Entries tagged as security
Thursday, July 26. 2012
Via Forbes
-----
The first crypto war revolved around the hardware-based Clipper Chip
and coercing companies to deploy broken encryption with backdoors to
enable domestic State spying. Fortunately, the good guys won.
The next crypto war is still a war of the government against its own
citizens but this time enlisting the corporations, including social
networks, as direct agents of the State. What some have dubbed Crypto Wars 2.0 manifests itself in the current litany of legislative acronyms designed to confuse and befuddle.
Sometimes I think legislative bills are named with a Twitter hashtag
in mind. Although it doesn’t always work out favorably for the name
deciders, hashtags do generally assist in the coalescing of Internet
organizers around the world. Since passage of the Cyber Intelligence Sharing and Protection Act by the U.S. House of Representatives in April, #CISPA has been everywhere. Thankfully, twin legislative initiatives SOPA and PIPA were dropped in January. Also, let’s not forget the gradual expansion of CALEA and the Lieberman-Collins Cyber Security Act and the NSA-centric McCain Cybersecurity Act.
Even the seemingly unpatriotic USA PATRIOT Act of 2001 is a garbled backronym that would make George Orwell proud: Uniting (and) Strengthening America (by) Providing Appropriate Tools Required (to) Intercept (and) Obstruct Terrorism Act.
The Electronic Frontier Foundation recently posted an FAQ
arguing that CISPA would allow companies to review and then to hand
over customers’ personal information, logs, and email to the government.
That is a fairly broad and comprehensive mandate.
What has gone largely unnoticed in this torrent of analysis, however,
is that privacy tools for individuals already exist and they have so
for many years! Quietly anticipating encroachment against basic Internet
liberties, concerned cyber privacy advocates has been coding and
releasing the tools that allow for private electronic communication and
private web surfing. Proposed legislation like CISPA may or may not pass
and become law, but if it does we have to understand the new landscape.
Your privacy is up to you!
1. Email Privacy – Naked email is like a postcard for anyone to read. Pretty Good Privacy
(PGP), an open source software program created by Phil Zimmermann in
1991, is the global standard for point-to-point encrypted and
authenticated email. Hushmail is an OpenPGP-compatible web-based email platform that does not have access to your user password for decryption. Both products, when used correctly, offer subpoena-proof email communication.
2. File Privacy – Your files might be
stored in the encrypted cloud but that doesn’t mean that they’re 100%
safe for your eyes only. Free and open-source TrueCrypt allows you to encrypt folders or entire drives locally prior to syncing with Dropbox. BoxCryptor also facilitates local file encryption prior to cloud uploading and it comes with added compatibility for Android and iOS.
There is an alternative to the dual-application process described
above. Although most cloud-based storage services transfer over an
encrypted session and store data in an encrypted form, the files are
still accessible to the service provider which makes the data vulnerable
to court-ordered subpoena. In order to rectify this, two different zero-knowledge data storage companies provide secure online data backup and syncing – SpiderOak and Wuala. For obvious reasons, there is no password recovery and employees have zero access to your data.
3. Voice Privacy – Wiretapping will become more prevalent in the days and months ahead. From the creator of PGP, Zfone is a new secure VoIP phone software product utilizing a protocol called ZRTP which lets you make encrypted phone calls over the Internet. The project’s trademark is “whisper in someone’s ear from a thousand miles away.” You can listen to Zimmermann present Zfone at DEFCON 15.
Also utilizing ZRTP, open-source Jitsi
provides secure video calls, conferencing, chat, and desktop sharing.
Because of security issues and lawful interception, Tor Project’s Jacob
Appelbaum recommends using Jitsi instead of Skype.
Designed specifically for mobile devices and utilizing ZRTP, open-source RedPhone from Whisper Systems is an application that enables encrypted voice communication between RedPhone users on Android.
4. Chat Privacy – Encrypting your chat or instant messaging sessions is just as important as encrypting your email. Cryptocat
establishes a secure, encrypted chat session that is not subject to
commercial or government surveillance. Similar to Cryptocat, the older
and more durable Off-the-record Messaging (OTR) cryptographic protocol generates new key pairs for every chat implementing a form of perfect forward secrecy and deniable encryption. It is available via Pidgin plugin.
5. Traffic Privacy – The final step in the process is geo-privacy, which refers to the protection of ‘information privacy’ with regard to geographic information. Virtual Private Networks, or VPNs, have been used consistently for anonymous web browsing and IP address masking. Just make sure that your VPN provider does not log IP addresses and that they accept a form of payment that does not link you to the transaction.
Additionally, the Tor Project
provides free software and an open network for privacy-oriented
Internet usage. Intended to protect users’ personal freedom, privacy,
and ability to conduct confidential business, Tor (The onion router) is a
system that improves online anonymity by routing Internet traffic
through a worldwide volunteer network of layering and encrypting servers
which impedes network surveillance or traffic analysis.
