Wednesday, September 28. 2011
New DoCoMo smartphone case able to detect radiation
Via Asahi shimbun
-----

NTT DoCoMo Inc. has developed a smartphone case featuring a function that measures radiation levels.
The case has a sensor on it that identifies radiation levels, and the results show up on the screen. A special application must be installed to take advantage of the service.
The new feature, using technologies developed by a domestic dosimeter maker, can determine radiation levels from 0.01 microsieverts to 100 millisieverts per hour, the company said. The device also allows people to access measured values by time on a map using the global positioning system available with the carrier's smartphones.
NTT DoCoMo also developed smartphone cases that enable measurements of ultraviolet rays and body fat percentages. These cases can be switched to monitor various health conditions, the company said. Specific dates for marketing the cases have yet to be decided.
Prototypes of the three cases will be exhibited at Ceatec Japan 2011, Japan's largest exhibition on IT and electronics, to be held Oct. 4-8 at the Makuhari Messe convention center in Chiba Prefecture.
Tuesday, September 27. 2011
Facebook and the 'Like Me’ Election
Via Businessweek
By Elizabeth Dwoskin
-----
New advertising tools from the social media giant let campaigns find and target voters

Charlie Neibergall/AP Photo
Michele Bachmann wants to be your friend. So much so that her campaign is scouring your travels on Facebook for the things that matter to you most. Then she can place a customized message on your page assuring you that those things are important to her, too.
Bachmann did this to great effect in August, when she won the Republican straw poll in Iowa in part by zeroing in on the Facebook pages of potential supporters who lived nearby. Facebookers who had identified themselves as Tea Party supporters or Christian rock fans, or who had posted messages in favor of tax cuts or against abortion, found an ad from Bachmann waiting for them on their profile page in the weeks before the vote, asking for their support and directing them to a link where they could arrange a free ride to the polling place. Bachmann’s campaign says a significant portion of the people who pushed her over the top in Iowa—they won’t say how many—came as a result of the ad campaign.
While some candidates are still trying to get their heads around social media —Rick Perry has been known to block people he doesn’t like from following him on Twitter—Bachmann and other well-funded candidates, including Mitt Romney and Barack Obama, are putting Facebook at the center of their campaign strategies. Working with Facebook’s Washington office, they are taking advantage of just-released advertising tools the company is marketing to politicians.
The software allows candidates to target campaign ads to individuals in ways that weren’t possible a few months ago, reaching them on a site where they spend a lot of time and are less likely to tune out the pitch. “They may not know we’re looking for them,” says Rebecca Donatelli of Campaign Solutions, a social media consulting firm in Alexandria, Va., which was hired by Bachmann. “So we have to give them the opportunity to be found.”
Unlike expensive radio and TV ads, which are blasted out to thousands or millions of people and hit the eyes and ears of as many opponents as supporters, these appeals are often aimed at just a few hundred or even a few dozen potential voters who may never have expressed interest in the candidate. The ads use information Facebook constantly collects about its users to connect with people. “In the last 45 days, I’ve designed over 1,000 ads,” says Michael Beach, a GOP consultant working for Romney.
The campaigns are able to churn out so many ads because Facebook makes it cheap and easy to do, especially compared with TV spots or even Google (GOOG) Ads, which can reach many more people but not necessarily the ones most likely to respond favorably. Facebook ads can be had for 50¢ or less per click—and by counting those clicks, the campaigns know within minutes whether they’re working.
“We’ll throw out four or five different messages targeting different demographics,” says Michael Hendrix, a Dallas-based consultant who works with Donatelli on the Bachmann campaign. “You’re trying to figure out which message will drive a higher response.”
Hendrix’s latest Facebook project is what he refers to as “the gamification of politics.” In virtual reality games such as Facebook’s popular FarmVille, he sees a demographic frontier for Republicans in 2012. He has written software, to be launched later this year, that will allow FarmVille players to get active in politics within the game. Their online characters will be able to go door to door to other players’ imaginary farms, campaigning for real-life candidates and placing yard signs on their lawns. Hendrix is blunt about his intentions. “The majority of social gamers are stay-at-home moms over 38,” says Hendrix. And they vote. He hopes to use the game “to target soccer moms again.”
Facebook’s voter-sifting tools are the same as those it markets to corporations. (Sometimes the same people use the tools for politics and commerce; in addition to his work for Bachmann, Hendrix handles social media for Moët Hennessy (LVMUY), the Champagne maker.) But the pitch is different. The company has stocked its Washington operation with political pros who speak the language of campaigns and elections.
In 2007, Facebook hired Adam Conner, then a 23-year-old Democrat staffer on the House Rules Committee, to help the company break into the capital. He started out slow, teaching politicians the basics of setting up a Facebook page. Democratic politicians were happy to hear Conner’s social media spiel, but some Republicans viewed him with suspicion. So in February, Facebook hired Katie Harbath, a 30-year-old digital strategist for the National Republican Senatorial Committee. Around the office, they’re jokingly known as “the R” and “the D.”
Facebook’s post-industrial space in downtown D.C., where guests are invited to write on the walls with brightly colored Sharpies, may be the most un-Washington workplace in the city. “What I push with folks is that, while the fan count matters, how many people are interacting with it really matters,” says Harbath, who is one of a dozen people working for Facebook in Washington. “How many people are liking it, commenting on it, sharing it with their friends.”
Which raises an important question: Is the effort and money Bachmann and her rivals put into all this liking, commenting, and sharing bringing tangible results that can be measured in volunteers, donations, and ultimately votes next November? The answer is: They don’t know yet. No one has figured out how to “monetize the like,” says Donatelli. What Facebook provides at the moment is an efficient way to reach someone without having to reach everyone and an enormous platform to get a message across without interference from the conventional media. “It’s not in the sheer numbers, but in the intensity of your followers,” Donatelli says. She says that Bachmann fans tend to be issue-driven and feverishly post and cross-post on Facebook, keeping the candidate’s name in the conversation even as her poll numbers slide compared with Romney’s and Perry’s.
Ultimately, Bachmann’s team believes conversation will translate into action and money, like they say it did in Iowa this summer. Otherwise, they say, they wouldn’t bother wasting precious resources on it. “What’s the point of having a fan or a follower if they don’t do anything?” says Donatelli. “At the end of the day, this is a persuasion tool.”
The bottom line: Presidential candidates are targeting potential supporters with Facebook ads, which can cost less than 50¢ a click.
Monday, September 26. 2011
Google digitizes the Dead Sea Scrolls and puts them online
Via Slash Gear
-----
The Dead Sea Scrolls are some of the most famous Christian documents in the world and they are the oldest known biblical manuscripts in existence. The scrolls have a storied history that saw them stashed away inside a series of caves on the shores of the Dead Sea to protect them for the Roman armies that were invading the Holy Land in 68 BCE. The scrolls were lost until 1947 when a shepherd tossed a rock into the cave and discovered the scrolls.

The scrolls have been on exhibit since 1965 at the Shrine of the Book at The Israel museum in Jerusalem. Google has announced that it has now made the Dead Sea Scrolls available online and has digitized all of the content in the scrolls and made that content searchable online. The images of the scroll are high resolution at up to 1200MP to allow the user to see everything about the scrolls.

Google says that you can zoom in on the Temple Scroll and see what the animal skin that the text is written on looks like. The Great Isaiah Scroll can be read chapter and verse. The Hebrew text is also translated into English when clicked. The scrolls went online via a partnership between Google and The Israel Museum, Jerusalem.
---
Friday, September 23. 2011
Amazon Kindle books now available in public libraries
Via myce
---
Amazon has struck a deal with 11,000 U.S. libraries that lets Kindle owners borrow ebooks from the increasingly high-tech institutions. The company said Kindle books accessed through this method will boast a suite of social networking support, including Facebook and Twitter. Additionally, Amazon’s own Whispersync app is supported – which means benefits readers previously needed to scuff up books to enjoy, such as bookmarking and highlighting important passages, are freely available.
