
Monday, April 28. 2014
‘Electronic skin' equipped with memory
Via Nature
-----

Donghee Son and Jongha Lee - Wearable sensors have until now been unable to store data locally.
Researchers have created a wearable device that is as thin as a temporary tattoo and can store and transmit data about a person’s movements, receive diagnostic information and release drugs into skin.
Similar efforts to develop ‘electronic skin’ abound, but the device is the first that can store information and also deliver medicine — combining patient treatment and monitoring. Its creators, who report their findings today in Nature Nanotechnology1, say that the technology could one day aid patients with movement disorders such as Parkinson’s disease or epilepsy.
The researchers constructed the device by layering a package of stretchable nanomaterials — sensors that detect temperature and motion, resistive RAM for data storage, microheaters and drugs — onto a material that mimics the softness and flexibility of the skin. The result was a sticky patch containing a device roughly 4 centimetres long, 2 cm wide and 0.3 millimetres thick, says study co-author Nanshu Lu, a mechanical engineer at the University of Texas in Austin.
“The novelty is really in the integration of the memory device,” says Stéphanie Lacour, an engineer at the Swiss Federal Institute of Technology in Lausanne, who was not involved in the work. No other device can store data locally, she adds.
The trade-off for that memory milestone is that the device works only if it is connected to a power supply and data transmitter, both of which need to be made similarly compact and flexible before the prototype can be used routinely in patients. Although some commercially available components, such as lithium batteries and radio-frequency identification tags, can do this work, they are too rigid for the soft-as-skin brand of electronic device, Lu says.
Even if softer components were available, data transmitted wirelessly would need to be converted into a readable digital format, and the signal might need to be amplified. “It’s a pretty complicated system to integrate onto a piece of tattoo material,” she says. “It’s still pretty far away.”
Friday, April 25. 2014
Bionic Olympics to be hosted in 2016
Via BBC
-----

Totally paralysed people will be able to take part, using a brain-computer interface
The first Cybathlon, an Olympics for bionic athletes, will take place in Switzerland in October 2016.
The event will include a race where competitors control an avatar via a brain interface.
There will also be races for competitors wearing prosthetic limbs and exo-skeletons.
Hosted by the Swiss National Competence Center of Research, it is hoped the competition will spur interest in human performance-enhancing technology.
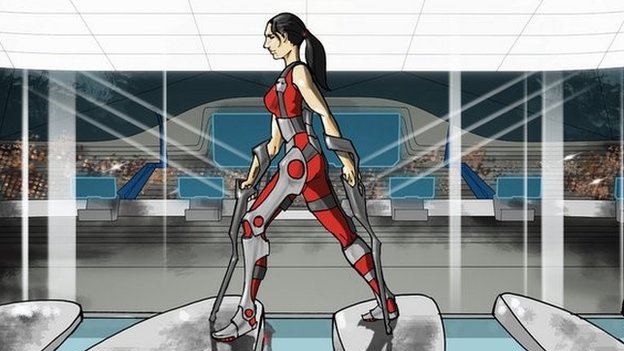
More people are walking again thanks to exo-skeletons
The brain-computer interface race is designed for competitors who are paralysed from the neck down. They will control an avatar in a computer racing game via a headset that connects the brain to a computer.
There will also be races for those wearing arm or leg prosthetics, an exoskeleton race and a wheelchair race.
The assistive devices worn by the athletes, who will be known as pilots, can either be ones that are already commercially available or prototypes from research labs.
There will be two medals for each competition, one for the pilot and one for company that developed the device.

There will also be a wheelchair race
Bionic limbs and exoskeletons are becoming much more technically advanced, offering those wearing them much more realistic movements.
Prof Hugh Herr, from the Massachusetts Institute of Technology, showed off some of the prosthetics that his team have been working on at the Ted (Technology, Entertainment and Design) conference in Vancouver last week.
He is currently in negotiations with health care professionals to get the bionic limbs more widely available to those who need them.
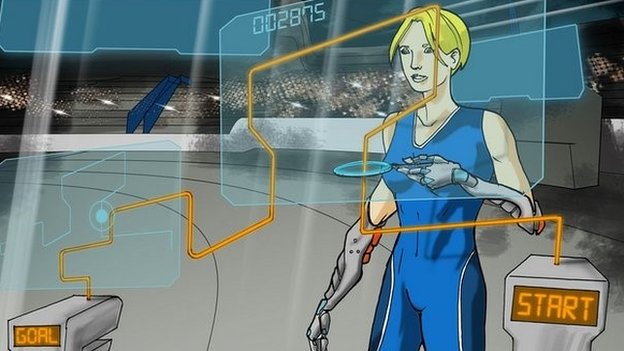
Pilots with arm prosthetics will be able to compete
Often though there was a disconnect between technology and patients, said Prof Robert Riener, event organiser, from the University of Switzerland.
"The idea is that we want to push development of assistive technologies towards devices that patients can really use in everyday life," he told the BBC.
"Some of the current technologies look very fancy but are a long way from being practical and user-friendly," he added.
The other main aim of the games is to allow people to compete who have never had the opportunity before.
"We allow technology that has previously been excluded from the Paralympics. By making it a public event we want to get rid of the borders between patients, society and the technology community," Prof Riener said.
Thursday, April 24. 2014
Giant photoshop eraser sticks to london streets
Via designboom
-----

