Entries tagged as network
Related tags
3g gsm lte mobile technology ai algorythm android apple arduino automation crowd-sourcing data mining data visualisation hardware innovation&society neural network programming robot sensors siri software web artificial intelligence big data cloud computing coding fft program amazon cloud ebook google kindle microsoft history ios iphone physical computing satellite drone light wifi botnet security browser chrome firefox ie privacy laptop chrome os os computing farm open source piracy sustainability 3d printing data center energy facebook art car flickr gui internet internet of things maps photos army camera virus social networkTuesday, October 18. 2011
The developer's guide to browser adoption rates
Via netmagazine
-----
As new platform versions get released more and more quickly, are users keeping up? Zeh Fernando, a senior developer at Firstborn, looks at current adoption rates and points to some intriguing trends
There's a quiet revolution happening on the web, and it's related to one aspect of the rich web that is rarely discussed: the adoption rate of new platform versions.
First, to put things into perspective, we can look at the most popular browser plug-in out there: Adobe's Flash Player. It's pretty well known that the adoption of new versions of the Flash plug-in happens pretty quickly: users update Flash Player quickly and often after a new version of the plug-in is released [see Adobe's sponsored NPD, United States, Mar 2000-Jun 2006, and Milward Brown’s “Mature markets”, Sep 2006-Jun 2011 research (here and here) collected by way of the Internet Archive and saved over time; here’s the complete spreadsheet with version release date help from Wikipedia].
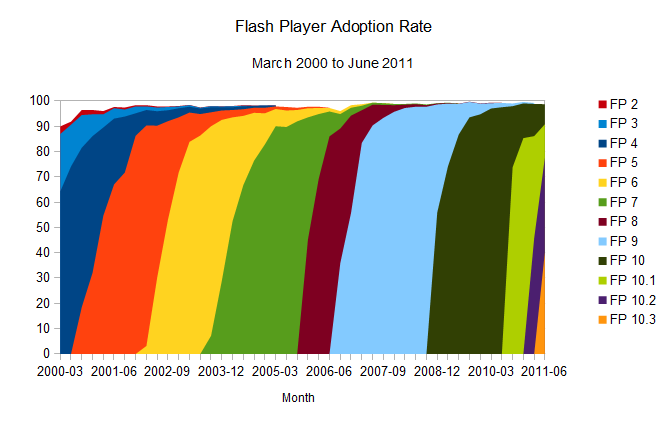
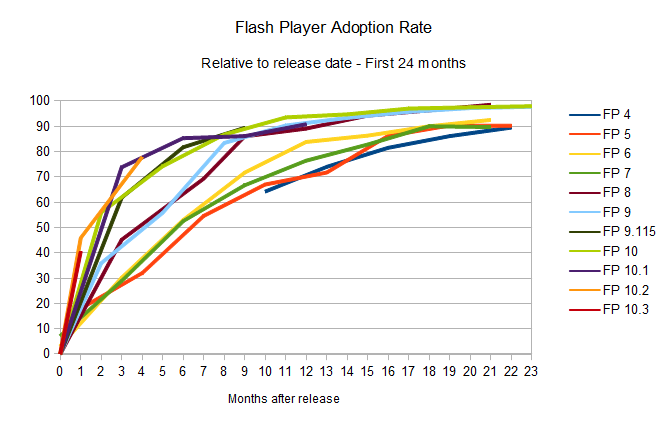
To simplify it: give it around eight months, and 90 per cent of the desktops out there will have the newest version of the plug-in installed. And as the numbers represented in the charts above show, this update rate is only improving. That’s party due to the fact that Chrome, now a powerful force in the browser battles, installs new versions of the Flash Player automatically (sometimes even before it is formally released by Adobe), and that Firefox frequently detects the user's version and insists on them installing an updated, more secure version.
Gone are the days where the Flash platform needed an event such as the Olympics or a major website like MySpace or YouTube making use of a new version of Flash to make it propagate faster; this now happens naturally. Version 10.3 only needed one month to get to a 40.5 per cent install base, and given the trends set by the previous releases, it's likely that the plug-in's new version 11 will break new speed records.
Any technology that can allow developers and publishers to take advantage of it in a real world scenario so fast has to be considered a breakthrough. Any new platform feature can be proposed, developed, and made available with cross-platform consistency in record time; such is the advantage of a proprietary platform like Flash. To mention one of the more adequate examples of the opposite effect, features added to the HTML platform (in any of its flavours or versions) can take many years of proposal and beta support until they're officially accepted, and when that happens, it takes many more years until it becomes available on most of the computers out there. A plug-in is usually easier and quicker to update than a browser too.
That has been the story so far. But that's changing.
Advertisement
Google Chrome adoption rate
Looking at the statistics for the adoption rate of the Flash plug-in, it's easy to see it's accelerating constantly, meaning the last versions of the player were finding their way to the user's desktops quicker and quicker with every new version. But when you have a look at similar adoption rate for browsers, a somewhat similar but more complex story unfolds.