“Starting today, millions of Kindle customers can borrow Kindle books from their local libraries,” said Jay Marine, Amazon Kindle director. Marine called libraries “a critical part of our communities” and touted the announcement as an important step in bridging an ever-widening gap between the old and the new.
According to Amazon, the process itself is quick and easy.
Members whose local libraries include the online OverDrive service can visit their official sites and select a title for download. Both an Amazon.com account and active library card are required. Transactions are completed over a Wi-Fi connection or USB transfer. Those without a Kindle can still take part in the program by downloading the company’s free Kindle app on a bevy of other devices, including iPad, BlackBerry and the PC Kindle Cloud Reader.
The closure of Borders stores across the country and the growing popularity of digital media consumption among e-reader and tablet owners may not spell utter doom for paper-bound books, but the convenience of downloading them from your home into a single device is hard to ignore. Amazon’s agreement with libraries proves as much.
The tough part now is getting more people to actually read. Sadly, there’s no app for that.
Thursday, September 22. 2011
Dr. Watson - Come Here - I Need You
Via big think
By Dominic Basulto
-----

The next time you go to the doctor, you may be dealing with a supercomputer rather than a human. Watson, the groundbreaking artificial intelligence machine from IBM that took on chess champions and Jeopardy! contestants alike, is about to get its first real-world application in the healthcare sector. In partnership with health benefits company WellPoint, Watson will soon be diagnosing medical cases – and not just the everyday cases, either. The vision is for Watson to be working hand-in-surgical-glove with oncologists to diagnose and treat cancer in patients.
The WellPoint clinical trial, which could roll out as early as 2012, is
exciting proof that supercomputing intelligence, when properly
harnessed, can lead to revolutionary breakthroughs in complex fields
like medicine. At a time when talk about reforming the healthcare system
is primarily about the creation of digital health records, the
integration of Watson into the healthcare industry could really shake
things up. By some accounts, Watson
is able to process as many as 200 million pages of medical information
in seconds – giving it a number-crunching head start on doctors for
diagnosing cases. In one test case cited by WellPoint, Watson was able
to diagnose a rare form of an illness within seconds – a case that had
left doctors baffled.
While having super-knowledgeable medical experts on call is exciting, it also raises several thorny issues. At what point – if ever - would you ask for a “second opinion” on your medical condition from a human doctor? Will “Watson” ever be included in the names of physicians included in your HMO listings? And, perhaps most importantly, can supercomputers ever provide the type of bedside manner that we are accustomed to in our human doctors?
This last question has attracted much attention from medical practitioners and health industry thought leaders alike. Abraham Verghese,
a professor at the Stanford University School of Medicine as well as
bestselling author, has been particularly outspoken about the inability
of computers to provide the type of medical handholding that we are used to from human doctors.
Verghese claims that the steady digitization of records and clinical
data is reducing every patient to an "iPatient" – simply a set of
digital 1’s and 0’s that can be calculated, crunched, and computed.
Forget whether androids dream of digital sheep – can they take a digital Hippocratic Oath?
Given that the cost of healthcare is simply too high, as a society we will need to accept some compromises. Once the healthcare industry is fully digitized, supercomputers like Watson could result in a more cost-effective way to sift through the ever-growing amount of medical information and provide real-time medical analysis that could save lives. If Watson also results in a significant improvement in patient treatment as well, it’s clear that the world of medicine will never be the same again. Right now, IBM envisions Watson supplementing – not actually replacing - doctors. But the time is coming when nurses across the nation will be saying, “Watson -- Come Here –- I Need You,” instead of turning to doctors whenever they need a sophisticated medical evaluation of a patient.
Tuesday, September 20. 2011
Google offers Ice Cream Sandwich guidance to Android app devs
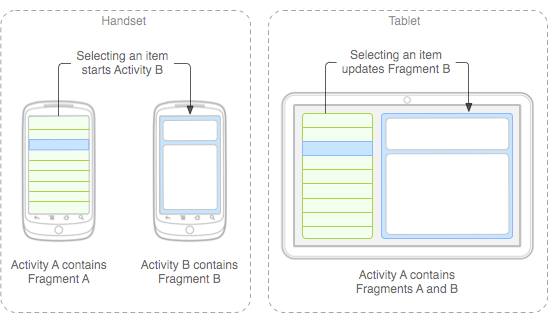
The next major version of Google's Android platform, codenamed Ice Cream Sandwich (ICS), is expected to reach the market in October or November. ICS is expected to bring some significant changes to Android because it will unify Google's tablet and phone variants into a single environment.
Although the SDK is not available yet, Google has published some technical guidance to help third-party application developers start preparing for the ICS transition. An entry posted this week on the Android developer blog describes some steps that developers can take to better accommodate the breadth of screen sizes supported by ICS.
The documentation also provides some insight into how several elements of the Honeycomb user interface could be translated to phone-sized screens in ICS. For example, it includes mockups that show the distinctive Honeycomb action bar on a tablet and a phone. It's not clear, however, if the mockups accurately depict the user experience that will be delivered in ICS.
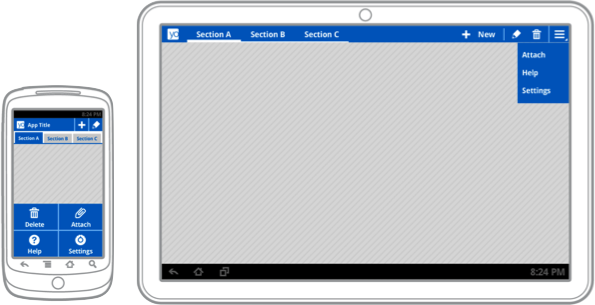
This seems to suggest that tablet user interfaces developed with standard Honeycomb APIs will largely work on phones in ICS without requiring much modification by third-party developers. That's good news, especially if it ends up being equally true the other way, which would allow phone applications built for ICS to look and feel more native on tablet devices. Google's existing Fragments framework will also help simplify interface scalability by making it easy to transition data-driven applications between single-pane to multi-pane layouts.
Developers who use Fragments and stick to the standard Honeycomb user interface components are on the right track for the upcoming ICS release, but developers who have built more complicated tablet-specific user interfaces or haven't stayed within the boundaries imposed by the documented APIs might face some challenges.
Honeycomb applications that were designed only for the tablet screen size might not scale down correctly on phones. That's a problem, because Android's versioning model doesn't prevent old applications from running on devices with new versions of the operating system—it's going to be possible for users to install Honeycomb tablet applications on ICS phones, even in cases where the result is going to be a very broken application.
In cases where third-party developers can't adapt their tablet software to work well at phone sizes, Google suggests changing the application manifest file to block the application from being installed on devices with small screens.
Another challenge is the large body of legacy devices that aren't going to be updated to ICS. Developers who want to reach the largest possible audience will have to refrain from using the new APIs, which means that it will be harder for them to take advantage of the platform's increasingly sophisticated capabilities for scaling across different screen sizes.
Google has already partially addressed this issue by backporting the Fragments framework and making it available as a static library for older versions of the operating system. It might be beneficial for them to go a step further and do the same with the Action Bar and other critical user interface components that will be designed to scale seamlessly in ICS.
It's going to take some time for the Android application ecosystem to sort all of this out after ICS is released, but Google's approach seems reasonably practical. In theory, developers who are solely targeting ICS APIs might not have to make a significant development investment to get their application working well across tablet and phone form factors.