two creatives behind the ‘street eraser‘ blog are merging the digital world with the analog, sticking their adobe-inspired art throughout london’s urban fabric. the giant playful labels illustrate the familiar grey and white checkerboard pattern, visible when using the eraser tool in photoshop. eliminating graffitti from traffic signs, color from mailboxes and portions of billboards, the intervention seemingly reveals a concealed world beneath our own. the team says of the digital tool interrupting everyday surroundings, ‘we rather like the idea that it’s hiding under the surface of everything around us.’




Smile! New tech creates 3D mug shots from DNA
Via Tech Times
-----

Virtual 3D faces can now be produced from DNA code. The application,
developed by Mark Shriver of Pennsylvania State University, produces a
virtual mug shot of potential criminals. Pictured here is a work flow
diagram showing how facial features were processed for the application.
(Photo : PLOS ONE)
Models of a criminal's face may so be generated from any trace of DNA left at the scene of a crime. Computer-generated 3D maps will show exactly how the suspect would have looked from an angle.
Mark Shriver of Pennsylvania State University and his team developed the application, which produces a virtual mug shot of potential criminals.
Shriver and his team took 3D images of almost 600 volunteers, coming from a wide range of racial and ethnic groups. They superimposed more than 7,000 digital points of reference on the facial features and recorded the exact position of each of those markers. These grids were used to measure how the facial features of a subject differ from the norm. For instance, they would quantify the distance between the eyes of a subject, and record how much more narrow or wide they were than average.
A computer model was created to see how facial features were affected by sex, genes and race. Each of the study participants were tested for 76 genetic variants that cause facial mutations. Once corrected for race and sex, 20 genes with 24 variants appeared to reliably predict facial shape.
"Results on a set of 20 genes showing significant effects on facial features provide support for this approach as a novel means to identify genes affecting normal-range facial features and for approximating the appearance of a face from genetic markers," the researchers wrote in the article announcing the results.
As part of data collection, the team asked participants to rate faces based on perceived ethnicity, as well as gender.
Digital facial reconstructions from DNA have proven to be notoriously unreliable. Even seemingly simple information like height can be difficult to determine through genetic analysis. Other aspects of human physiology, such as eye color, are easier to predict using genetic analysis.
"One thing we're certain of [is] there's no single gene that suddenly makes your nose big or small," Kun Tang, from the Shanghai Institutes for Biological Sciences in China, said.
In order to further refine the system, Shriver has already started sampling more people. Adding further diversity to the database should allow the application to make even more accurate recreations of a person's face. In the next round of testing, 30,000 different points will be used instead of 7,000. Merging this development with 3D printers would make it possible to print out 3D models of a person, just based on a piece of DNA.
Such models - digital or physical - are not likely to be used in courts anytime soon. A more likely scenario is use as modern day version of police sketches, assisting police in finding suspects. Only after an arrest would the DNA of a suspect be compared to that collected at the scene of a crime.
Creating 3D facial models from genetic evidence was detailed in Nature.
Wednesday, April 23. 2014
New Drone Can Hack Into Your Smartphone To Steal Usernames And Passwords
Via Think Progress
-----