I encourage everyone to become familiar with these basic tools for
privacy. The important disclaimer is that in order to circumvent these
privacy technologies, your password can be obtained in a variety of ways
that are extremely intrusive and beyond the realm of casual day-to-day
usage, such as hardware keyloggers
or ceiling-mounted cameras. Furthermore, browser-based cryptography
carries the added risk of spoofed applets being delivered to your
desktop by court order or by malicious actors but this risk can be
mitigated by maintaining trusted source code locally or by verifying
compiled code against a digital signature. The mission statement from
Tor Project director Jacob Appelbaum still stands, “Make the metadata
worthless essentially for people that are surveilling you.”
Monday, April 16. 2012
Via DVICE
-----
It doesn't get much more futuristic than "universal quantum network,"
but we're going to have to find something else to pine over, since a
UQN now exists. A group from the Max Planck Institute of Quantum Optics
has tied the quantum states of two atoms together using photons, creating the first network of qubits.
A quantum network is just like a regular network, the one that you're
almost certainly connected to at this very moment. The only difference
is that each node in the network is just a single atom (rubidium atoms,
as it happens), and those atoms are connected by photons. For the first
time ever, scientists have managed to get these individual atoms to read
a qubit off of a photon, store that qubit, and then write it out onto
another photon and send it off to another atom, creating a fully
functional quantum network that has the potential to be expanded to
however many atoms we want.
How Quantum Networking Works
You remember the deal with the quantum states of atoms, right? You
know, how you can use quantum spin to represent the binary states of
zero or one or both or neither all at the same time? Yeah, don't worry,
when it comes down to it it's not something that anyone really
understands. You just sort of have to accept that that's the way it is,
and that quantum bits (qubits) are rather weird.
So, okay, this quantum weirdness comes in handy when you want to create a very specific sort of computer,
but what's the point of a quantum network? Well, if you're the paranoid
sort, you're probably aware that when you send data from one place to
another in a traditional network, those data can be intercepted en route and read by some nefarious person with nothing better to do with their time.
The cool bit about a quantum network is that it offers a way
to keep a data transmission perfectly secure. To explain why this is
the case, let's first go over how the network functions. Basically,
you've got one single atom on one end, and other single atom on the
other end, and these two atoms are connected with a length of optical
fiber through which single photons can travel. If you get a bunch of
very clever people with a bunch of very expensive equipment together in a
room with one of those atoms, you can get that atom to emit a photon
that travels down the optical fiber containing the quantum signature of
the atom that it was emitted from. And when that photon runs smack into
the second atom, it imprints it with the quantum information from the first atom, entangling the two.
When two atoms are entangled like this, it means that you can measure
the quantum state of one of them, and even though the result of your
measurement will be random, you can be 100% certain that the quantum
state of the other one will match it. Why and how does this work? Nobody
has any idea. Seriously. But it definitely does, because we can do it.
Quantum Lockdown
Now, let's get back to this whole secure network thing. You've got a
pair of entangled atoms that you can measure, and you'll get back a
random state (a one or a zero) that you know will be the same for both
atoms. You can measure them over and over, getting a new random state
each time you do, and gradually you and the person measuring the other
atom will be able to build up a long string of totally random (but
totally identical) ones and zeros. This is your quantum key.
There are three things that make a quantum key so secure. Thing one
is that the single photon that transmits the entanglement itself cannot
be messed with, since messing with it screws up the quantum signature of
the atom that it originally came from. Thing two is that while you're
measuring your random ones and zeroes, if anyone tries to peek in and
measure your atom at the same time (to figure out your key), you'll be
able to tell. And thing three is that you don't have to send the key
itself back and forth, since you're relying on entangled atoms that
totally ignore conventional rules of space and time.*
Hooray, you've got a super-secure quantum key! To use it, you turn it
into what's called a one-time pad, which is a very old fashioned and
very simple but theoretically 100% secure way to encrypt something. A
one-time pad is just a completely random string of ones and zeros.
That's it, and you've got one of those in the form of your quantum key.
Using binary arithmetic, you add that perfectly random string of data to
the data that make up your decidedly non-random message, ending up with
a new batch of data that looks completely random. You can send
that message through any non-secure network you like, and nobody will
ever be able to break it. Ever.
When your recipient (the dude with the other entangled atom and an
identical quantum key) gets your message, all they have to do is do that
binary arithmetic backwards, subtracting the quantum key from the
encrypted message, and that's it. Message decoded!