Let's have a look at Google Chrome's adoption rates in the same manner I've done the Flash player comparisons, to see how many people had each of its version installed (but notice that, given that Chrome is not used by 100 per cent of the people on the internet, it is normalised for the comparison to make sense).

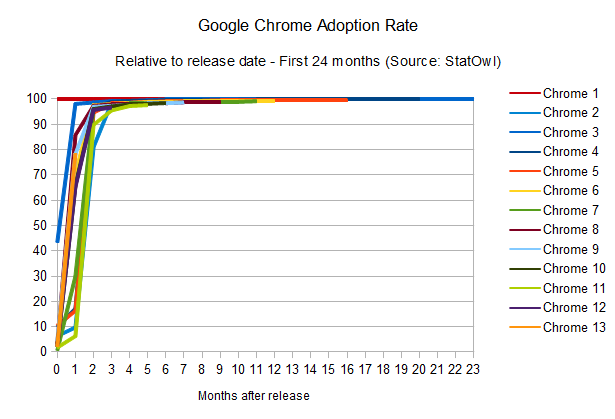
The striking thing here is that the adoption rate of Google Chrome manages to be faster than Flash Player itself [see StatOwl's web browser usage statistics, browser version release dates from Google Chrome on Wikipedia]. This is helped, of course, by the fact that updates happens automatically (without user approval necessary) and easily (using its smart diff-based update engine to provide small update files). As a result, Chrome can get to the same 90 per cent of user penetration rate in around two months only; but what it really means is that Google manages to put out updates to their HTML engine much faster than Flash Player.
Of course, there's a catch here if we're to compare that to Flash Player adoption rate: as mentioned, Google does the same auto-update for the Flash Player itself. So the point is not that there's a race and Chrome's HTML engine is leading it; instead, Chrome is changing the rules of the game to not only make everybody win, but to make them win faster.
Opera adoption rate
The fast update rate employed by Chrome is not news. In fact, one smaller player on the browser front, Opera, tells a similar story.
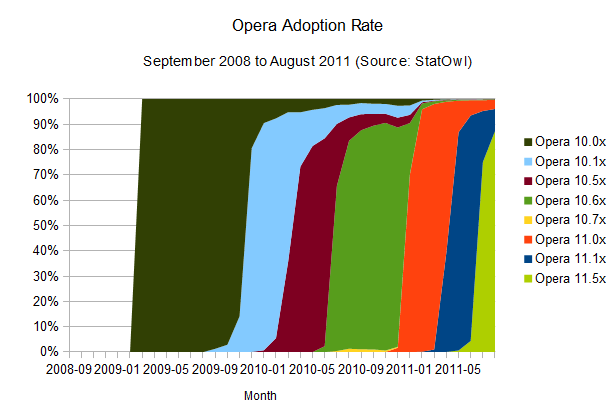

Opera also manages to have updates reach a larger audience very quickly [see browser version release dates from History of the Opera web browser, Opera 10 and Opera 11 on Wikipedia]. This is probably due to its automatic update feature. The mass updates seem to take a little bit longer than Chrome, around three months for a 90 per cent reach, but it's important to notice that its update workflow is not entirely automatic; last time I tested, it still required user approval (and Admin rights) to work its magic.
Firefox adoption rate
The results of this browser update analysis start deviating when we take a similar look at the adoption rates of the other browsers. Take Firefox, for example:
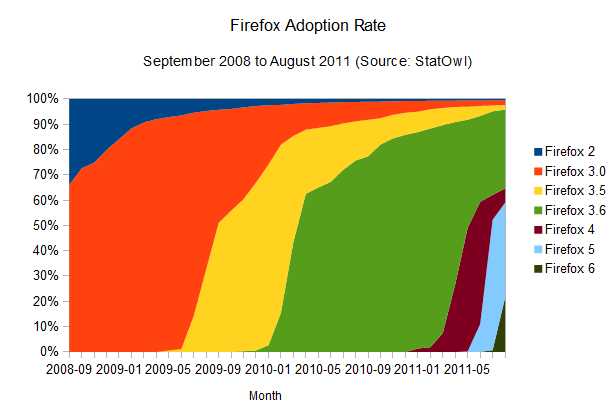
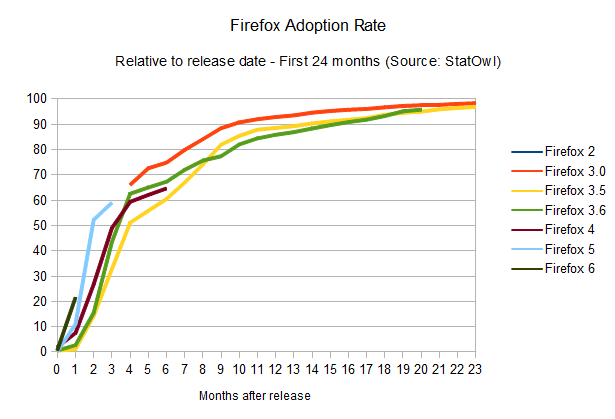
It's also clear that Firefox's update rate is accelerating (browser version release dates from Firefox on Wikipedia), and the time-to-90-per-cent is shrinking: it should take around 12 months to get to that point. And given Mozilla's decision to adopt release cycles that mimics Chrome's, with its quick release schedule, and automatic updates, we're likely to see a big boost in those numbers, potentially making the update adoption rates as good as Chrome's.
