to map the MAC addresses of wireless devices in a given neighborhood or city.
Since Apple engineers are remaining mum, we can only guess why iDevices behave the way they do. What isn't in dispute is that, unlike hundreds of competing devices that Wuergler and Graham have examined, the Apple products leak connection details many users would prefer to keep private.
A video demonstrating the iPhone's vulnerability to fake access point attacks is here.
Updated to better describe video.Image courtesy of Robert Graham, Errata Security
Tuesday, March 27. 2012
TI Demos OMAP5 WiFi Display Mirroring on Development Platform
Via AnandTech
-----

On our last day at MWC 2012, TI pulled me aside for a private demonstration of WiFi Display functionality they had only just recently finalized working on their OMAP 5 development platform. The demo showed WiFi Display mirroring working between the development device’s 720p display and an adjacent notebook which was being used as the WiFi Display sink.
TI emphasized that what’s different about their WiFi Display implementation is that it works using the display framebuffer natively and not a memory copy which would introduce delay and take up space. In addition, the encoder being used is the IVA-HD accelerator doing the WiFi Display specification’s mandatory H.264 baseline Level 3.1 encode, not a software encoder running on the application processor. The demo was running mirroring the development tablet’s 720p display, but TI says they could easily do 1080p as well, but would require a 1080p framebuffer to snoop on the host device. Latency between the development platform and display sink was just 15ms - essentially one frame at 60 Hz.
The demonstration worked live over the air at TI’s MWC booth and also used a WiLink 8 series WLAN combo chip. There was some stuttering, however this is understandable given the fact that this demo was using TCP (live implementations will use UDP) and of course just how crowded 2.4 and 5 GHz spectrum is at these conferences. In addition, TI collaborated with Screenovate for their application development and WiFi Display optimization secret sauce, which I’m guessing has to do with adaptive bitrate or possibly more.
Enabling higher than 480p software encoded WiFi Display is just one more obvious piece of the puzzle which will eventually enable smartphones and tablets to obviate standalone streaming devices.
-----
Personal Comment:
Kind of obvious and interesting step forward as it is more and more requested by mobile devices users to be able to beam or 'to TV' mobile device's screens... which should lead to transform any (mobile) device in a full-duplex video broadcasting enabled device (user interaction included!) ... and one may then succeed in getting rid of some cables in the same sitting?!
Monday, March 26. 2012
New Samsung sensor captures image, depth simultaneously
Via electronista
-----
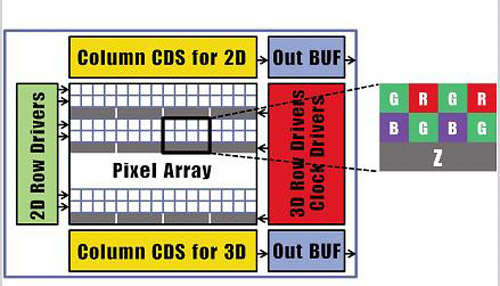
Samsung has developed a new camera sensor technology that offers the ability to simultaneously capture image and depth. The breakthrough could potentially be applied to smartphones and other devices as an alternative method of control where hand gestures could be used to carry out functions without having to touch a screen or other input. According to Tech-On, it uses a CMOS sensor with red, blue and green pixels, combined with an additional z-pixel for capturing depth.
The
new Samsung sensor can capture images at a resolution of 1,920x720
using its traditional RGB array, while it can also capture a depth image
at a resolution of 480x360 with the z-pixel. It is able to achieve its
depth capabilities by a special process whereby the z-pixel is located
beneath the RGB pixel array. Samsung’s boffins then placed a special
barrier between the RGB and z pixels allowing the light they capture to
give the effect that the z-pixel is three times its actual size.
In this early iteration of the new technology, Samsung used FSI
technology only. In future applications, BSI could be applied doubling
the quantum efficiency of the design further reducing cross-talk to the
RGB pixels.
-----
Personal Comment:
Some additional information on BSI (Backside illumination)/FSI (Frontside Illumination):
Wednesday, March 21. 2012
World’s First Flying File-Sharing Drones in Action
Via TorrentFreak
-----
A few days ago The Pirate Bay announced that in future parts of its site could be hosted on GPS controlled drones. To many this may have sounded like a joke, but in fact these pirate drones already exist. Project “Electronic Countermeasures” has built a swarm of five fully operational drones which prove that an “aerial Napster” or an “airborne Pirate Bay” is not as futuristic as it sounds.
 In an ever-continuing effort to thwart censorship, The Pirate Bay plans to turn flying drones into mobile hosting locations.