CREDIT: AP – Mel Evans
A new hacker-developed drone can lift your smartphone’s private data from your GPS location to mobile applications’ usernames and passwords — without you ever knowing. The drone’s power lies with a new software, Snoopy, which can turn a benign video-capturing drone into a nefarious data thief.
Snoopy intercepts Wi-Fi signals when mobile devices try to find a network connection. London researchers have been testing the drone and plan to debut it at the Black Hat Asia cybersecurity conference in Singapore next week. Snoopy-equipped drones can aid in identity theft and pose a security threat to mobile device users.
Despite its capabilities, the drone software project was built to raise awareness and show consumers how vulnerable their data is to theft, Glenn Wilkinson, a Sensepost security researcher and Snoopy’s co-creator, told CNN Money.
As a part of its controversial surveillance programs, the U.S. National Security Agency already uses similar technology to tap into Wi-Fi connections and control mobile devices. And even though Snoopy hasn’t hit the market, phone-hacking drones could become a reality in the United States now that a federal judge recently overturned the U.S. Federal Aviation Administration’s commercial drone ban. Because the ban was lifted, filmmakers and tech companies such as Facebook and Amazon are now allowed to fly drones — be it to increase Web access or deliver packages — for profit.
Before latching onto a Wi-Fi signal, mobile devices first check to see if any previously connected are nearby. The Snoopy software picks up on this and pretends to be one of those old network connections. Once attached, the drone can access all of your phone’s Internet activity. That information can tell hackers your spending habits and where you work.
With the right tools, Wi-Fi hacks are relatively simple to pull off, and are becoming more common. Personal data can even be sapped from your home’s Wi-Fi router. And because the number of Wi-Fi hotspots keeps growing, consumers must take steps, such as using encrypted sites, to protect their data.
Data breaches overall are happening more often. Customers are still feeling the effect of Target’s breach last year that exposed more than 100 million customers’ personal data. But as smartphones increasingly becoming the epicenter of personal data storage, hacks targeting the device rather than individual apps pose a greater privacy and security threat.
According to a recent Pew Research study, about 50 percent of Web users publicly post their birthday, email or place of work — all of which can be used in ID theft. Nearly 25 percent of people whose credit card information is stolen also suffer identity theft, according to a study published by Javelin Strategy & Research of customers who received data breach notifications in 2012. Moreover, most people manage about 25 online accounts and only use six passwords, quadrupling the potential havoc from one account’s password breach.
Thursday, April 17. 2014
Apple Releases iBeacon Specifications Under Non-Disclosure Agreement
Via TechCrunch
-----

Apple has just released the iBeacon specifications for everyone who is a member of the MFi program, Apple’s program for hardware partners (“Made for iPhone program”, etc.). You’ll have to sign an NDA to read the specifications. BEEKn first spotted the news. The company also reiterates that you can’t use the iBeacon brand without prior consent. You have to register to the MFi program, submit a request and get approved by Apple. It’s free for now.
As a reminder, iBeacon is an indoor positioning system based on Bluetooth Low Energy. Many iOS and Android devices now come with Bluetooth Low Energy, so they are all theoretically compatible with iBeacon. iBeacon is particularly interesting for retailers. They can buy a beacon (such as the Estimote pictured above) and use it for proximity interactions.
For instance, merchants can send a push notification to smartphone users when they get close to a particular product. It can also be used for payment systems to detect who is in your store. There are countless of possibilities — it’s just the beginning.
iBeacon is just a particular implementation of Bluetooth Low Energy. Devices broadcast a Bluetooth LE signal, and iPhones download data when they are close to a beacon. It also works with Android phones, and Apple apparently doesn’t want to stop that.
Yet, iBeacon is a registered trademark and Apple can decide what to do. For now, developers who sign up to the MFi program, request to use the iBeacon name, and conform to the Apple standard can use the brand for free. iBeacon devices will mostly be B2B devices for shop owners, trade show staffs and more.
Think of it like the “Made for iPhone” brand. Dock manufacturers can build a speaker that works with Android and iOS phones. They put the little “Made for iPhone” stickers. It means that Apple certifies that it will work well with iPhones. The iBeacon brand works the same way for beacons.
Wednesday, April 16. 2014
Plugin Visualizes Your Entire Browser History
Via fastcodesign
-----
Want to know exactly how much of your Internet time is spent fiddling around on Facebook versus doing all-important Googling, online shopping or watching videos? Try Iconic History, a plugin that puts your whole browser history into an exhaustive stream of favicons, the icons that appear next to a website's name on a browser tab.
Created by Carnegie Mellon University computer science student Shan Huang for a class on interactive art and computational design, the plugin pulls your browser history from Google Chrome (which keeps up to four months of data) and visualizes every site you've visited by sorting each individual URL's associated icon chronologically. So it'll show if you've spent an entire day surfing Facebook, or if you've stayed up late into the night visiting Wikipedia.