One interesting point here is that a few users seem to have been stuck with Firefox 3.6, which is the last version that employs the old updating method (where the user has to manually check for new versions), causing Firefox updates to spread quickly but stall around the 60 per cent mark. Some users still need to realise there's an update waiting for them; and similarly to the problem the Mozilla team had to face with Firefox 3.5, it's likely that we'll see the update being automatically imposed upon users soon, although they'll still be able to disable it. It's gonna be interesting to see how this develops over the next few months.
What does Apple's Safari look like?
Safari adoption rate
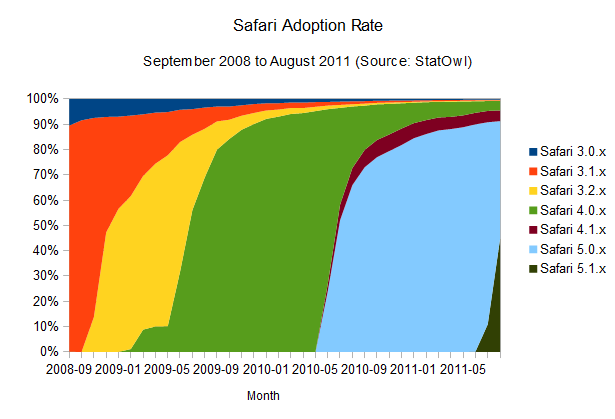
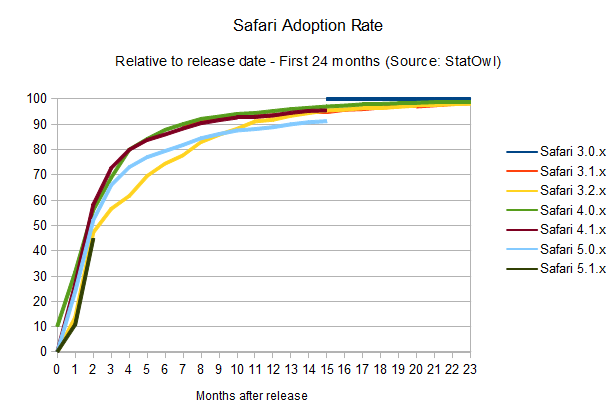
Right now, adoption rates seem on par with Firefox (browser version release dates from Safari on Wikipedia), maybe a bit better, since it takes users around 10 months to get a 90 per cent adoption rate of the newest versions of the browser. The interesting thing is that this seems to happen in a pretty solid fashion, probably helped by Apple's OS X frequent update schedule, since the browser update is bundled with system updates. Overall, update rates are not improving – but they're keeping at a good pace.
Notice that the small bump on the above charts for Safari 4.0.x is due to the public beta release of that version of the browser, and the odd area for Safari 4.1.x is due to its release in pair with Safari 5.0.x, but for a different version of OSX.
IE adoption rate
All in all it seems to me that browser vendors, as well as the users, are starting to get it. Overall, updates are happening faster and the cycle from interesting idea to a feature that can be used on a real-world scenario is getting shorter and shorter.
There's just one big asterisk in this prognosis: the adoption rate for the most popular browser out there.
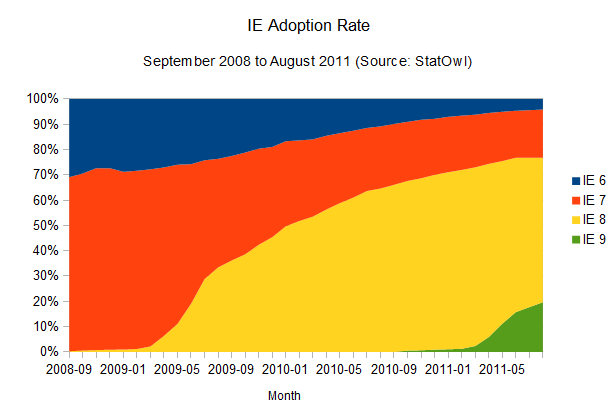
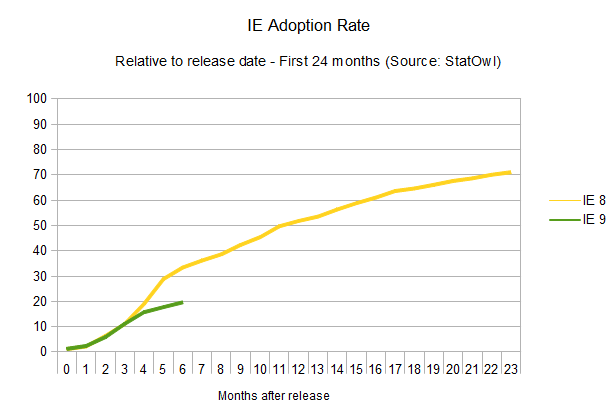
The adoption rate of updates to Internet Explorer is not improving at all (browser version release dates from Internet Explorer on Wikipedia). In fact, it seems to be getting worse.