Monday, September 19. 2011
UNIVAC: the troubled life of America's first computer
Via ars technica
By Matthew Lasar
-----

It was November 4, 1952, and Americans huddled in their living rooms to follow the results of the Presidential race between General Dwight David Eisenhower and Adlai Stevenson, Governor of Illinois. We like to think that our time is a unique moment of technological change. But the consumers observing this election represented an unprecedented generation of early adopters, who watched rather than listened to the race on the radio. By that year they had bought and installed in their homes about 21 million copies of a device called the television—about seven times the number that existed just three years earlier.
On that night they witnessed the birth of an even newer technology—a machine that could predict the election's results. Sitting next to the desk of CBS Anchor Walter Cronkite was a mockup of a huge gadget called a UNIVAC (UNIVersal Automatic Computer), which Cronkite explained would augur the contest. J. Presper Eckert, the UNIVAC's inventor, stood next to the device and explained its workings. The woman who actually programmed the mainframe, Navy mathematician Grace Murray Hopper was nowhere to be seen; for days her team had input voting statistics from earlier elections, then wrote the code that would allow the calculator to extrapolate the contest based on previous races.

J. Presper Eckert and CBS's Walter Cronkite pondering the UNIVAC on election night, 1952.
To the disquietude of national pollsters expecting a Stevenson victory, Hopper's UNIVAC group predicted a huge landslide for Eisenhower, and with only five percent of the results. CBS executives didn't know what to make of this bold finding. "We saw [UNIVAC] as an added feature to our coverage that could be very interesting in the future," Cronkite later recalled. "But I don't think that we felt the computer would become predominant in our coverage in any way."
And so CBS told its audience that UNIVAC only foresaw a close race. At the end of the evening, when it was clear that UNIVAC's actual findings were spot on, a spokesperson for the company that made the machine was allowed to disclose the truth—that the real prediction had been squelched.
"The uncanny accuracy of UNIVAC's prediction during a major televised event sent shock waves across through the nation," notes historian Kurt W. Beyer, author of Grace Hopper and the Invention of the Information Age. "In the months that followed, 'UNIVAC' gradually became the generic term for a computer."
That's putting it mildly. By the late 1950s the UNIVAC and its cousin, the ENIAC, had inspired a generic sobriquet for anyone with computational prowess—a "BRAINIAC." The term became so embedded in American culture that to this day your typical computer literacy quiz includes the following multiple choice poser:
Which was not an early mainframe computer?
- ENIAC
- UNIVAC
- BRAINIAC
But the fact that this question is even posed is testimony to the other key component of UNIVAC's history—its famous trajectory was cut short by a corporation with a much larger shadow: IBM. The turbulent life of UNIVAC offers interesting lessons for developers and entrepreneurs in our time.
The machines and their teams
During the Second World War, two teams in the United States were deployed to improve the calculations necessary for artillery firing and strategic bombing. Hopper worked with Harvard mathematician Howard Aiken, whose Mark I computer performed computations for the Navy. John Mauchly and J. Presper Eckert's Electronic and Numerical Integrator and Computer (ENIAC) rolled out rocket firing tables for the Army.
While both groups served extraordinarily during the war, their leaders could not have thought about these devices more differently. Aiken viewed them as scientific tools. Mauchly saw their potential as commercial instruments.
After the conflict, Aiken obstinately lobbied against the commercialization of computing, inveighing against the "foolishness with Eckert and Mauchly," at computer conferences. Perhaps there was a need for five or six machines in the country, he told associates; no more. But Aiken's assistant Hopper was fascinated by the duo—the former a graduate student and the latter a professor of electronics.
Eckert was "looking way ahead," Hopper recalled. "Even though he was a college professor he was visualizing the use of these computers in the business and industrial area." The University of Pennsylvania sided with Aiken. The college offered Eckert and Mauchly tenured positions, but only on the condition that they sign patent releases for all their work. Both inventors resigned from the campus and in the spring of 1946 formed the Electronic Control Company, which eventually became the Eckert-Mauchly Computer Corporation.
Over the course of five years, the two developers rethought everything associated with computational machines. The result was a device that went way beyond the age of punch card calculators associated with IBM devices. The UNIVAC, unveiled in 1951, was the fruit of this effort.
"No one who saw a UNIVAC failed to see how much it differed from existing calculators and punched card equipment," writes historian Paul E. Ceruzzi:
It used vacuum tubes—thousands of them. It stored data on tape, not cards. It was a large and expensive system, not a collection of different devices. The biggest difference was its internal design, not visible to the casual observer. The UNIVAC was a "stored program" computer, one of the first. More than anything else, that made it different from the machines it was designed to replace.
These characteristics would enable the UNIVAC to perform thousands more operations per second than its closest rival, the Harvard Mark II. And its adaptation of the entertainment industry's new tool—magnetic recording tape—would allow it to store vastly more data. UNIVAC was quickly picked up by the US Census Bureau in a $300,000 contract, which was followed by another deal via the National Bureau of Standards. Soon a racetrack betting odds calculator company called American Totalisator signed on, purchasing a 40 percent interest in the company.
You could see and hold it
But Eckert-Mauchly could not handle this volume of work on its own. Its principals drastically underbid on key contracts. After a plane crash killed the corporation's board president, the inventors and Totalisor clashed over the viability of the project. The duo then went to IBM for backing and met with Thomas Watson Junior and Senior, but could not convince the elder executive of the UNIVAC's viability.
"Having built his career on punch cards," Watson Jr. later reflected, "Dad distrusted magnetic tape instinctively. On a punch card, you had a piece of information that was permanent. You could see it and hold it in your hand.... But with magnetic tape, your data were stored invisibly on a medium that was designed to be erased and reused."
So EMCC turned to its second choice—the Remington Rand office equipment company, whose founder James Rand expressed outrage when he saw a reworked IBM typewriter rather than a Remington hooked up to the UNIVAC. "Take that label off that machine!" Rand declared on his first visit to an EMCC laboratory. "I don't want it seen in here!"
The tenderness over an IBM logo aside, Remington Rand brought an important innovation to the UNIVAC—television advertisements. The longer infomercials came complete with symphony orchestra introductions and historical progress timelines that began with the Egyptian Sphinx. The shorter ones extolled the role that UNIVAC was playing in weather prediction. "Today UNIVAC is saving time and increasing efficiency for science, industry, business, and government," one ad concluded.
A Remington Rand UNIVAC commercial.
But while that was certainly true about what the machine did for its clients, historian Beyer notes that it didn't extend to Remington's management of EMCC. Most of the office company's top staff, like its founder, didn't understand the device, and related more to punch card machines. The man put in direct charge of EMCC, former Manhattan Project director Leslie Groves, tossed Mauchly to the sales department when he flunked a company security clearance test (apparently he had attended some Communist Party meetings in the 1930s).
On top of that, new management did not sympathize with EMCC's female programmers, among them Grace Hopper, who by 1952 had written the UNIVAC's first software compiler. "There were not the same opportunities for women in larger corporations like Remington Rand," she later reflected. "They were older companies, and the jobs had been stereotyped."
Then there was Groves' marketing strategy for the UNIVAC, which amounted to selling less of the devices, even as they were being hawked on TV as exemplars of technological progress. He ordered a fifty percent annual production quota drop. "With such low sales expectations, there was little incentive to educate Remington Rand's sizeable sales force about the new technology," Beyer explains.
The biggest blow, however, came when IBM began to rethink its aversion to magnetic mainframe storage.
Left in the dust
Despite Remington/EMCC's internal chaos, interest in the UNIVAC exploded after the 1952 CBS demonstration. This created more problems. Hopper's programming staff was now besieged with attractive offers from companies using IBM gear, creating a brainiac drain within EMCC itself. "Some members of Dr. Grace Hopper's staff have already left for positions with users of IBM equipment," Mauchly noted in a memo, "and those of her staff who still remain are now expecting attractive offers from outside sources."
