Via EE Times
-----
PARIS — As of the end of 2014, 16 million mobile devices worldwide have
been infected by malicious software, estimated Alcatel-Lucent’s security
arm, Motive Security Labs, in its latest security report released Thursday (Feb. 12).
Such malware is used by “cybercriminals for corporate and personal
espionage, information theft, denial of service attacks on business and
governments and banking and advertising scams,” the report warned.
Some of the key facts revealed in the report -- released two weeks in
advance of the Mobile World Congress 2015 -- could dampen the mobile
industry’s renewed enthusiasm for mobile payment systems such as Google
Wallet and Apple Pay.
At risk is also the matter of privacy. How safe is your mobile
device? Consumers have gotten used to trusting their smartphones,
expecting their devices to know them well enough to accommodate their
habits and preferences. So the last thing consumers expect them to do is
to channel spyware into their lives, letting others monitor calls and
track web browsing.
Cyber attacks
The latest in a drumbeat of data
hacking incidents is the massive database breach reported last week by
Anthem Inc., the second largest health insurer in the United States.
There was also the high profile corporate security attack on Sony in
late 2014.
Declaring that 2014 “will be remembered as the year of
cyber-attacks,” Kevin McNamee, director, Alcatel-Lucent Motive Security
Labs, noted in his latest blog
other cases of hackers stealing millions of credit and debit card
account numbers at retail points of sale. They include the security
breach at Target in 2013 and similar breaches repeated in 2014 at
Staples, Home Depot Sally Beauty Supply, Neiman Marcus, United Parcel
Service, Michaels Stores and Albertsons, as well as the food chains
Dairy Queen and P. F. Chang.
“But the combined number of these attacks pales in comparison to the
malware attacks on mobile and residential devices,” McNamee insists. In
his blog, he wrote, “Stealing personal information and data minutes from
individual device users doesn’t tend to make the news, but it’s
happening with increased frequency. And the consequences of losing one’s
financial information, privacy, and personal identity to cyber
criminals are no less important when it’s you.”
'Workhorse of cybercrime'
Indeed, malware
infections in mobile devices are on the rise. According to the Motive
Security Labs report, malware infections in mobile devices jumped by 25%
in 2014, compared to a 20% increase in 2013.
According to the report, in the mobile networks, “Android devices
have now caught up to Windows laptops as the primary workhorse of
cybercrime.” The infection rates between Android and Windows devices now
split 50/50 in 2014, said the report.
This may be hardly a surprise to those familiar with Android
security. There are three issues. First, the volume of Android devices
shipped in 2014 is so huge that it makes a juicy target for cyber
criminals. Second, Android is based on an open platform. Third, Android
allows users to download apps from third-party stores where apps are not
consistently verified and controlled.
In contrast, the report said that less than 1% of infections come
from iPhone and Blackberry smartphones. The report, however, quickly
added that this data doesn’t prove that iPhones are immune to malware.
The Motive Security Labs report cited findings by Palo Alto Networks
in early November. The Networks discussed the discovery of WireLurker
vulnerability that allows an infected Mac OS-X computer to install
applications on any iPhone that connects to it via a USB connection.
User permission is not required and the iPhone need not be jail-broken.
News stories reported the source of the infected Mac OS-X apps as an
app store in China that apparently affected some 350,000 users through
apps disguised as popular games. These infected the Mac computer, which
in turn infected the iPhone. Once infected, the iPhone contacted a
remote C&C server.
According to the Motive Security Labs report, a couple of weeks
later, FireEye revealed Masque Attack vulnerability, which allows
third-party apps to be replaced with a malicious app that can access all
the data of the original app. In a demo, FireEye replaced the Gmail app
on an iPhone, allowing the attacker complete access to the victim’s
email and text messages.
Spyware on the rise
It’s important to note that
among varieties of malware, mobile spyware is definitely on the
increase. According to Motive Security Labs, “Six of the mobile malware
top 20 list are mobile spyware.” These are apps used to spy on the
phone’s owner. “They track the phone’s location, monitor ingoing and
outgoing calls and text messages, monitor email and track the victim’s
web browsing,” according to Motive Security Labs.
Impact on mobile payment
For consumers and mobile operators, the malware story hits home hardest
in how it may affect mobile payment. McNamee wrote in his blog:
The rise of mobile malware threats
isn’t unexpected. But as Google Wallet, Apple Pay and others rush to
bring us mobile payment systems, security has to be a top focus. And
malware concerns become even more acute in the workplace where more than
90% of workers admit to using their personal smartphones for work
purposes.