"Because I spend so much time online every day, doing all sorts of things from working to socializing to just aimless wandering, I thought browser history alone could narrate a significant portion of my life and what was on my mind," Huang writes in her summary of the project. For example, she found she frequently stayed up late online shopping at sites like Urban Outfitters and Macy's.
Each icon is linked to the original URL, so it's easy to go back and see exactly which Urban Outfitters sweater you were coveting or which seven YouTube videos you watched in a row, though these are visualized just as a long list of identical pictures. You can filter the list to show a specific site or time window during the day, in case you really need to know what you've been searching between midnight and 6 a.m. Hopefully you haven't been clearing your most interesting data!
Iconic History - a browser history visualization from Shan on Vimeo.
Try Iconic History for yourself here, or check out Huang's demo.
How to turn an old phone or tablet into a PC productivity tool
Via PCWorld
-----
Your old phones and tablets don’t have to become e-waste. They can do real work as repurposed sidekicks for your PC. Think of them as bonus touchscreen displays and you’ll begin to see the possibilities. They just need to be plugged in, wiped of unneeded apps and notifications, and they’re ready to serve as desktop companions. Here are some of the best ways to reuse that old tech.
Turn your tablet into a second monitor
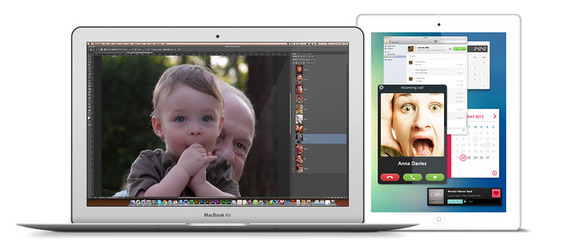
Air Display can turn your tablet into a true second screen for your PC or Mac.
One simple way to get some extra mileage out of an old tablet is to turn it into a dedicated PC monitor. Even with just 7-inch tablet, you can use the extra screen to keep an eye on instant messages, email, or social networks. If you’re working with photos, video or music, the second screen could even serve as a dedicated space for toolbars. It’s also an easy second screen to pack up and take with you.
I suggest Air Display, a $10 app for iOS andAndroid that connects to your main computer over Wi-Fi. (A $5 app called iDisplay also supports USB connections on Android devices, but I had trouble getting it to work on a 2012 Nexus 7.) You may also want to pick up a cheap tablet stand, such as this one.
Use your phone as an air mouse or dictation tool
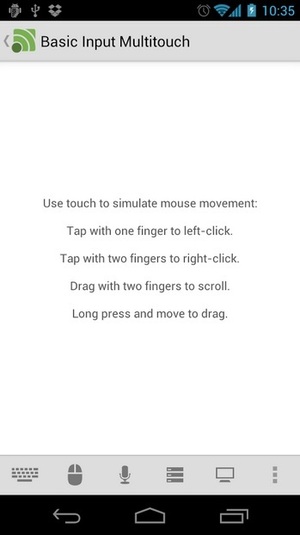
Unified Remote for Android can be used as an impromptu gesture or voice control tool, among other things.
If you need a break from hunching over your desk, a spare smartphone can serve as a touchscreen mouse for your PC. All you need is a remote mouse app that communicates with a companion desktop app over Wi-Fi.
On the iPhone, Mobile Mouse is a fine option that supports gestures such as two-finger scrolling. You can add gyroscopic air mouse controls by upgrading to the $2 Pro version. Mobile Mouse’s Android version isn’t quite as slick, so for that platform I recommend Unified Remote instead.
Here’s a neat trick for either app: With your phone’s on-screen keyboard, use the microphone key for voice dictation on your PC.
Turn your tablet into a full-blown command center
With a little effort and a few bucks, your tablet can be more than just an extra trackpad. The touch screen can also quickly launch applications and execute commands faster than you can point and click with a mouse.
iPad users should check out Actions, a $5 app that lets you create buttons for all the things you do most on your PC. You can quickly launch a new window in Chrome, expose the desktop, open the search bar, or control media playback. Just install the companion server app for Windows or Mac and start shaving the minutes off your work routine.
Actions for iPad is a colorful, customizable, and incredibly handy tool for controlling your PC.
For Android, the premium version of Unified Remote comes close to what Actions offers, even if it isn’t as snazzy. The $4 upgrade gives access to lots of app-specific control panels, plus a way to create your own panels.
Set up a small file server with battery backup
In terms of raw storage, an old phone or tablet can’t compare to a networked hard drive. But it’s good enough for documents or a small number of media files—especially if you can pop in a microSD card for extra capacity. Plus, mobile devices can hum along for days on battery power, so you can still get to your files even if someone shuts off your computer. Think of it as do-it-yourself cloud storage, without the cloud.
To transfer files onto your phone or tablet, you could just plug it into your PC and drag-and-drop. Or you could go the automated route: Install BitTorrent Sync on your PC and your phone, and use the “sync folders” option to back up whatever folders you want.
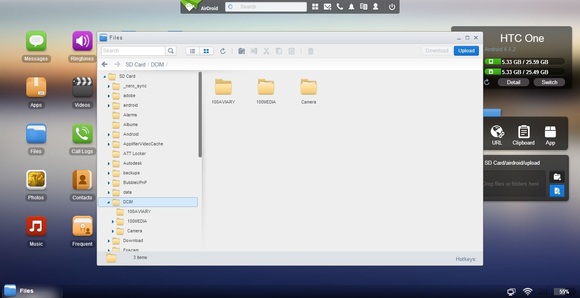
AirDroid makes shifting files from your phone to your PC and back again absolutely painless. (Click to enlarge.)
The easiest way to access Android files remotely is with AirDroid. Install the app on your phone and create a login (or just sign in with your Google account), then visit web.airdroid.com from any browser. After signing in, you’ll be able to access your phone’s file directory and snag anything you need. (Just make sure to disable “power saving mode” in AirDroid’s settings first.)
Create a desktop calculator or document scanner
Tapping digits on a touch screen is easier than pointing and clicking on your PC’s built-in calculator program. (PCalc for iOS and Real Calc for Android are both free for basic calculations, and you can upgrade to paid versions if you need more features.)
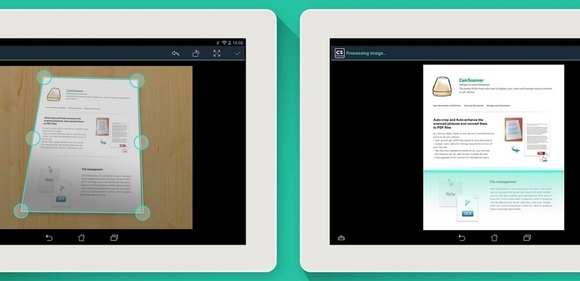
CamScanner’s a handy tool for quickly scanning documents, complete with baked-in optical character regonition technology to extract text from pics as well as tools to optimize your images.
As long as you’re making up for missing peripherals, you can also use your phone as a document scanner. CamScanner, available for both iOS and Android, is loaded with features, and you can try it for free. The paid version costs $5 per month on both platforms.
Dedicate it to calls and video chats
If you’re working on a small laptop or an older PC with limited processing power, you may want to offload Skype calls, Google Hangouts, or other video chat applications to a separate phone or tablet. That way, you can free up your PC’s resources—and its screen—for taking notes or pulling up reference files. This one’s easy: All you need is a phone or tablet with a front-facing camera and a cheap stand or monitor mount. (You could also MacGyver your own phone stand or monitor mount for practically nothing.)
Create minimalist writing/sketching station