Customer service and support became more and more of a challenge. Still, the UNIVAC was highly competitive with IBM equipment. The question was whether EMCC could beat Big Blue in government contract bidding, specifically for the Semi-Automatic Ground Environment (SAGE) defense communications network.
The SAGE project amounted to an early-warning radar system designed to pick up enemy bomber activity around the nation's borders. It was the brainchild of Jay Forrester, director of MIT's Sernomechanisms Laboratory, and central to the idea was a network of digital computers to integrate the network, dubbed "Project Whirlwind." In three years Forrester's team had pioneered real-time, high-capacity access memory for the mainframes. The government now offered a contract to build 50 Whirlwind computers. IBM quickly rallied its forces for the contest.
"I thought it was absolutely essential to IBM's future that we win it," Thomas Watson Jr., who had none of Senior's allergies to digital computing, later explained. "The company that built those computers was going to be way ahead of the game, because it would learn the secrets of mass production."
Forrester gave the matter some thought. Remington Rand had UNIVAC. And it had the prestige of Manhattan Project Director Leslie Groves. But Remington did not have IBM's scale of operation or its production capacity. Indeed, under Groves' direction, it had scaled that capacity down. In 1953, the government offered the contract to IBM. Historian Beyer explains the consequences of this decision:
Not only did IBM take away knowledge about random-access magnetic core memory; they also learned how the Whirlwind team had pushed the technological envelope in a number of other areas. Forrester's staff had figured out a variety of ways to lower the frequency of vacuum-tube failure, thus increasing system reliability. Cathode-ray-tube displays were ingeniously employed to display processed information, index registers made programming easier, and real-time information from radar sensors could be processed without the need for a slow input medium such as punch cards.
IBM quickly integrated these discoveries into its next rollout of commercial computers. The market loved them and ordered thousands. "In a little over a year we started delivering those redesigned computers," Watson Jr. later boasted. "They made the UNIVAC obsolete and we soon left Remington Rand in the dust."

The UNIVAC universe of the 1950s—clockwise from top left: UNIVAC mathematician and programmer Grace Hopper; John W. Mauchly and John Presper Eckert; General Leslie Groves of Remington Rand; DC Comics' Brainiac confronting Superman in 1959; a Department of Commerce UNIVAC in the center.
Aftermath
Sensing the dust around it, in 1955 Remington merged with the Sperry Corporation and became Sperry Rand. No less than General Douglas MacArthur ran the new entity. This gave the UNIVAC a new lease on digital life, but one that operated in the shadow of the company that had once sworn that it would stick to punch tape: IBM.
In the meantime, a slew of firms jumped into the high-speed computing business, among them RCA, National Cash Register, General Electric, and Honeywell. "IBM and the Seven Dwarfs," they were dubbed. UNIVAC was now a dwarf.
Grace Hopper continued her work. She became an advocate of the assumption inherent in her UNIVAC compiler which she called "automatic" computing—the notion that programs should emphasize simple English words. Her compiler, later called FLOW-MATIC, understood 20 words.
Her contemporaries patiently informed her that this number was enough. Hopper "was told very quickly that [she] couldn't do this because computers didn't understand English," she later noted. Happily, she did not believe this to be true, and advised a team that developed the COBOL programming language, which she championed and furthered through the 1960s and 1970s. US Navy Rear-Admiral Grace Murray Hopper died in 1992.
Having fattened IBM on government grants for decades, the Department of Justice launched an antitrust suit against the corporation in 1969. This initiative was suddenly withdrawn by the Reagan administration in 1982—as the company once again jolted the industry by jumping into the PC market.
As for UNIVAC, its complex birth 60 years ago remains the moment when we discovered that computers were going to be part of our lives—that they were going to become integral our work and collective imagination. It was also a moment when information systems developers and entrepreneurs learned that innovation and genius are not always a match for influence and organizational scale.
"Howard Aiken was wrong," historian Paul Cerruzi wrote in 2000. "There turned out to be a market for millions of electronic digital computers by the 1990s." Their emergence awaited advances in solid state physics. Nonetheless, "the nearly ubiquitous computers of the 1990s are direct descendants of what Eckert and Mauchly hoped to commercialize in the late 1940s."
Further reading
Most of the material in this essay comes from Kurt W. Beyer's must-read book, Grace Hopper and the Invention of the Information Age (MIT Press). Also essential is Paul E. Ceruzzi's History of Modern Computing.
Friday, September 16. 2011
Data Analytics: Crunching the Future
The technicians at SecureAlert’s monitoring center in Salt Lake City sit in front of computer screens filled with multicolored dots. Each dot represents someone on parole or probation wearing one of the company’s location-reporting ankle cuffs. As the people move around a city, their dots move around the map. “It looks a bit like an animated gumball machine,” says Steven Florek, SecureAlert’s vice-president of offender insights and knowledge management. As long as the gumballs don’t go where they’re not supposed to, all is well.
The company works with law enforcement agencies around the U.S. to keep track of about 15,000 ex-cons, meaning it must collect and analyze billions of GPS signals transmitted by the cuffs each day. The more traditional part of the work consists of making sure that people under house arrest stay in their houses. But advances in the way information is collected and sorted mean SecureAlert isn’t just watching; the company says it can actually predict when a crime is about to go down. If that sounds like the “pre-cogs”—crime prognosticators—in the movie Minority Report, Florek thinks so, too. He calls SecureAlert’s newest capability “pre-crime” detection.
Using data from the ankle cuffs and other sources, SecureAlert identifies patterns of suspicious behavior. A person convicted of domestic violence, for example, might get out of jail and set up a law-abiding routine. Quite often, though, SecureAlert’s technology sees such people backslide and start visiting the restaurants or schools or other places their victims frequent. “We know they’re looking to force an encounter,” Florek says. If the person gets too close for comfort, he says, “an alarm goes off and a flashing siren appears on the screen.” The system doesn’t go quite as far as Minority Report, where the cops break down doors and blow away the perpetrators before they perpetrate. Rather, the system can call an offender through a two-way cellphone attached to the ankle cuff to ask what the person is doing, or set off a 95-decibel shriek as a warning to others. More typically, the company will notify probation officers or police about the suspicious activity and have them investigate. Presumably with weapons holstered. “It’s like a strategy game,” Florek says. (BeforeBloomberg Businessweek went to press, Florek left the company for undisclosed reasons.)
It didn’t used to be that a company the size of SecureAlert, with about $16 million in annual revenue, could engage in such a real-world chess match. For decades, only Fortune 500-scale corporations and three-letter government agencies had the money and resources to pull off this kind of data crunching. Wal-Mart Stores (WMT) is famous for using data analysis to adjust its inventory levels and prices. FedEx (FDX) earned similar respect for tweaking its delivery routes, while airlines and telecommunications companies used this technology to pinpoint and take care of their best customers. But even at the most sophisticated corporations, data analytics was often a cumbersome, ad hoc affair. Companies would pile information in “data warehouses,” and if executives had a question about some demographic trend, they had to supplicate “data priests” to tease the answers out of their costly, fragile systems. “This resulted in a situation where the analytics were always done looking in the rearview mirror,” says Paul Maritz, chief executive officer of VMware (VMW). “You were reasoning over things to find out what happened six months ago.”
In the early 2000s a wave of startups made it possible to gather huge volumes of data and analyze it in record speed—à la SecureAlert. A retailer such as Macy’s (M) that once pored over last season’s sales information could shift to looking instantly at how an e-mail coupon for women’s shoes played out in different regions. “We have a banking client that used to need four days to make a decision on whether or not to trade a mortgage-backed security,” says Charles W. Berger, CEO of ParAccel, a data analytics startup founded in 2005 that powers SecureAlert’s pre-crime operation. “They do that in seven minutes now.”