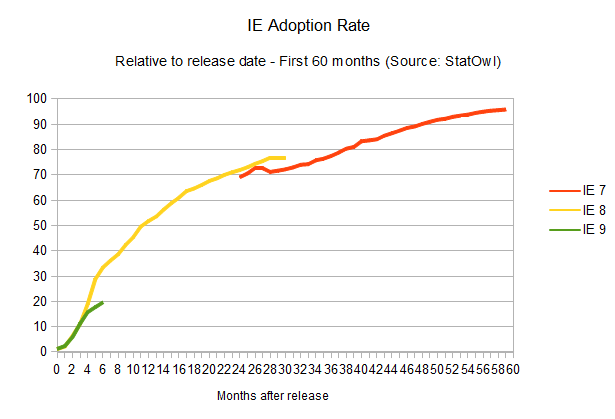
As is historically known, the adoption rate of new versions of Internet Explorer is, well, painstakingly slow. IE6, a browser that was released 10 years ago, is still used by four per cent of the IE users, and newer versions don't fare much better. IE7, released five years ago, is still used by 19 per cent of all the IE users. The renewing cycle here is so slow that it's impossible to even try to guess how long it would take for new versions to reach a 90 per cent adoption rate, given the lack of reliable data. But considering update rates haven't improved at all for new versions of the browser (in fact, IE9 is doing worse than IE8 in terms of adoption), one can assume a cycle of four years until any released version of Internet Explorer reaches 90 per cent user adoption. Microsoft itself is trying to make users abandon IE6, and whatever the reason for the version lag – system administrators hung up on old versions, proliferation of pirated XP installations that can't update – it's just not getting there.
And the adoption rates of new HTML features is, unfortunately, only as quick as the adoption rate of the slowest browser, especially when it's someone that still powers such a large number of desktops out there.
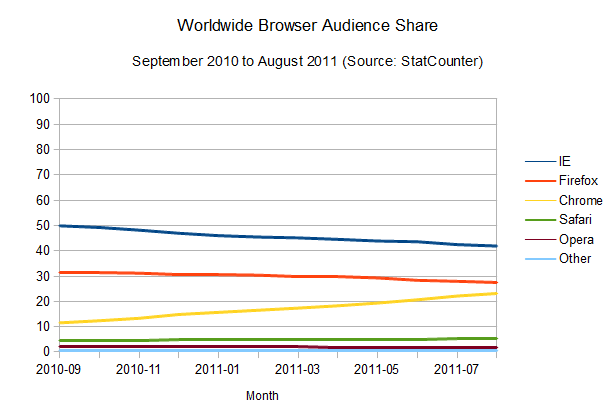
Internet Explorer will probably continue to be the most popular browser for a very long time.
The long road for HTML-based tech
The story, so far, has been that browser plug-ins are usually easier and quicker to update. Developers can rely on new features of a proprietary platform such as Flash earlier than someone who uses the native HTML platform could. This is changing, however, one browser at a time.
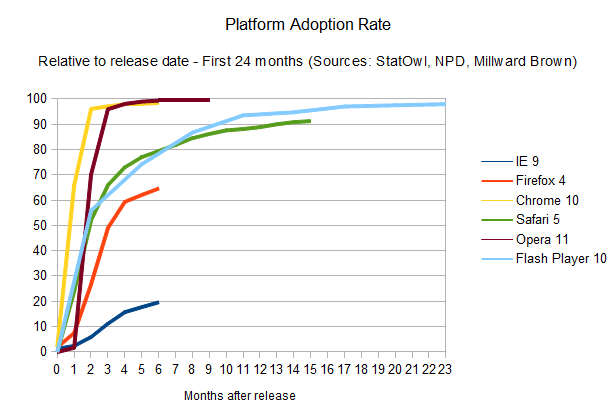
A merged chart, using the weighted distribution of each browser's penetration and the time it takes for its users to update, tells that the overall story for HTML developers still has a long way to go.