In an ever-continuing effort to thwart censorship, The Pirate Bay plans to turn flying drones into mobile hosting locations.
“Everyone knows WHAT TPB is. Now they’re going to have to think about WHERE TPB is,” The Pirate Bay team told TorrentFreak last Sunday, announcing their drone project.
Liam Young, co-founder of Tomorrow’s Thoughts Today, was amazed to read the announcement, not so much because of the technology, because his group has already built a swarm of file-sharing drones.
“I thought hold on, we are already doing that,” Young told TorrentFreak.
Their starting point for project “Electronic Countermeasures” was to create something akin to an ‘aerial Napster’ or ‘airborne Pirate Bay’, but it became much more than that.
“Part nomadic infrastructure and part robotic swarm, we have rebuilt and programmed the drones to broadcast their own local Wi-Fi network as a form of aerial Napster. They swarm into formation, broadcasting their pirate network, and then disperse, escaping detection, only to reform elsewhere,” says the group describing their creation.
File-Sharing Drone in Action (photo by Claus Langer)

In short the system allows the public to share data with the help of flying drones. Much like the Pirate Box, but one that flies autonomously over the city.
“The public can upload files, photos and share data with one another as the drones float above the significant public spaces of the city. The swarm becomes a pirate broadcast network, a mobile infrastructure that passers-by can interact with,” the creators explain.
One major difference compared to more traditional file-sharing hubs is that it requires a hefty investment. Each of the drones costs 1500 euros to build. Not a big surprise, considering the hardware that’s needed to keep these pirate hubs in the air.
“Each one is powered by 2x 2200mAh LiPo batteries. The lift is provided by 4x Roxxy Brushless Motors that run off a GPS flight control board. Also on deck are altitude sensors and gyros that keep the flight stable. They all talk to a master control system through XBee wireless modules,” Young told TorrentFreak.
“These all sit on a 10mm x 10mm aluminum frame and are wrapped in a vacuum formed aerodynamic cowling. The network is broadcast using various different hardware setups ranging from Linux gumstick modules, wireless routers and USB sticks for file storage.”
For Young and his crew this is just the beginning. With proper financial support they hope to build more drones and increase the range they can cover.
“We are planning on scaling up the system by increasing broadcast range and building more drones for the flock. We are also building in other systems like autonomous battery change bases. We are looking for funding and backers to assist us in scaling up the system,” he told us.
Those who see the drones in action (video below) will notice that they’re not just practical. The creative and artistic background of the group shines through, with the choreography performed by the drones perhaps even more stunning than the sharing component.
“When the audience interacts with the drones they glow with vibrant colors, they break formation, they are called over and their flight pattern becomes more dramatic and expressive,” the group explains.
Besides the artistic value, the drones can also have other use cases than being a “pirate hub.” For example, they can serve as peer-to-peer communications support for protesters and activists in regions where Internet access is censored.
Either way, whether it’s Hollywood or a dictator, there will always be groups that have a reason to shoot the machines down. But let’s be honest, who would dare to destroy such a beautiful piece of art?
Electronic Countermeasures @ GLOW Festival NL 2011 from liam young on Vimeo.
Thursday, February 16. 2012
Google Sky Map development ends, app goes open source
-----
If you’re a fan of Google’s augmented reality astronomy app Google Sky Map, I’ve got good news and bad news for you. Google announced that major development on the app has ended, so there will be no more major official releases from the company. On the plus side, they’ve decided to release the open-source code for Sky Map, so given enough developer interest it should be around for quite some time.

Sky Map started as one of Google’s famous 20% projects, which six of its employees launched by working in their company-sponsored spare time. The application was one of Android’s first showpiece apps, combining basic astronomical data overlaid on a smartphone camera to easily identify constellations, planets and other heavenly bodies by simply pointing the phone towards the sky. The free app has been downloaded over 10 million times from the Android Market.
Google is working with Carnegie Melon University so that its students can continue direct development. The company didn’t say if direct updated with computer scientist students’ code would make it into the android Market, but it’s a pretty safe bet. If you’ d like to give it a try for yourself, you can download the open-source code here. I fully expect a Star Trek themed version of Sky Map in the next few weeks which will allow me to view the Alpha Quadrant from my smartphone – get to it, devs.
Tuesday, January 31. 2012
Build Up Your Phone’s Defenses Against Hackers
-----
Chuck Bokath would be terrifying if he were not such a nice guy. A jovial senior engineer at the Georgia Tech Research Institute in Atlanta, Mr. Bokath can hack into your cellphone just by dialing the number. He can remotely listen to your calls, read your text messages, snap pictures with your phone’s camera and track your movements around town — not to mention access the password to your online bank account.