Now a second wave of startups is finding ways to use cheap but powerful servers to analyze new categories of data such as blog posts, videos, photos, tweets, DNA sequences, and medical images. “The old days were about asking, ‘What is the biggest, smallest, and average?’?” says Michael Olson, CEO of startup Cloudera. “Today it’s, ‘What do you like? Who do you know?’ It’s answering these complex questions.”
The big bang in data analytics occurred in 2006 with the release of an open-source system called Hadoop. The technology was created by a software consultant named Doug Cutting, who had been examining a series of technical papers released by Google (GOOG). The papers described how the company spread tremendous amounts of information across its data centers and probed that pool of data for answers to queries. Where traditional data warehouses crammed as much information as possible on a few expensive computers, Google chopped up databases into bite-size chunks and sprinkled them among tens of thousands of cheap computers. The result was a lower-cost and higher-capacity system that lots of people can use at the same time. Google uses the technology throughout its operations. Its systems study billions of search results, match them to the first letters of a query, take a guess at what people are looking for, and display suggestions as they type. You can see the bite-size nature of the technology in action on Google Maps as tiny tiles come together to form a full map.
Cutting created Hadoop to mimic Google’s technology so the rest of the world could have a way to sift through massive data sets quickly and cheaply. (Hadoop was the name of his son’s toy elephant.) The software first took off at Web companies such as Yahoo! (YHOO) and Facebook and then spread far and wide, with Walt Disney (DIS), the New York Times, Samsung, and hundreds of others starting their own projects. Cloudera, where Cutting, 48, now works, makes its own version of Hadoop and has sales partnerships withHewlett-Packard (HPQ) and Dell (DELL).
Dozens of startups are trying to develop easier-to-use versions of Hadoop. For example, Datameer, in San Mateo, Calif., has built an Excel-like dashboard that allows regular business people, instead of data priests, to pose questions. “For 20 years you had limited amounts of computing and storage power and could only ask certain things,” says Datameer CEO Stefan Groschupf. “Now you just dump everything in there and ask whatever you want.” Top venture capital firms Kleiner Perkins Caufield & Byers and Redpoint Ventures have backed Datameer, while Accel Partners, Greylock Partners, and In-Q-Tel, the investment arm of the CIA, have helped finance Cloudera.
Past technology worked with data that fell neatly into rows and columns—purchase dates, prices, the location of a store. Amazon.com (AMZN), for instance, would use traditional systems to track how many people bought a certain type of camera and for what price. Hadoop can handle data that don’t fit into spreadsheets. That ability, combined with Hadoop’s speedy divide-and-conquer approach to data, lets users get answers to questions they couldn’t even ask before. Retailers can dig into not just what people bought but why they bought it. Amazon can (and does) analyze its website logs to see what other items people look at before they buy that camera, how long they look at them, whether certain colors on a Web page generate more sales—and synthesize all that into real-time intelligence. Are they telling their friends about that camera? Is some new model poised to be the next big hit? “These insights don’t come super easily, but the information is there, and we do have the machine power now to process it and search for it,” says James Markarian, chief technology officer at data specialist Informatica (INFA).
Take the case of U.S. Xpress Enterprises, one of the largest private trucking companies. Through a device installed in the cabs of its 10,000-truck fleet, U.S. Xpress can track a driver’s location, how many times the driver has braked hard in the last few hours, if he sent a text message to the customer saying he would be late, and how long he rested. U.S. Xpress pays particular attention to the fuel economy of each driver, separating out the “guzzlers from the misers,” says Timothy Leonard, U.S. Xpress CTO. Truckers keep the engines running and the air conditioning on after they’ve pulled over for the night. “If you have a 10-hour break, we want your AC going for the first two hours at 70 degrees so you can go to sleep,” says Leonard. “After that, we want it back up to 78 or 79 degrees.” By adjusting the temperature, U.S. Xpress has lowered annual fuel consumption by 62 gallons per truck, which works out to a total of about $24 million per year. Less numerically, the company’s systems also analyze drivers’ tweets and blog posts. “We have a sentiment dashboard that monitors how they are feeling,” Leonard says. “If we see they hate something, we can respond with some new software or policies in a few hours.” The monitoring may come off as Big Brotherish, but U.S. Xpress sees it as key to keeping its drivers from quitting. (Driver turnover is a chronic issue in the trucking business.)
How are IBM (IBM) and the other big players in the data warehousing business responding to all this? In the usual way: They’re buying startups. Last year, IBM bought Netezza for $1.7 billion. HP, EMC (EMC), and Teradata (TDC) have also acquired data analytics companies in the past 24 months.
It’s not going too far to say that data analytics has even gotten hip. The San Francisco offices of startup Splunk have all the of-the-moment accoutrements you’d find at Twitter or Zynga. The engineers work in what amounts to a giant living room with pinball machines, foosball tables, and Hello Kitty-themed cubes. Weekday parties often break out—during a recent visit, it was Mexican fiesta. Employees were wearing sombreros and fake moustaches while a dude near the tequila bar played the bongos.
Splunk got its start as a type of nuts-and-bolts tool in data centers, giving administrators a way to search through data tied to the low-level operations of computers and software. The company indexes “machine events”—the second-by-second records produced by computing devices to keep track of their actions. This could include records of every time a server stores information, or it could be the length of a cell phone call and what type of handset was used. Splunk helps companies search through this morass, looking for events that caused problems or stood out as unusual. “We can see someone visit a shopping website from a certain computer, see that they got an error message while on the lady’s lingerie page, see how many times they tried to log in, where they went after, and what machine in some far-off data center caused the problem,” says Erik Swan, CTO and co-founder of Splunk. While it started as troubleshooting software for data centers, the company has morphed into an analysis tool that can be aimed at fine-tuning fraud detection systems at credit-card companies and measuring the success of online ad campaigns.
A few blocks away from Splunk’s office are the more sedate headquarters of IRhythm Technologies, a medical device startup. IRhythm makes a type of oversize, plastic band-aid called the Zio Patch that helps doctors detect cardiac problems before they become fatal. Patients affix the Zio Patch to their chests for two weeks to measure their heart activity. The patients then mail the devices back to IRhythm’s offices, where a technician feeds the information into Amazon’s cloud computing service. Patients typically wear rivals’ much chunkier devices for just a couple of days and remove them when they sleep or shower—which happen to be when heart abnormalities often manifest. The upside of the waterproof Zio Patch is the length of time that people wear it—but 14 days is a whole lot of data.
IRhythm’s Hadoop system chops the 14-day periods into chunks and analyzes them with algorithms. Unusual activity gets passed along to technicians who flag worrisome patterns to doctors. For quality control of the device itself, IRhythm uses Splunk. The system monitors the strength of the Zio Patch’s recording signals, whether hot weather affects its adhesiveness to the skin, or how long a patient actually wore the device. On the Zio Patch manufacturing floor, IRhythm discovered that operations at some workstations were taking longer than expected. It used Splunk to go back to the day when the problems cropped up and discovered a computer glitch that was hanging up the operation.
Mark Day, IRhythm’s vice-president of research and development, says he’s able to fine-tune his tiny startup’s operations the way a world-class manufacturer like Honda Motor (HMC) or Dell could a couple years ago. Even if he could have afforded the old-line data warehouses, they were too inflexible to provide much help. “The problem with those systems was that you don’t know ahead of time what problems you will face,” Day says. “Now, we just adapt as things come up.”
At SecureAlert, Florek says that despite the much-improved tools, extracting useful meaning from data still requires effort—and in his line of work, sensitivity. If some ankle-cuff-wearing parolee wanders out-of-bounds, there’s a human in the process to make a judgment call. “We are constantly tuning our system to achieve a balance between crying wolf and catching serious situations,” he says. “Sometimes a guy just goes to a location because he got a new girlfriend.”