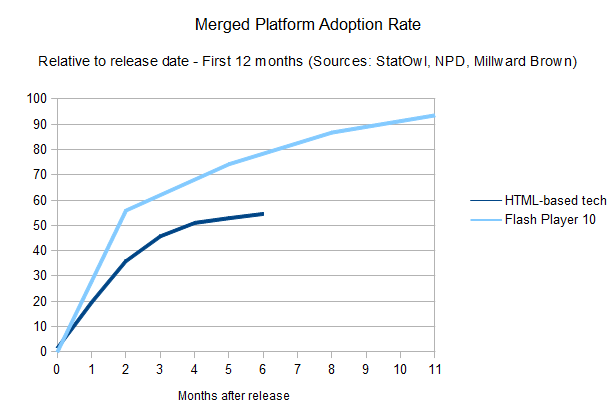
Of course, this shouldn't be taken into account blindly. You should always have your audience in mind when developing a website, and come up with your own numbers when deciding what kind of features to make use of. But it works as a general rule of thumb to be taken into account before falling in love with whatever feature has just been added to a browser's rendering engine (or a new plug-in version, for that matter). In that sense, be sure to use websites like caniuse.com to check on what's supported (check the “global user stats” box!), and look at whatever browser share data you have for your audience (and desktop/mobile share too, although it's out of the scope of this article).
Conclusion
Updating the browser has always been a certain roadblock to most users. In the past, even maintaining bookmarks and preferences when doing an update was a problem.
That has already changed. With the exception of Internet Explorer, browsers vendors are realising how important it is to provide easy and timely updates for users; similarly, users themselves are, I like to believe, starting to realise how an update can be easy and painless too.
Personally, I used to look at the penetration numbers of Flash and HTML in comparison to each other and it always baffled me how anyone would compare them in a realistic fashion when it came down to the speed that any new feature would take to be adopted globally. Looking at them this time, however, gave me a different view on things; our rich web platforms are not only getting better, but they're getting better at getting better, by doing so faster.
In retrospect, it seems obvious now, but I can only see all other browser vendors adopting similar quick-release, auto-update features similar to what was introduced by Chrome. Safari probably needs to make the updates install without user intervention, and we can only hope that Microsoft will consider something similar for Internet Explorer. And when that happens, the web, both HTML-based and plug-ins-based but especially on the HTML side, will be moving at a pace that we haven't seen before. And everybody wins with that.
Thursday, September 29. 2011
Wi-Fi networks could detect your breathing and pinpoint your location
Via dvice
-----

Well, this is a little unsettling: it turns out that Wi-Fi signals are slightly affected by people breathing, and with the right tech someone could pinpoint where you are in a room from afar using just Wi-Fi.
This was discovered when University of Utah researcher Neal Patwari was looking for a way to monitor breathing without using uncomfortable equipment. If you can track breathing using just a Wi-Fi signal, it'll make sleep studies easier for both researchers and subjects. And it worked! By laying in a hospital bed surrounded by a bunch of wireless routers, they were able to accurately estimate his breathing rate within 0.4 breaths per minute.
Now that this is known, it's only a matter of time until there's a way to detect people in rooms using Wi-Fi signals. But don't worry! If you're nervous, there's a simple solution: stop breathing.
-----
Wednesday, September 14. 2011
Botnet rentals reveal the darker side of the cloud
Via InfoWorld
-----
The operators of the TDSS botnet are renting out access to infected computers for anonymous Web activities
Cloud computing isn't just opening up new opportunities for legitimate organizations worldwide; it's also proving a potential boon for cyber criminals as it inexpensively and conveniently puts disposal powerful computing resources at their fingertips, which helps them quickly and anonymously do their dirty deeds.
Among the latest examples of this unfortunate trend comes via Kaspersky Labs: The company has reported that the operators of TDSS, one of the world's largest, most sophisticated botnets, are renting out infected computers to would-be customers through the awmproxy.net storefront. Not only has TDSS developed a convenient Firefox add-on, it's accepting payment via PayPal, MasterCard, and Visa, as well as e-currency like WebMoney and Liberty Reserve.
Also known as TDL-4, the TDSS malware employs a rootkit to infect Windows-based systems, allowing outsiders to use affected machines to anonymously surf the Web, according to Kaspersky researchers Sergey Golobanov and Igor Soumenkov. The malware also removes some 20 malicious programs from host PCs to sever communication with other bot families. (Evidently, botnet operators are becoming increasingly competitive with one another.)
According to the researchers, the operators of TDSS are effectively offering anonymous Internet access as a service for about $100 per month. "For the sake of convenience, the cyber criminals have also developed a Firefox add-on that makes it easy to toggle between proxy servers within the browser," they reported.
According to Golovanov, once machines are infected, a component called socks.dll notifies awmproxy.net that a new proxy is available for rent. Soon after, the infected PC starts to accept proxy requests.
Notably, Kapersky does offer a utility to remove TDSS dubbed TDSSKiller.
This isn't the first instance of an organization making expansive cloud-based systems available to potential ne'er-do-wells, though it's arguably among the most brazen examples. Amazon Web Services have proven possible to exploit to pull off cheap brute-force attacks and could be abused for other unsavory deeds as well, such as spam propagation.
Tuesday, September 13. 2011
Mobile Internet Users to Surpass Number of Wireline Users by 2015, Says IDC
Via DailyTech
-----
Between
2010 and 2015, the number of U.S. mobile Internet users will increase by
a compound annual growth rate of 16.6 percent while PCs and other
wireline services first stagnate, then gradually decline
The
International Data Corporation (IDC) released its Worldwide New Media Market Model (NMMM) predictions
yesterday, which forecasts that the number of people who use mobile devices to
access the Internet will significantly increase over the next few years while
wireline internet access will slowly decline.