Working on a connected tablet is a great way to eliminate the distractions that crop up on PCs.
The lack of a windowing system on iOS and Android can be a burden for serious work, but sometimes a break from multitasking can help you focus. Grab a cheap Bluetooth keyboard if you want, and dedicate a spot in your office for writing without distractions. A good note-taking app that syncs online, such as Evernote or the Android-only Google Keep, is especially useful, since whatever you write will be waiting for you when you get back to your computer.
Of course, a text editor isn’t the only tool you could have at your disposal. You could also install a diagram app, such as Lucidchart or Idea Sketch, or grab a pressure-sensitive stylus for free-form sketching.
The advantage of repurposing an older device is that you can completely dedicate it to the task. There’s nothing stopping you from using a brand-new phone or tablet for any of these purposes, however. Check out PCWorld’s guide to 13 highly productive Android apps that play nice with your PC.
Qualcomm is getting high on 64-bit chips
Via PCWorld
-----

Qualcomm is getting high on 64-bit chips with its fastest ever Snapdragon processor, which will render 4K video, support LTE Advanced and could run the 64-bit Android OS.
The new Snapdragon 810 is the company’s “highest performing” mobile chip for smartphones and tablets, Qualcomm said in a statement. Mobile devices with the 64-bit chip will ship in the first half of next year, and be faster and more power-efficient. Snapdragon chips are used in handsets with Android and Windows Phone operating systems, which are not available in 64-bit form yet.
The Snapdragon 810 is loaded with the latest communication and graphics technologies from Qualcomm. The graphics processor can render 4K (3840 x 2160 pixel) video at 30 frames per second, and 1080p video at 120 frames per second. The chip also has an integrated modem that supports LTE and its successor, LTE-Advanced, which is emerging.
The 810 also is among the first mobile chips to support the latest low-power LPDDR4 memory, which will allow programs to run faster while consuming less power. This will be beneficial, especially for tablets, as 64-bit chips allow mobile devices to have more than 4GB of memory, which is the limit on current 32-bit chips.