Wednesday, September 14. 2011
Botnet rentals reveal the darker side of the cloud
Via InfoWorld
-----
The operators of the TDSS botnet are renting out access to infected computers for anonymous Web activities
Cloud computing isn't just opening up new opportunities for legitimate organizations worldwide; it's also proving a potential boon for cyber criminals as it inexpensively and conveniently puts disposal powerful computing resources at their fingertips, which helps them quickly and anonymously do their dirty deeds.
Among the latest examples of this unfortunate trend comes via Kaspersky Labs: The company has reported that the operators of TDSS, one of the world's largest, most sophisticated botnets, are renting out infected computers to would-be customers through the awmproxy.net storefront. Not only has TDSS developed a convenient Firefox add-on, it's accepting payment via PayPal, MasterCard, and Visa, as well as e-currency like WebMoney and Liberty Reserve.
Also known as TDL-4, the TDSS malware employs a rootkit to infect Windows-based systems, allowing outsiders to use affected machines to anonymously surf the Web, according to Kaspersky researchers Sergey Golobanov and Igor Soumenkov. The malware also removes some 20 malicious programs from host PCs to sever communication with other bot families. (Evidently, botnet operators are becoming increasingly competitive with one another.)
According to the researchers, the operators of TDSS are effectively offering anonymous Internet access as a service for about $100 per month. "For the sake of convenience, the cyber criminals have also developed a Firefox add-on that makes it easy to toggle between proxy servers within the browser," they reported.
According to Golovanov, once machines are infected, a component called socks.dll notifies awmproxy.net that a new proxy is available for rent. Soon after, the infected PC starts to accept proxy requests.
Notably, Kapersky does offer a utility to remove TDSS dubbed TDSSKiller.
This isn't the first instance of an organization making expansive cloud-based systems available to potential ne'er-do-wells, though it's arguably among the most brazen examples. Amazon Web Services have proven possible to exploit to pull off cheap brute-force attacks and could be abused for other unsavory deeds as well, such as spam propagation.
Microsoft Windows 8 Complete Guide
Via SlashGear
By Chris Burns
-----
During a lovely September week in 2011, Microsoft Windows 8 was announced and launched for developers. The event this launch occurred at was what Microsoft was presenting as a welcome to Windows 8, especially in regards to the 5,000 developers at BUILD, launching the platform with there eyes directly fixed on applications, the whole situation a large opportunity for developers. This is the beginning of Windows 8 as it exists in a sense that there’s no product launch here from Microsoft, instead there’s an opportunity for 3rd party developers to get on board here right at the start of the next-wave OS. What lies beneath is a living document which takes what Microsoft Windows 8 is at the start here in 2011 and how it will evolve over time.

Three years ago was when Windows 7 launched, since then 450 million copies have sold. Inside September 2011, the amount of users using Windows 7 has finally trumped the amount of users using Windows XP on the consumer market. Microsoft tells us they know this because they’re working with the numbers coming from machines hitting the Windows Update Service. As with any update to a new version of a major operating system, one must ask a similar question as – and you’ll have to allow me to nerd out for a moment here – Alan Bradley from TRON when he asked what changes had REALLY been made to the system that Microsoft would find it necessary to give it a whole new number.
Turns out 1,502 product changes have been made to Windows XP since Microsoft released it to manufacturing, these all being non-security updates. Improvements galore! Now what does this mean for Windows 8? Does it mean that the software will be continuously updated as the folks at Microsoft see ways to improve it? Of course, that’s a given. How many changes have been made between the Windows XP and Windows 7 we’ve known between their inception date and this end-of-summer 2011 timeframe where Windows 8 is released? That’s a number we’ll have to figure out on our own.
Reimagining Windows
Microsoft brings you Windows 8 as a operating system that is said to improve everything they brought forth in Windows 7, and what’s more, every bit of software that runs currently on Windows 7 will be able to run on Windows 8 without a problem.
Chipsets
ARM chips equal integrated engineering. Where X86, Microsoft says, was the same for every system, ARM chips are optimized for unique situations. Like what Microsoft says about software made for working on Windows 7 now also working on Windows 8, so too does everything they present here work on ARM chips.

Boldness
What’s so bold about Windows 8 is that they’re envisioning an operating system that scales from small form factors, keyboardless tablets, all the way up to gigantic servers running hundreds of processors.
Julie Larson Green, Corporate Vice President of the Windows Experience at Microsoft noted during the week of the reveal of Windows 8 that they had started planning Windows 8 in June of 2009, before they even shipped Windows 7 out the door. Of course changes in both industry and technology spark change, and in this mobile landscape and move by many from one platform to another and/or the adoption of several platforms happening by the public, Microsoft planned accordingly. Microsoft wanted to top the release of Windows 7, but they did not want to do it in a way that was either linear or reactive – this being an interesting goal of course at that time as the idea of a tablet computer simply wasn’t a reality at the time – so what is there to react to?
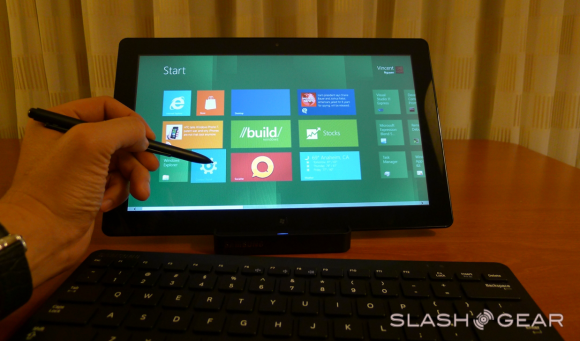
In Windows 7 there were studies on form factor, user action models, and best of all touch. Microsoft has noted that they were the first group to add touch to a major operating system. As you know well, since that time, touch has all but consumed the mobile market, and recent developments in non-mobile computing have trended toward touch as well to a degree. With this, the demand for developers to create apps for every single little function, one by one, this showing itself prevalently again on mobile, but non-mobile beginning to take back what is theirs in the recent past as well with on-device app stores on all machines. These are only two of a whole slew of points Microsoft touched on during the BUILD conference showing off the first real look at Windows 8 in September of 2011.
Tablets and PCs
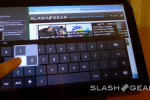
You begin with a lockscreen (seen at the top of this post). This screen doesn’t look unlike what you’re used to with Windows Phone devices, giving you pre-opening updates about time, date, updates, and of course its all displayed with a background of your choice. One of the new ideas Microsoft has to make this experience unique is “Picture Password”.

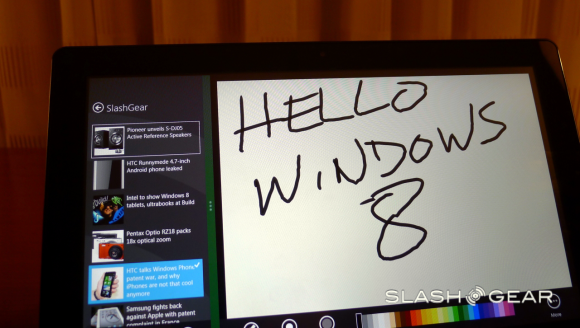
What Picture Password consists of is a specific photo or digital image that, when you see it, you’ll know to draw a certain combination of shapes and lines on your display. If you draw the correct combination, you will be logged in. Circles and lines are what’s at play here – perhaps drawing a hat on a squirrel will be your password combo?