According to the IDC's Worldwide New Media Market Model, more U.S. internet
users will access the web through mobile devices rather than through PCs or
wireline services by 2015.
Between 2010 and 2015, the number of U.S. mobile internet users will increase
by a compound annual growth rate of 16.6 percent while PCs and other wireline
services first stagnate, then gradually decline.
Globally, the number of internet users will increase from 2 billion in 2010 to
2.7 billion in 2015, as 40 percent of the world's population will have Web
access by that time. Also, global B2C e-commerce spending will increase from
$708 billion in 2010 to $1,285 billion in 2015 at a compound annual growth rate
of 12.7 percent, and worldwide online advertising will increase from $70
billion in 2010 to $138 billion in 2015.
"Forget what we have taken for granted on how consumers use the Internet," said Karsten Weide,
research vice president, Media and Entertainment. "Soon, more users will
access the Web using mobile devices than using PCs, and it's going to make the
Internet a very different place."
These
predictions may seem unsurprising, considering the fact that tech giants like
The spotlight was placed on the decline of wireline services last month
when 45,000 Verizon wireline
employees went on strike because the company had to cut pensions,
make employees pay more for healthcare, etc. in order to cut costs and
compensate for its declining wireline business.
Friday, September 09. 2011
Google -- "How our cloud does more with less"
-----

We’ve worked hard to reduce the amount of energy our services use. In fact, to provide you with Google products for a month—not just search, but Google+, Gmail, YouTube and everything else we have to offer—our servers use less energy per user than a light left on for three hours. And, because we’ve been a carbon-neutral company since 2007, even that small amount of energy is offset completely, so the carbon footprint of your life on Google is zero.
We’ve learned a lot in the process of reducing our environmental impact, so we’ve added a new section called “The Big Picture” to our Google Green site with numbers on our annual energy use and carbon footprint.
We started the process of getting to zero by making sure our operations use as little energy as possible. For the last decade, energy use has been an obsession. We’ve designed and built some of the most efficient servers and data centers in the world—using half the electricity of a typical data center. Our newest facility in Hamina, Finland, opening this weekend, uses a unique seawater cooling system that requires very little electricity.
Whenever possible, we use renewable energy. We have a large solar panel installation at our Mountain View campus, and we’ve purchased the output of two wind farms to power our data centers. For the greenhouse gas emissions we can’t eliminate, we purchase high-quality carbon offsets.
But we’re not stopping there. By investing hundreds of millions of dollars in renewable energy projects and companies, we’re helping to create 1.7 GW of renewable power. That’s the same amount of energy used to power over 350,000 homes, and far more than what our operations consume.
Finally, our products can help people reduce their own carbon footprints. The study (PDF) we released yesterday on Gmail is just one example of how cloud-based services can be much more energy efficient than locally hosted services helping businesses cut their electricity bills.
Thursday, September 08. 2011
Why Google's Offline App Strategy will Benefit Chrome OS
Via OStatic
-----
 Now
that Chromebooks--portable computers based on Google's Chrome OS--are
maturing, it's easier to gauge the prospects for Google's first-ever
operating system. As Jon Buys discussed
here on OStatic, these portables have a number of strong points.
However, there are criticisms appearing about them, too, and some of
them echo ones made here on OStatic before.
Specifically, Chrome OS imposes a very two-fisted, cloud-centric model
for using data and applications, where traditional, local storage of
data and apps is discouraged. Recently, Google has sought to close
this gap with its own apps, allowing users to work with its Gmail,
Calendar and Docs apps offline. Will these moves help boost Chrome OS
and use of Chromebooks? In enterprises, they may do so.
Now
that Chromebooks--portable computers based on Google's Chrome OS--are
maturing, it's easier to gauge the prospects for Google's first-ever
operating system. As Jon Buys discussed
here on OStatic, these portables have a number of strong points.
However, there are criticisms appearing about them, too, and some of
them echo ones made here on OStatic before.
Specifically, Chrome OS imposes a very two-fisted, cloud-centric model
for using data and applications, where traditional, local storage of
data and apps is discouraged. Recently, Google has sought to close
this gap with its own apps, allowing users to work with its Gmail,
Calendar and Docs apps offline. Will these moves help boost Chrome OS
and use of Chromebooks? In enterprises, they may do so.
Google officials have explained the logic behind allowing offline usage of key Google apps in this post, where they write:
"Today’s world doesn’t slow down when you’re offline and it’s a great feeling to be productive from anywhere, on any device, at any time. We’re pushing the boundaries of modern browsers to make this possible, and while we hope that many users will already find today’s offline functionality useful, this is only the beginning. Support for offline document editing and customizing the amount of email to be synchronized will be coming in the future. We also look forward to making offline access more widely available when other browsers support advanced functionality (like background pages)."