And while Mr. Bokath’s job is to expose security flaws in wireless devices, he said it was “trivial” to hack into a cellphone. Indeed, the instructions on how to do it are available online (the link most certainly will not be provided here). “It’s actually quite frightening,” said Mr. Bokath. “Most people have no idea how vulnerable they are when they use their cellphones.”
Technology experts expect breached, infiltrated or otherwise compromised cellphones to be the scourge of 2012. The smartphone security company Lookout Inc. estimates that more than a million phones worldwide have already been affected. But there are ways to reduce the likelihood of getting hacked — whether by a jealous ex or Russian crime syndicate — or at least minimize the damage should you fall prey.
As cellphones have gotten smarter, they have become less like phones and more like computers, and thus susceptible to hacking. But unlike desktop or even most laptop computers, cellphones are almost always on hand, and are often loaded with even more personal information. So an undefended or carelessly operated phone can result in a breathtaking invasion of individual privacy as well as the potential for data corruption and outright theft.
“Individuals can have a significant impact in protecting themselves from the kind of fraud and cybercrimes we’re starting to see in the mobile space,” said Paul N. Smocer, the president of Bits, the technology policy division of the Financial Services Roundtable, an industry association of more than 100 financial institutions.
Cellphones can be hacked in several ways. A so-called man-in-the-middle attack, Mr. Bokath’s specialty, is when someone hacks into a phone’s operating system and reroutes data to make a pit stop at a snooping third party before sending it on to its destination.
That means the hacker can listen to your calls, read your text messages, follow your Internet browsing activity and keystrokes and pinpoint your geographical location. A sophisticated perpetrator of a man-in-the-middle attack can even instruct your phone to transmit audio and video when your phone is turned off so intimate encounters and sensitive business negotiations essentially become broadcast news.
How do you protect yourself? Yanking out your phone’s battery is about the only way to interrupt the flow of information if you suspect you are already under surveillance. As for prevention, a common ruse for making a man-in-the middle attack is to send the target a text message that claims to be from his or her cell service provider asking for permission to “reprovision” or otherwise reconfigure the phone’s settings due to a network outage or other problem. Don’t click “O.K.” Call your carrier to see if the message is bogus.
For added security, Mr. Bokath uses a prepaid subscriber identity module, or SIM, card, which he throws away after using up the line of credit. A SIM card digitally identifies the cellphone’s user, not only to the cellphone provider but also to hackers. It can take several months for the cellphone registry to associate you with a new SIM. So regularly changing the SIM card, even if you have a contract, will make you harder to target. They are not expensive (about $25 for 50 of them on eBay). This tactic works only if your phone is from AT&T or T-Mobile, which support SIM cards. Verizon and Sprint do not. Another way hackers can take over your phone is by embedding malware, or malicious software, in an app. When you download the app, the malware gets to work corrupting your system and stealing your data. Or the app might just be poorly designed, allowing hackers to exploit a security deficiency and insert malware on your phone when you visit a dodgy Web site or perhaps click on nefarious attachments or links in e-mails. Again, treat your cellphone as you would a computer. If it’s unlikely Aunt Beatrice texted or e-mailed you a link to “Great deals on Viagra!”, don’t click on it.
Since apps are a likely vector for malware transmission on smartphones, Roman Schlegel, a computer scientist at City University of Hong Kong who specializes in mobile security threats, advised, “Only buy apps from a well-known vendor like Google or Apple, not some lonely developer.”
It’s also a good idea to read the “permissions” that apps required before downloading them. “Be sure the permissions requested make sense,” Mr. Schlegel said. “Does it make sense for an alarm clock app to want permission to record audio? Probably not.” Be especially wary of apps that want permission to make phone calls, connect to the Internet or reveal your identity and location.
The Google Android Market, Microsoft Windows Phone Marketplace, Research in Motion BlackBerry App World and Appstore for Android on Amazon.com all disclose the permissions of apps they sell. The Apple iTunes App Store does not, because Apple says it vets all the apps in its store.
Also avoid free unofficial versions of popular apps, say, Angry Birds or Fruit Ninja. They often have malware hidden in the code. Do, however, download an antivirus app like Lookout, Norton and AVG. Some are free. Just know that security apps screen only for viruses, worms, Trojans and other malware that are already in circulation. They are always playing catch-up to hackers who are continually developing new kinds of malware. That’s why it’s important to promptly download security updates, not only from app developers but also from your cellphone provider.