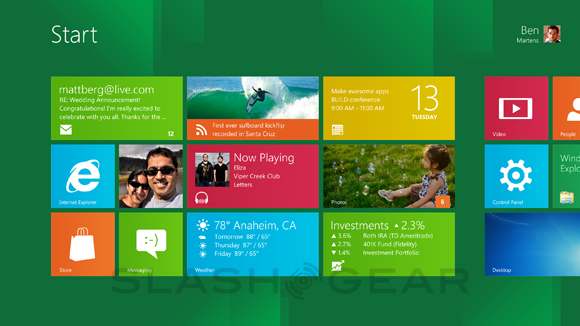
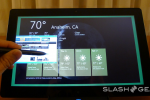
Then there’s a Start Screen. This is the place where you’ll return all the time before and after moving to other screens and apps. You’ll again recognize the look of this space as being a rather Windows Phone experience, and as each app is represented by what Microsoft calls a “tile”, you’ll certainly feel at home if you’re an avid Windows Phone user. Each tile has the ability to show off different actions before its activated to reveal the app inside, movement and, for example, feeds showing social networking news. The “serendipity of the web” has here been brought into Windows.
Tiles can express essentially anything you want and are themselves resizable and customizable. Tiles can open up to apps or they can sit by themselves and work. There are “groups” that can hold tiles “like folders” as they say, and there’s a new feature called “Semantic Zoom.” What this Semantic Zoom does is to pull you back from your interface in a way that you’ve never been able to do on a Windows device before. Fast and fluid touch language throughout, allowing you access to all of your media, all of your content, all of your apps at once.
We got hands-on with the first Windows 8 tablet at BUILD 2011 as well, see the video unboxing and hands-on here:
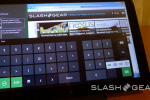
Metro-Style Apps
There is a new kind of app called Metro-Style Apps. The first thing that makes a Metro-Style app what it is full immersion. What Windows has done here is to change what they’ve done in the past, that is adding widgets and “doodads” all around the majority of apps and is now being a bit more humble, letting the app take the show.
Any app on Windows Phone 8 can be turned into a Secondary Tile. You can, for instance, “pin” a webpage to your Start Screen – in this case you’ll have all the same features your original app had, here because this is a webpage and your original app was a web-based app, you’re able to see a changing feed straight from your desktop.
Charms
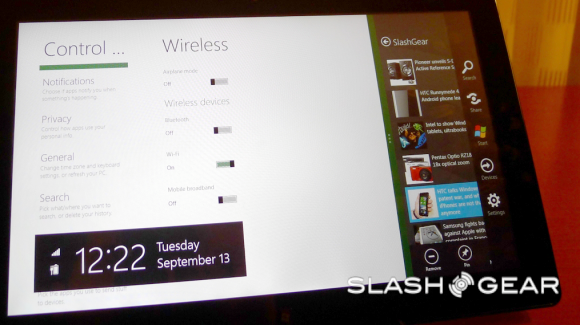
Charms are next – what this feature, activated by a swipe across your screen, is comprised of several icons, these depending on the app or location inside your system you are at. This may seem intuitive to those of you who’ve been using computers for years and years now, but as software engineers make the transition between mobile and stationary OS being separate to being one in the same, it’s little points like this that make all the difference.
What Microsoft is showing us here in Windows 8 is their next step towards a singularity in operating systems. Moving in and out of apps, shutting them down and opening them up, and even having more than one application open and working at once on the same page. This again is something that desktop mobile operating systems have been able to do for many years now, but as mobile moves into the fold, this is a big step taken.
Windows Key
There’s a button, be it physical or on the screen, wherever, that will always bring you back to your Start Screen. This is your Windows Key. If you’re using a Windows 8 tablet, you’ll likely have a physical or haptic-feedback-filled Windows Key. If you’re using a device with no physical keys, the Windows Key will be in some sneaky places for you to access.
Windows Store
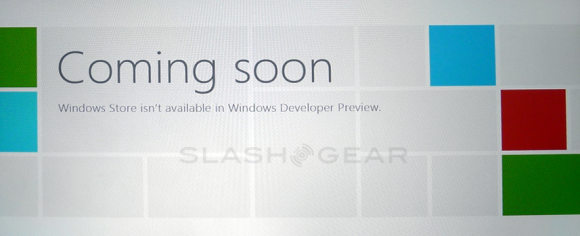
For developers (who will be mentioned many more times before this guide is through), it’s the newly minted Windows Store that should be paid attention to. Windows users will be able to access this store for apps anywhere Windows is sold worldwide. Go wild!
Apps
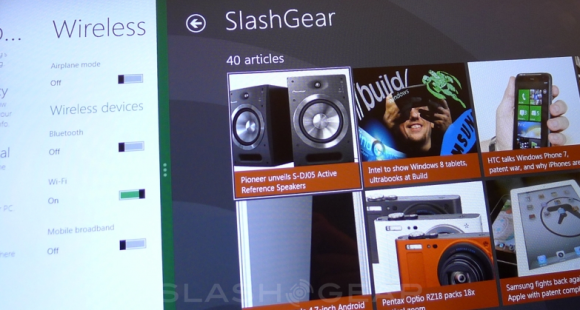
Microsoft feels that all apps should be able to work together, all of this without any extra work done by the developers of the apps in question. One of the most obvious “contracts” this connectedness will be working on is sharing. Have a bit of content you’d like to share? Grab your Charms, hit the Share Charm, and share it through, for example, “Friend Share.” Here you’re able to contact your contacts through a huge variety of ways – share and go! The data package is taken by one app and sent to another app, all of this possible with any set of apps that have sharing activated.
Sharing can happen from any app in Windows.
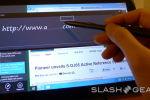
Search is next, it being one the most essential bits in any successful computer system, operating systems a must. The Search Charm is present in quite a few apps and in the system to search files. You expect Windows to know how to search files, but here we’ve got a few new options, one of them being autocomplete of options if you like. You search your term and you get results PLUS you get a list of apps that are able to also search themselves. Search a term and find results on your own computer, then search through your web app, search a social networking site, search anything that supports search.
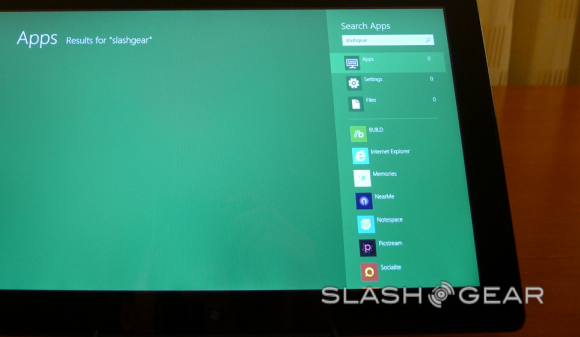
A hypothetical situation for this ability to search and select content from a variety of apps and services is if you’re creating an album of photos on a website. You can search from your local device, your app which seeks photos you’ve got on a cloud on the internet, and an app that seeks photos on your local network. Grab em all without having to launch every single app, all at once with search only. The selling point, if I may be so bold here, is that the apps are what makes up the system. Just like console video game systems, inkjet printers, and… well… every home computer in history, essentially, this system relies on the apps that it runs to run. That’s the promotion in part.

Spellcheck, auto-correct, “squiggle” underlining of words to show you they’re not necessarily understood by the system as English (or whatever language(s) you’ve got running). All of this is what you remember it as being from your current and past tens of years on your Windows machine – all of it’s intact here and is available free as part of Microsoft’s dealings with third party app developers. The same is true of the on-screen touch keyboard keyboard.
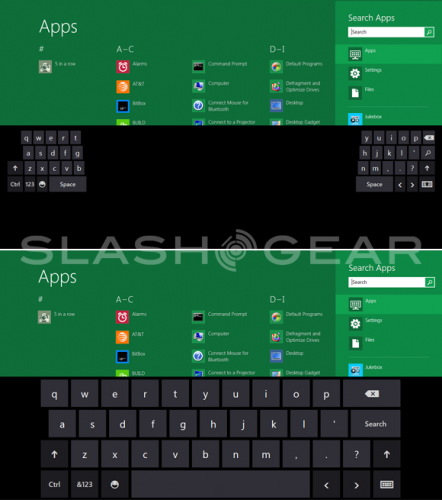
Measuring Style Device App / Connections
As you may well know by now, computers of all types, most recently mobile devices like tablets are able to connect to a plethora of other devices via Bluetooth, HDMI cable, USB, and a bunch of other slightly less popular means right this moment. In Windows 8, these connections will be handled by your Charms. Much in the same way that selecting File-Print works in most Windows systems now (though I’m sure some developers would disagree), you’re able to hit a charm, hit print, and if you like, work with a selection of settings. This interface has another name: Measuring Style Device App.