The layout of the Snapdragon 810 chip. (Click to enlarge.)
The quad-core chip has a mix of high-power ARM Cortex-A57 CPU cores for demanding tasks and low-power A53 CPU cores for mundane tasks like taking calls, messaging and MP3 playback. The multiple cores ensure more power-efficient use of the chip, which helps extend battery life of mobile devices.
The company also introduced a Snapdragon 808 six-core 64-bit chip. The chips will be among the first made using the latest 20-nanometer manufacturing process, which is an advance from the 28-nm process used to make Snapdragon chips today.
Qualcomm now has to wait for Google to release a 64-bit version of Android for ARM-based mobile devices. Intel has already shown mobile devices running 64-bit Android with its Merrifield chip, but most mobile products today run on ARM processors. Qualcomm licenses Snapdragon processor architecture and designs from ARM.
Work for 64-bit Android is already underway, and applications like the Chrome browser are already being developed for the OS. Google has not officially commented on when 64-bit Android would be released, but industry observers believe it could be announced at the Google I/O conference in late June.
Qualcomm spokesman Jon Carvill declined to comment on support for 64-bit Android. But the chips are “further evidence of our commitment to deliver top-to-bottom mobile 64-bit leadership across product tiers for our customers,” Carvill said in an email.
Qualcomm’s chips are used in some of the world’s top smartphones, and will appear in Samsung’s Galaxy S5. A Qualcomm executive in October last year called Apple’s A7, the world’s first 64-bit mobile chip, a “marketing gimmick,” but the company has moved on and now has five 64-bit chips coming to medium-priced and premium smartphones and tablets. But no 64-bit Android smartphones are available yet, and Apple has a headstart and remains the only company selling a 64-bit smartphone with its iPhone 5S.
The 810 supports HDMI 1.4 for 4K video output, and the Adreno 430 graphics processor is 30 percent faster on graphics performance and 20 percent more power efficient than the older Adreno 420 GPU. The graphics processor will support 55-megapixel sensors, Qualcomm said. Other chip features include 802.11ac Wi-Fi with built-in technology for faster wireless data transfers, Bluetooth 4.1 and a processing core for location services.
The six-core Snapdragon 808 is a notch down on performance compared to the 810, and also has fewer features. The 808 supports LTE-Advanced, but can support displays with up to 2560 x 1600 pixels. It will support LPDDR3 memory. The chip has two Cortex-A57 CPUs and four Cortex-A53 cores.
The chips will ship out to device makers for testing in the second half of this year.
Wednesday, April 09. 2014
The NSA is burning down the web, but what if we rebuilt a spy-proof internet?
Via The guardian
-----

What will life be like after the internet? Thanks to the mass surveillance undertaken by the National Security Agency and the general creepiness of companies like Google and Facebook, I've found myself considering this question. I mean, nothing lasts forever, right?
There's a broad tech backlash going on right now; I wonder just how deep the disillusionment runs. I get the feeling that there are folks out there who would relish putting the internet behind us sooner rather than later. Imagine that: even the internet could be a thing of the past one day. What would that be like? No Facebook. No Google. No government nerds looking through your webcam.
But could we become more secure without abandoning the internet? What if there's a third way? One that doesn't involve either passive resignation to being exploited or a Luddite smash-the-looms fantasy. What if we began to develop and encourage the adoption of machines and a network that are actually secure – through which neither thieves, corporations, nor the NSA could track us – and what if these could be configured by us, to really do what we want them to do? To stop the spying, stealing and monitoring, but to allow other things to continue.
What would that look like?
A problem: maybe the internet wasn't built to be secure
We all know by now that the NSA and the UK's Government Communication Headquarters are reading our emails, listening to our phone conversations, storing our metadata and using our computers and phones to watch us. A bunch of dorky guys amassing huge collections of pictures of tits and dicks. Here they are, hard at work, protecting us:

I know I feel safer now! Happy viewing, guys! If we had any doubts before, now we know that the government doesn't trust us – so very many of us – and we certainly don't trust it.
Meanwhile, thieves have managed to get their hands on more than 100 million credit card numbers and PINs from Target and Neiman Marcus. Lots of cyber thieves operate in the former Soviet republics, so maybe that new sports car in Baku or that night on the town in Sofia is courtesy of your hard-earned savings.
It's not just the government and thieves who take advantage of the web's weird combination of opacity and insecurity; Google, Apple, Facebook, Microsoft and other tech companies repurpose our phones and tablets into tracking and monitoring devices. Google, for one, makes a lot of money gathering information from us and selling it to advertisers. The free conveniences we enjoy – email, endless web browsing, cats and all sorts of gossip – are not, in fact, free. They are merely clever trade-offs for information about you. In return for access to much of the world's knowledge, we hand over valuable personal information about everything we believe, everything we're curious about, everything we desire or fear – everything that makes us who we are, at least to the retailers, advertisers and secret government agencies on the receiving end.
It is we who are being sold.
Trading our privacy for the convenience of a Google search is not so different from giving up constitutionally protected freedoms in exchange for the "security" that our government claims to offer. At least with Google and other tech services we know we're getting something; whether we actually are more secure because of the NSA's surveillance is an unresolved question. We are frequently told that this indiscriminate data collection has produced valuable results, but those results are "secret," so you'll just have to trust the government. I'm not saying we don't need strong security measures to protect us from lunatics, but this dragnet surveillance has gone way beyond meeting that need.
Cyber thieves, for their part, don't offer the average internet user anything in return – not only that, but they make money selling information about the security gaps they find to the US government. It's an open question whether the government actually wants to patch up those holes and make the internet more secure. For now, it's in its interest to keep these holes open – available for future use, but secret. And we know how good the government is at keeping secrets.
To a lot of folks it appears that the corporations, the thieves and the government are all doing exactly the same thing: the "legal" behavior and the illegal theft are cousins. Spying and cyber theft are not freak phenomena; increasingly, they appear to be unavoidable consequences of online access as it now exists.
As the internet has become more integral to our lives, we've become more vulnerable to its seductions, and the web has started to act like a bully, a drug dealer. It knows we need it, love it and are addicted to it, so it can take advantage of that need.
Moreover, the internet is no longer even egalitarian. And that was one of the big pluses! Once it seemed that everyone had the same access to information. Soon, though, its glories will be available only to those who can afford them. Recently, Verizon won a court ruling against net neutrality, which the Federal Communications Commission has announced it will not appeal, so the way is clear for corporations to play favorites with internet traffic. Clearly this miraculous technology – developed in part with the noble ambition that nuclear scientists might communicate freely – has been perverted into something dark and disturbing.
A thought experiment: what if we broke the internet?
These deteriorating conditions feed into the rapidly growing discontent regarding the internet. What if the disillusionment eventually reaches a point at which many feel that the free services and convenience no longer compensate for the exploitation, control and surveillance? What if, one night, a small group of people decided they've had enough and say, Let's call it a day? What exactly might this imaginary band of outsiders do? Would they or could they shut down the entire internet? Is that even possible? And what would be the consequences? Now, let's be clear, I'm not advocating this, but I also don't think it's entirely outside the realm of possibility.
As we all know by now, the NSA tapped into a vast amount of international and domestic internet communications by installing devices in small rooms in data centers in San Francisco and a few other places. It didn't require an all-out assault to subvert one of these fortresses – just a small intervention with impunity and intent. Here is what the inside of one of these buildings looks like:

That's what makes it all work? My music studio isn't this messy!
The internet, it seems, is not "nowhere". There are nodes in the internet, where great amounts of data come and go, and they do have real physical locations. Intercept a few of these nodes – there are some here in downtown New York, linked to some in Lisbon, where the fiberoptic cables surface – and you can infiltrate the whole world, as the NSA knows. They needed access to only a few undistinguished buildings to get what they wanted.
So… imagine that a hypothetical group of disillusioned citizens obtains access to the same nodes – let's say it's an inside job by some building employees – but instead of tapping the nodes, as the NSA did, they break them. And to avoid any possibility of repair, they detonate a small timed radioactive paintball after they leave. No one gets hurt, but the radioactive splatter creates a no-go zone. As a result, no one can fix the fiber optics or even get near them for, let's say, 100 years. The city outside, and even the rest of the building, might remain safe, but don't go near that room on the 20th floor!
This might sound far-fetched. Surely no one can "break" the internet! The internet is our friend! And how could anyone even get into the buildings that keep it running?! But as we've seen, neither our "security" organizations nor the world's largest corporations are very good at keeping their shit secure.
OK, now, for the sake of this thought experiment…
A wasteland: what if the web as we know it didn't exist?