While Google had previously
announced its intent to deliver this offline functionality, the need for
it was undoubtedly accelerated by some of the criticisms of the way
Chrome OS forces users to work almost exclusively in the cloud. It's
also not accidental that the offline capabilities are focused on Google
applications that enterprises care about: mail, document-creation apps,
etc.
Guillermo Garron has gone so far as to reverse his previous
criticisms of Chrome OS based on the new offline functionality, as seen in his post here. He writes:
"This is something specially good for Chromebooks. Now they are not just new toys, they can be real productive tools…now Chromebooks are ready for Prime Time at least to do what they were designed for, with no limitations."Researchers at Microsoft have produced data before that shows that most people use a maximum of five software applications on a regular basis. In delivering offline functionality for mail, document creation, and other absolutely key tasks for working people, Google is hedging the cloud-only bet that it made with Chrome OS upon its debut. It's the right move for Google to be making, and is likely to help win over some enterprises that would find working exclusively in the cloud to be too limiting.
Norton cyber crime study offers striking revenue loss statistics
Via MyCE
-----
Symantec, the company behind Norton Anti-Virus, has published a startling report which estimates nearly $388 billion is lost each year to cyber crime – $274 billion in sheer wasted time, and the remaining $114 billion either spent to combat it or deposited into the bank accounts of criminals.
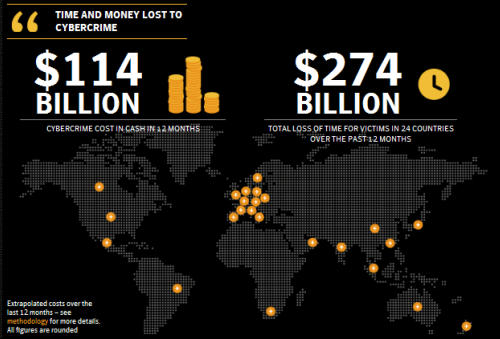
Source: Norton
According to the “Norton Cybercrime Report 2011,” viruses and malware are the “preventable yet more prevalent” methods employed by cyber criminals. Conducted earlier this year by StrategyOne, who polled 19,636 adults, kids and teachers in 24 countries, the study revealed over 54 percent of online adults have indeed encountered either threat despite the fact 59 percent incorporate active, up-to-date anti-virus software. Online scams and phishing rounded out the most common methods.
Resolving a cyber crime is also a huge hassle for those affected. Norton’s research found the entire process takes anywhere from four to 16 days depending on where you live; on average, victims spend 10 days.
“These latest cyber crime statistics reflect crime rates in the physical world, where young adults and men are more often victims of crime,” said Adam Palmer, Norton Lead Cyber Security Analyst. “Countries like South Africa and Brazil, where physical crimes against people are among the highest in the world, are clearly emerging as cyber crime capitals, too.”
China topped Norton’s list of countries most affected by cyber crime, boasting an ignominious 85 percent of adults affected. The U.S. wasn’t too far behind at 73 percent.
The fact the Internet is such a huge part of everyday life in many countries means cyber thieves have ample prey. 24 percent of respondents said that they “can’t live without the Internet,” while 41 percent “need the Internet in their everyday life.” Considering that level of dependency, it’s not too shocking that nearly 70 percent of adults reported being the victim of some form of cyber crime.
Joseph LaBrie, an Associate Professor of Psychology at Loyola Marymount University, addressed the mental state of online users and their resistance to educating or protecting themselves.
“Often, because people feel the Internet is too complicated and the threats are unknown or ambiguous, they default to a learned helplessness where they simply accept cyber crime as part of the cost of going online,” said LaBrie. “Also, they cannot visualize online protection like they can offline security systems like a fence or alarm that act as a physical deterrent.”
Norton asserts that each day cyber crime affects over one million people and that 431 million people have been victims of cyber crime in the last year alone. (via Threat Post)
-----
The study
Monday, August 29. 2011
Google TV set to launch in Europe
Via TechSpot
-----

During his keynote speech at the annual Edinburgh Television Festival last Friday, Google Executive Eric Schmidt announced plans to launch Google's TV service in Europe starting early next year.
The original launch in the United States back in October 2010 received rather poor reviews, with questions being raised regarding lack of content being available. This has seen prices slashed on Logitech set-top boxes down as low as $99 in July, with similarly poor sales of the integrated Sony Bravia Google TV models.
How much of a success Google TV will become in Europe remains to be seen, with the UK broadcasters especially concerned about the damage it could do to their existing business models. Strong competition from established companies like Sky and Virgin Media could further complicate matters for the Internet search giant.
During the MacTaggart lecture, Schmidt sought to calm the fears of the broadcasting elite, taking full advantage of the fact he was the first non-TV executive to ever be invited to present the prestigious keynote lecture at the festival.
"We seek to support the content industry by providing an open platform for the next generation of TV to evolve, the same way Android is an open platform for the next generation of mobile” said Schmidt. “Some in the US feared we aimed to compete with broadcasters or content creators. Actually our intent is the opposite…".