What a Measuring Style Device App does is represent a device in the system. This could be compared, if you wish, to drivers provided by manufacturers for specific devices, instead here it’s a whole new entity called a MSDA (for short) and has the ability to bring you a large set of options in, for example, a Charm.
Internet Explorer 10
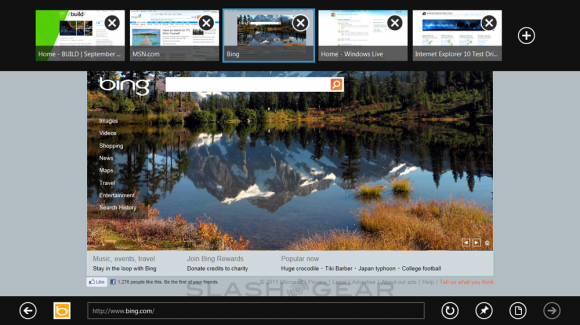
The newest version of IE aka Internet Explorer will be available as a metro-style app. Full screen action for you lovers of your monitors with all of the same hardware acceleration (even more than IE 9 does), same performance and better, same compliance and standards as IS and better, same security and same privacy as IE 9. But it’s better, better I tell you! Here you’ve got a totally immersive mode like with the other metro-style apps, and you’ve got four big gestures that, like with a lot of the rest of your system here, do the following:
Top to Bottom: Use the User Interface, in this case see your controls for webpages.
Right Side: Charms.
Left Side: Go back.
Of course you can create new tabs including the forever helpful “private” tab, you can travel to webpages, go back and forth, and use the internet in the same sort of hands-off way that all great web browsers work with. Internet Explorer 10 is able to go full screen and will, with gestures, be able to access the same lovely menus many other Windows 8 optimized apps will be able to as well.
Whispers of Photoshop
Adobe’s photo editing app has become so well known and used that an edited photo in our modern world is better known as having been “Photoshopped” than it is as having been “modified” or “photo manipulated”. We know this week at BUILD 2011 that Windows 8 will work with Photoshop on a touch platform. This isn’t the first time we’ve seen Adobe bring a Photoshop branded app to a mobile platform, but it is the first time we’ve seen what appears very much to be a full-fledged Photoshop app that, as you know from above, will be able to work with keyboard and mouse, but will here be able to work with touch in a way that’s only been available through third party touchscreen displays and drawing pads. What we can hope for is a much more optimized experience in the near future.
Pen (Stylus)

Handwriting, drafting, and graphic arts are promoted in Windows 8 by a new optimization and integration of the pen, or the stylus as you may call it. You may use pen with touch at the same time and you may navigate the whole system with pen as well. Much in the same way that the on-screen keyboard, the physical mouse, and the physical keyboard are all supported for 3rd party developers by Microsoft, so too is the Pen. Get your drawing hand out and try to remember what it was like to use a pencil!
Cloud Connections
Windows 8 will have the ability to work with online clouds of information, developers at Microsoft keeping in mind that this new operating system is most certainly going to be used to access the connected web on many levels and with many different devices and types of devices. Microsoft gives one of the most obvious reasons for this: what if you reach an awesome level on your favorite game, then you’ve got to switch to a new device? You’d have to start over if it wasn’t for the idea of cloud computing – all that information can be stored for access by multiple computers without a hassle, and Windows 8 is built with this idea deep in its heart. Settings down to the state you last left your app in can be saved to the cloud with this system. One you, one system, any number of multiple machines to work with.
Mail and Calendar
Improvements have been made to your basic Mail app on Windows 8. You’ve now got the simple addition of Folders to your Mail app, this right next to Inbox and Content. Organization is key, and the ability to place pieces of content in folders has been a tried and true way to make this happen. As far as Calendar goes, you’re now able to view more than one person’s Calendar at once. For instance if you need to see your wife’s calendar at the same time as your own to plan an event, this dual display mode can come in extremely handy.
People
There’s an app called People which organizes all the humans you know, each of the people displayed with connections to their Facebook, Linkedin, phone number, email(s), and more. This app People acts as an all-encompassing social network hub as you’re not only able to connect to People’s different profile pages on social networks, you can instant messenge them through what appears to be every single instant messenger network in existence, threads of conversation set up, organization abound. The networks take a back seat, Microsoft hopes here, to your connection to the person.
Photos

Your Photos library app connects you to your local photos as well as photos (and other types of images) you’ve got on a large number of photo hosting services and apps. This app, like the rest of the content browsing and interaction apps, appears to be working quite quickly and efficiently on every platform Microsoft is using to show off Windows 8 at BUILD 2011. This Photos app brings your photos together in a way that Microsoft hopes is easy to manifest and understand. Select photos, place them in your digital basket, and share them, only a few gestures from start to finish.
Skydrive
Connected applications is at the heart of Windows 8. Using Windows Phone, you likely know about Skydrive which allows you to place media for later editing and access from the cloud. Your Skydrive Camera Roll on Windows Phone automatically collects photos you’ve taken and uploads them to the cloud. When you’re emailing photos from your Photos app, you’ll automatically be doing so using Skydrive, this allowing you to have these photos hosted by Skydrive instead of having to pack them into the email. You’ve got the option of attaching to the email in a traditional way as well, but Skydrive gives you the ability to, in many cases, send a whole lot quicker.
Heading online to Windows Live and Skydrive will also be optimized to work with Windows 8 to give you access to any of your connected computers. For example if you’re out in the park and you meet Auntie Sue and you want to show her a picture of your half-uncle Fred but all your Fred photos are at your PC at home, you can connect to your PC at home with your mobile device by accessing Windows Live in a web browser and check your Skydrive, there’s your content.
Windows Phone
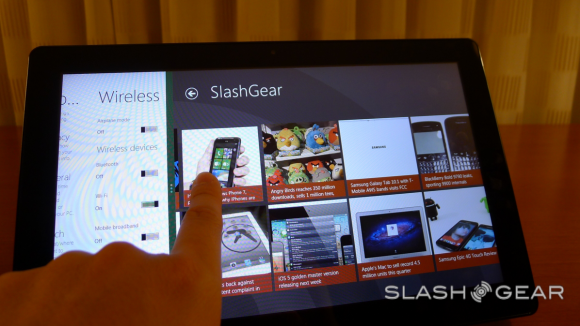
Along these same lines, syncing and cloud connectedness flows freely through Windows Phone which, at the time Windows 8 is revealed at BUILD 2011, is currently at Windows Phone 7.5 Mango. On Windows Phone here you have only to log in once and you’ve got all of your connections to your various services you
Quicksearch
Popular Entries
- The great Ars Android interface shootout (131050)
- Norton cyber crime study offers striking revenue loss statistics (101660)
- MeCam $49 flying camera concept follows you around, streams video to your phone (100062)
- Norton cyber crime study offers striking revenue loss statistics (57889)
- The PC inside your phone: A guide to the system-on-a-chip (57454)
Categories
Show tagged entries
Syndicate This Blog
Calendar
|
|
February '26 | |||||
| Mon | Tue | Wed | Thu | Fri | Sat | Sun |
| 1 | ||||||
| 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 | 21 | 22 |
| 23 | 24 | 25 | 26 | 27 | 28 | |