Fixed broadband networks
The Motive Security
Labs report didn’t stop at mobile security. It also looked at
residential fixed broadband networks. The report found the overall
monthly infection rate there is 13.6%, “substantially up from the 9%
seen in 2013,” said the report. The report attributed it to “an increase
in infections by moderate threat level adware.”
Why is this all happening?
The short answer to
why this is all happening today is that “a vast majority of mobile
device owners do not take proper device security precautions,” the
report said.
Noting that a recent Motive Security Labs survey found that 65
percent of subscribers expect their service provider to protect both
their mobile and home devices, the report seems to suggest that the onus
is on operators. “They are expected to take a proactive approach to
this problem by providing services that alert subscribers to malware on
their devices along with self-help instructions for removing it,” said
Patrick Tan, General Manager of Network Intelligence at Alcatel-Lucent,
in a statement.
Due to the large market share it holds within communication networks,
Alcatel-Lucent says that it’s in a unique position to measure the
impact of mobile and home device traffic moving over those networks to
identify malicious and cyber-security threats. Motive Security Labs is
an analytics arm of Motive Customer Experience Management.
According to Alcatel-Lucent, Motive Security Labs (formerly Kindsight
Security Labs), processes more than 120,000 new malware samples per day
and maintains a library of 30 million active samples.
In the following pages, we will share the hilights of data collected by Motive Security Labs.
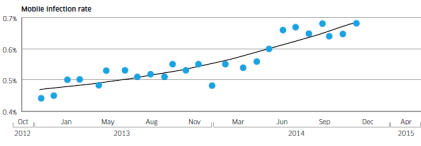
Mobile infection rate since December 2012
Alcatel-Lucent’s Motive Security Labs found 0.68% of mobile devices are infected with malware.
Using the ITU’s figure of 2.3 billion mobile broadband subscriptions,
Motive Security Labs estimated that 16 million mobile devices had some
sort of malware infection in December 2014.
The report called this global estimate “likely to be on the
conservative side.” Motive Security Labs’ sensors do not have complete
coverage in areas such as China and Russia, where mobile infection rates
are known to be higher.
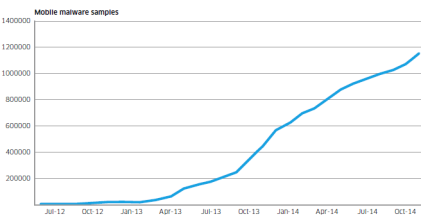
Mobile malware samples since June 2012
Motive Security Labs used the increase in the number of samples in its malware database to show Android malware growth.
The chart above shows numbers since June 2012. The number of samples grew by 161% in 2014.
In addition to the increase in raw numbers, the sophistication of
Android malware also got better, according to Motive Security Labs.
Researchers in 2014 started to see malware applications that had
originally been developed for the Windows/PC platform migrate to the
mobile space, bringing with them more sophisticated command and control
and rootkit technologies.
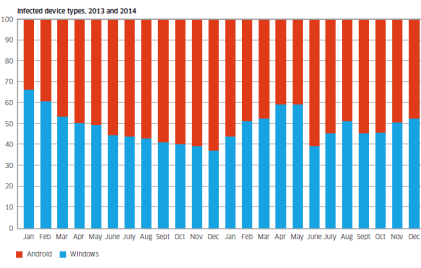
Infected device types in 2013 and 2014
The chart shows the breakdown of infected device types that have been
observed in 2013 and 2014. Shown in red is Android and shown in blue is
Windows.
While the involvement of such a high proportion of Windows/PC devices
may be a surprise to some, these Windows/PCs are connected to the
mobile network via dongles and mobile Wi-Fi devices or simply tethered
through smartphones.
They’re responsible for about 50% of the malware infections observed.
The report said, “This is because these devices are still the
favorite of hardcore professional cybercriminals who have a huge
investment in the Windows malware ecosystem. As the mobile network
becomes the access network of choice for many Windows PCs, the malware
moves with them.”
Android phones and tablets are responsible for about 50% of the malware infections observed.
Currently most mobile malware is distributed as “Trojanized” apps.
Android offers the easiest target for this because of its open app
environment, noted the report.