Clues that you might have already been infected include delayed receipt of e-mails and texts, sluggish performance while surfing the Internet and shorter battery life. Also look for unexplained charges on your cellphone bill.
As a general rule it is safer to use a 3G network than public Wi-Fi. Using Wi-Fi in a Starbucks or airport, for example, leaves you open to hackers shooting the equivalent of “gossamer threads into your phone, which they use to reel in your data,” said Martin H. Singer, chief executive of Pctel, a company in Bloomingdale, Ill., that provides wireless security services to government and industry.
If that creepy image tips you into the realm of paranoia, there are supersecure smartphones like the Sectéra Edge by General Dynamics, which was commissioned by the Defense Department for use by soldiers and spies. Today, the phone is available for $3,000 only to those working for government-sponsored entities, but it’s rumored that the company is working to provide something similar to the public in the near future. General Dynamics did not wish to comment.
Georgia Tech Research Institute is taking a different tack by developing software add-on solutions to make commercially available phones as locked-down as those used by government agents.
Michael Pearce, a mobile security consultant with Neohapsis in Chicago, said you probably did not need to go as far as buying a spy phone, but you should take precautions. “It’s like any arms race,” he said. “No one wins, but you have to go ahead and fight anyway.”
Monday, January 30. 2012
What happened to innovative games?
Via #AltDevBlogADay
-----
Indie developer Nimblebit dropped a PR bomb on Zynga yesterday
with it’s letter addressing the similarities between their hit iPhone
game Tiny Tower and Zynga’s upcoming release, Dream Heights. This
galvanized the gaming community, with thousands of people, from prominent bloggers to gamers on Reddit criticizing the company.
However, just after the new year, Atari ordered the removal of Black Powder Media’s Vector Tanks, a game strongly inspired by Atari’s Battlezone. This galvanized the community in a similar way, except this time, gamers were furious that Atari shut down an indie game company that made an extremely similar game.
Unfortunately, the line between inspiration and copying is incredibly blurry at best. The one thing that’s certain is that copying is here to stay. Copying has been present in some form since the dawn of capitalism (if you need proof, just go to the toothpaste isle of your local supermarket). The game industry is no stranger to this trend: game companies have been copying each other for years. Given it’s repeated success, there’s little reason to think that this practice will stop. Indie flash game studio XGEN Studios posted a response to Nimblebit, showing that their hit games were also copied:
Some would even argue that the incredibly successful iOS game Angry Birds was a copy of the popular Armor Games flash game, Crush the Castle, but then Crush the Castle was inspired by others that game before it. Social games even borrow many of their game mechanics from slot machines to increase retention. So what is copying, or more importantly, which parts of it are moral and immoral? Everyone seems to have a different answer, but it’s safe to say that people always copy the most successful ideas. The one thing that those in the Zynga-Nimblebit conversation seems to have overlooked is that everyone copies others in some way.
Of course, while imitation may be the sincerest form of flattery, it doesn’t feel good to be imitated when a competitor comes after your users. In this case, people may question Zynga’s authenticity and make a distinction between inspiration and outright duplication. But at the same time, Zynga’s continued success with the “watch, then replicate” model shows that marketing, analytics, and operations can improve on an existing game concept. Or just give them the firepower to beat out the original game, depending on how you look at it.
Friday, January 20. 2012
Did Google ever have a plan to curb Android fragmentation?
Via ZDNet
-----

Another day, another set of Android fragmentation stories. And while there’s no doubt that there is wide fragmentation within the platform, and there’s not real solution in sight, I’m starting to wonder if Google ever had a plan to prevent the platform for becoming a fragmented mess.
How bad’s the problem? Jon Evans over on TechCrunch tells it like it is:
OS fragmentation, though, is an utter disaster. Ice Cream Sandwich is by all accounts very nice; but what good does that do app developers, when according to Google’s own stats, 30% of all Android devices are still running an OS that is 20 months old?
…
More than two-thirds of iOS users had upgraded to iOS 5 a mere three months after its release. Anyone out there think that Ice Cream Sandwich will crack the 20% mark on Google’s platform pie chart by March?
He then goes on to deliver the killer blow:
OS fragmentation is the single greatest problem Android faces, and it’s only going to get worse. Android’s massive success over the last year mean that there are now tens if not hundreds of millions of users whose handset manufacturers and carriers may or may not allow them to upgrade their OS someday; and the larger that number grows, the more loath app developers will become to turn their back on them. That unwillingness to use new features means Android apps will fall further and further behind their iOS equivalents, unless Google manages – via carrot, stick, or both – to coerce Android carriers and manufacturers to prioritize OS upgrades.