The internet is a thing of the past. What now?
Obviously business goes haywire, to say nothing of the profitable business of watching us. High-speed automated trading, which makes up half or more of New York's stock market activity (though the proportion is currently declining, ends. Wall Street initially crashes, but eventually it finds a new normal. (There was trading before the internet, after all.) Streaming movies and music, however, is totally over. Skyping your grandmother – over.
Google is now absolutely worthless, though it still has all its existing data housed in massive server farms. No more drones will take flight or drop bombs on Pakistan or Yemen. Cash and checks are still pretty good; credit and debit cards can't rely on internet connections to verify accounts anymore – though they still work, as they did before the web. Amazon has ceased to exist, and huge brick-and-mortar stores like Wal-Mart have lost track of their massive inventories. Small towns and bookstores make a comeback! Even record stores!
No one can unfriend you, and Mark Zuckerberg won't know what and whom you like or don't like ever again. Online courses will halt; teachers will have to teach their students face-to-face. The Singularity will be postponed.
Would the world really be a better place without the internet? Is a complete reset really necessary?
For some, the internet has offered endless moneymaking opportunities, but whether many of the web's touted benefits end up reaching the majority of people is debatable. More and more, it seems that only a minority are making a fortune off what was extolled as a universally liberating technology.
To be fair, the internet offers some egalitarian benefits, besides pictures of cats. There's the well-publicized assistance it lends to movements for human rights and democracy and the instantaneously accessible forum it provides for much of the world's knowledge. Truth be told, the internet didn't actually create any of those movements or that knowledge, but it has certainly empowered a lot of previously voiceless people who now have access to them.
It's hard to weigh the worth of the internet because we can't even imagine life without it. We've internalized it. It's part of us, which explains why we are exploited so easily online. Is the internet a cancer killing us little by little or a wonderful cybernetic extension of our brains? Let's say we wanted to rid ourselves of the cancer. Would the cure be catastrophic or would the liberation be worth it?
A utopia: what would a revised internet look like?

To be honest, I have a hard time imagining internet 2.0. I'm old enough to remember the utopian enthusiasm that greeted the internet when it emerged 20 years ago. We can't go back – we know too much now – but maybe we can learn from what we loved about the internet back then. Namely, its egalitarian nature – that homemade and small-scale sites were just as accessible as the emerging e-commerce platforms. It was a pleasant, chaotic jumble. Can we revive the feeling of a souk and lose the big-box store feel?
Some folks have advocated that the internet be considered a utility. A "necessary" part of our lives like water, electricity or gas. It might be better to have some fair regulation than to let market forces shape the landscape. Can you imagine if corporations owned our water supply?
Imagine this: in a new internet, we'd still be able to send emails. Academic and nonprofit institutions would still share resources online. Wikipedia and web-based journalism would still exist. But if we can't be tracked as we are now, a lot would change. Google would lose its primary sources of revenue – ads – and return to being a very good search engine, with a lot fewer employees. The NSA and the other data thieves and collectors would be helpless. No one would have data on countless innocent citizens that could be repurposed to God knows what ends. The Chinese couldn't hack into the North American power grid.
All that money that was poured into online surveillance programs could of course now be spent on health and education (I did say "could" – I'm being very optimistic). That would actually increase security – worldwide. It's pretty well accepted that extreme poverty breeds terrorism. Offering attractive alternatives to extremism that lead to better lives is the way to win the "war on terror". Guns, drones and mass surveillance do the opposite: they actually breed terrorism. If we have the imagination to rethink both network security and national security – and that's a big if – then the whole world would have the opportunity to become safer, no matter what the US government claims.
Is there a will to change?
Let's assume that such a secure network structure is technically possible. internet 2.0 for real. Even if it is technically possible, I have a feeling that it might take a lot of willpower to walk away from the tit of convenience. Corporations and governments have built massive economic and political systems based on our accepting things as they are, and they will fight powerfully against any reforms.
What could make that surge of willpower come into existence? The information-hoovering in which corporations engage is of a kind with the government surveillance; in both cases we are prey to distant agendas. The three forms of data-gathering (if one includes cyber crime) are all connected – and none of them make us happier or more secure.
Reassessing what makes us secure might be a start. Real, life-long security comes not from the barrel of a gun or from being able to spy on your fellow citizens like a Stasi informant; it comes with less harsh extremes of wealth and poverty and increased access to health care and education. Embracing the security that comes with a more robust democracy is far preferable to other incentives to change, like all our credit cards becoming worthless or the NSA leaking incriminating webcam pictures of its critics. Before a catastrophic collapse like my hypothetical one ever comes, let's find it within ourselves to give up some convenience and become a little more human.
Quicksearch
Popular Entries
- The great Ars Android interface shootout (131079)
- Norton cyber crime study offers striking revenue loss statistics (101711)
- MeCam $49 flying camera concept follows you around, streams video to your phone (100096)
- Norton cyber crime study offers striking revenue loss statistics (57940)
- The PC inside your phone: A guide to the system-on-a-chip (57520)