Much like in the United States, Google faces a long battle to convince broadcasters and major media players of its intent to help evolve TV platforms with open technologies, rather than topple them.
Google seems to have firmly set its sights on a slice of the estimated $190bn TV advertising market which will do little to calm fears, especially when you consider Google's online advertising figures for 2010 were just $28.9bn in comparison.
Thursday, August 18. 2011
Wi-Fi Security: Cracking WPA With CPUs, GPUs, And The Cloud
Is your network safe? Almost all of us prefer the convenience of Wi-Fi over the hassle of a wired connection. But what does that mean for security? Our tests tell the whole story. We go from password cracking on the desktop to hacking in the cloud.
We hear about security breaches with such increasing frequency that it's easy to assume the security world is losing its battle to protect our privacy. The idea that our information is safe is what enables so many online products and services; without it, life online would be so very different than it is today. And yet, there are plenty of examples where someone (or a group of someones) circumvents the security that even large companies put in place, compromising our identities and shaking our confidence to the core.
Understandably, then, we're interested in security, and how our behaviors and hardware can help improve it. It's not just the headache of replacing a credit card or choosing a new password when a breach happens that irks us. Rather, it's that feeling of violation when you log into your banking account and discover that someone spent funds out of it all day.
In Harden Up: Can We Break Your Password With Our GPUs?, we took a look at archive security and identified the potential weaknesses of encrypted data on your hard drive. Although the data was useful (and indeed served to scare plenty of people who were previously using insufficient protection on files they really thought were secure), that story was admittedly limited in scope. Most of us don't encrypt the data that we hold dear.
At the same time, most of us are vulnerable in other ways. For example, we don't run on LAN-only networks. We're generally connected to the Internet, and for many enthusiasts, that connectivity is extended wirelessly through our homes and businesses. They say a chain is only as strong as its weakest link. In many cases, that weak link is the password protecting your wireless network.
There is plenty of information online about wireless security. Sorting through it all can be overwhelming. The purpose of this piece is to provide clarification, and then apply our lab's collection of hardware to the task of testing wireless security's strength. We start by breaking WEP and end with distributed WPA cracking in the cloud. By the end, you'll have a much better idea of how secure your Wi-Fi network really is.
-----
Complete article/survey @tomshardware.com
Thursday, August 11. 2011
Geeks Without Frontiers Pursues Wi-Fi for Everyone
Via OStatic
-----
Recently, you may have heard about new efforts to bring online access to regions where it has been economically nonviable before. This idea is not new, of course. The One Laptop Per Child (OLPC) initiative was squarely aimed at the goal until it ran into some significant hiccups. One of the latest moves on this front comes from Geeks Without Frontiers, which has a stated goal of positively impacting one billion lives with technology over the next 10 years. The organization, sponsored by Google and The Tides Foundation, is working on low cost, open source Wi-Fi solutions for "areas where legacy broadband models are currently considered to be uneconomical."
According to an announcement from Geeks Without Frontiers:
"GEEKS expects that this technology, built mainly by Cozybit, managed by GEEKS and I-Net Solutions, and sponsored by Google, Global Connect, Nortel, One Laptop Per Child, and the Manna Energy Foundation, will enable the development and rollout of large-scale mesh Wi-Fi networks for atleast half of the traditional network cost. This is a major step in achieving the vision of affordable broadband for all."
It's notable that One Laptop Per Child is among the sponsors of this initiative. The organization has open sourced key parts of its software platform, and could have natural synergies with a global Wi-Fi effort.
“By driving down the cost of metropolitan and village scale Wi-Fi networks, millions more people will be able to reap the economic and social benefits of significantly lower cost Internet access,” said Michael Potter, one of the founders of the GEEKS initiative.
The Wi-Fi technology that GEEKS is pursuing is mesh networking technology. Specifically, open80211s (o11s), which implements the AMPE (Authenticated Mesh Peering Exchange) enabling multiple authenticated nodes to encrypt traffic between themselves. Mesh networks are essentially widely distributed wireless networks based on many repeaters throught a specific location.
You can read much more about the open80211s standard here. The GEEKS initiative has significant backers, and with sponsorship from OLPC, will probably benefit from good advice on the topic of bringing advanced technologies to disadvantaged regions of the world. The effort will be worth watching.
Quicksearch
Popular Entries
- The great Ars Android interface shootout (131083)
- Norton cyber crime study offers striking revenue loss statistics (101714)
- MeCam $49 flying camera concept follows you around, streams video to your phone (100103)
- Norton cyber crime study offers striking revenue loss statistics (57943)
- The PC inside your phone: A guide to the system-on-a-chip (57527)
Categories
Show tagged entries
Syndicate This Blog
Calendar
|
|
March '26 | |||||
| Mon | Tue | Wed | Thu | Fri | Sat | Sun |
| 1 | ||||||
| 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 | 21 | 22 |
| 23 | 24 | 25 | 26 | 27 | 28 | 29 |
| 30 | 31 | |||||