And that’s the core problem with Android. While there’s no doubt that consumers who’ve bought Android devices are being screwed out of updates that they deserve (the take up of Android 4.0 ‘Ice Cream Sandwich’ is pretty poor so far), the biggest risk from fragmentation is that developers will ignore new Android features an instead focus on supporting older but more mainstream feature sets. After all, developers want to hit the masses, not the fringes. Also, the more platforms developers have to support, the more testing work there is.
OK, so Android is fragmented, and it’s a problem that Google doesn’t seem willing to tackle. But the more I look at the Android platform and the associated ecosystem, it makes me wonder if Google ever had any plan (or for that matter intention) to control platform fragmentation.
But could Google have done anything to control fragmentation? Former Microsoftie (and now investor) Charlie Kindel thinks there no hope to curb fragmentation. In fact, he believes that most things will make it worse. I disagree with Kindel on this matter. He also believes that Google’s current strategy amounts to little more that wishing that everyone will upgrade. On this point we are in total agreement.
I disagree with Kindel that that there’s nothing that Google can do to at least try to discourage fragmentation. I believe that one of Google’s strongest cards are Android users themselves. Look at how enthusiastic iPhone and iPad owners are about iOS updates. They’re enthusiastic because Apple tells them why they should be enthusiastic about new updates. Compare this to Google’s approach to Android customers. Google (or anyone else in the chain for that matter) doesn’t seem to be doing much to get people fired up and enthusiastic about Android. In fact, it seems to me the only message being given to Android customers is ‘buy another Android handset.’
I understand that Google isn’t Apple and can’t seem to sway the crowds in the same way, but it might start to help if the search giant seemed to care about the OS. The absence of enthusiasm make the seem Sphinx-like and uncaring. Why should anyone care about new Android updates when Google itself doesn’t really seem all that excited? If Google created a real demand for Android updates from the end users, this would put put pressure on the handset makers and the carriers to get updates in a timely fashion to users.
Make the users care about updates, and the people standing in the way of those updates will sit up and pay attention to things.
Personal comment:
Google with Android OS is now in a similar place than Microsoft with Windows, and blaming Google to have this disparity of OS versions would be the same than blaming Microsoft on the fact that Windows XP, Windows Vista and Windows 7 are still co-existing nowadays. One reason Android got that 'fragged' is that it has to face a rapid evolution of hardware and new kind of devices in a very short time, somehow having a kind of Frankenstein-like experience with its Android creature. Many distinct hardware manufacturers adopt Android, develop their own GUI layer on top of it, making Google having a direct control on the spread of new Android version quite impossible... as each manufacturer may need to perform their own code update prior to propose a new version of Android on their own devices.
The direct comparison with iOS is a kind of unfair as Apple do have a rapid update cycle by controlling every single workings of the overall mechanism: SDK regular updates push developers to adopt new features and forget about old iOS versions and new iDevice's Apps request the end-user to upgrade their iOS version to the last one in order to be able to install new Apps. Meanwhile, Apple is having control on hardware design, production and evolution too, making the propagation of new iOS versions much easier and much faster than it is for Google with Android.
Then, mobile devices (smartphones or tablets) do have a short life timeline and this was already true prior Google and Apple starts acting in this market. So whatever your name is Google or Apple, considering not proposing the very last version of your OS on so-called 'old' or obsolete hardware is a kind of an obvious choice to do. This is not even a 'choice' but more a direct consequence of how fast technology is evolving nowadays.
Now, smartphones and tablets hardware capabilities will reach a 'standard' level to become 'mature' products (all smartphones/tablets do have cameras, video capabilities, editing capabilities etc...) which may make easier for Android to spread over on all devices in a similar version while hardware evolution observes a pause. Already Apple's last innovations are more linked to software than real hardware (r)evolution, so Android may take benefit of this in order to reduce the gap.
Quicksearch
Popular Entries
- The great Ars Android interface shootout (131078)
- Norton cyber crime study offers striking revenue loss statistics (101710)
- MeCam $49 flying camera concept follows you around, streams video to your phone (100096)
- Norton cyber crime study offers striking revenue loss statistics (57939)
- The PC inside your phone: A guide to the system-on-a-chip (57518)
Categories
Show tagged entries
Syndicate This Blog
Calendar
|
|
March '26 | |||||
| Mon | Tue | Wed | Thu | Fri | Sat | Sun |
| 1 | ||||||
| 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 | 21 | 22 |
| 23 | 24 | 25 | 26 | 27 | 28 | 29 |
| 30 | 31 | |||||