The reason this system is so appealing is that theoretically, there are zero
weak points in the information chain. Theoretically (and we really do
have to stress that "theoretically"), an entangled quantum network
offers a way to send information back and forth with 100% confidence
that nobody will be able to spy on you. We don't have this capability
yet, but with this first operational entangled quantum network, we're
getting closer, in that all of the pieces of the puzzle do seem to
exist.
*If you're wondering why we can't use entanglement to transmit
information faster than the speed of light, it's because entangled atoms
only share their randomness. You can be sure that measuring one of them
will result in the same measurement on the other one no matter how far
away it is, but we have no control over what that measurement will be.
Wednesday, March 28. 2012
Via ars technica
-----
An Ars story from earlier this month reported that iPhones expose the unique identifiers of recently accessed wireless routers,
which generated no shortage of reader outrage. What possible
justification does Apple have for building this leakage capability into
its entire line of wireless products when smartphones, laptops, and
tablets from competitors don't? And how is it that Google, Wigle.net,
and others get away with publishing the MAC addresses of millions of
wireless access devices and their precise geographic location?
Some readers wanted more technical detail about the exposure, which
applies to three access points the devices have most recently connected
to. Some went as far as to challenge the validity of security researcher
Mark Wuergler's findings. "Until I see the code running or at least a
youtube I don't believe this guy has the goods," one Ars commenter wrote.
According to penetration tester Robert Graham, the findings are legit.
In the service of our readers, and to demonstrate to skeptics that
the privacy leak is real, Ars approached Graham and asked him to review
the article for accuracy and independently confirm or debunk Wuergler's
findings.
"I can confirm all the technical details of this 'hack,'" Graham, who
is CEO of Errata Security, told Ars via e-mail. "Apple products do
indeed send out three packets that will reveal your home router MAC
address. I confirmed this with my latest iPad 3."
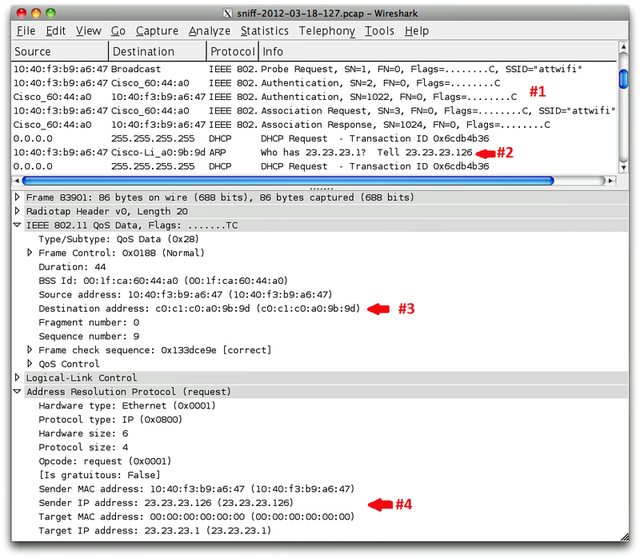
He provided the image at the top of this post as proof. It shows a
screen from Wireshark, a popular packet-sniffing program, as his iPad
connected to a public hotspot at a Starbucks in Atlanta. Milliseconds
after it connected to an SSID named "attwifi" (as shown in the section
labeled #1), the iPad broadcasted the MAC address of his Linksys home
router (shown in the section labeled #2). In section #3, the iPad sent
the MAC address of this router a second time, and curiously, the
identifier was routed to this access point even though it's not
available on the local network. As is clear in section #4, the iPad also
exposed the local IP address the iPad used when accessing Graham's home
router. All of this information is relatively simple to view by anyone
within radio range.
The image is consistent with one provided by Wuergler below. Just as
Wuergler first claimed, it shows an iPhone disclosing the last three
access points it has connected to.
Graham used Wireshark to monitor the same Starbucks hotspot when he
connected with his Windows 7 laptop and Android-based Kindle Fire.
Neither device exposed any previously connected MAC addresses. He also
reviewed hundreds of other non-Apple devices as they connected to the
network, and none of them exposed previously accessed addresses, either.
As the data makes clear, the MAC addresses were exposed in ARP (address resolution protocol)
packets immediately after Graham's iPad associated with the access
point but prior to it receiving an IP address from the router's DHCP
server. Both Graham and Wuergler speculate that Apple engineers
intentionally built this behavior into their products as a way of
speeding up the process of reconnecting to access points, particularly
those in corporate environments. Rather than waiting for a DHCP server
to issue an IP address, the exposure of the MAC addresses allows the
devices to use the same address it was assigned last time.
"This whole thing is related to DHCP and autoconfiguration (for speed
and less traffic on the wire)," Wuergler told Ars. "The Apple devices
want to determine if they are on a network that they have previously
connected to and they send unicast ARPs out on the network in order to
do this."
Indeed, strikingly similar behavior was described in RFC 4436,
a 2006 technical memo co-written by developers from Apple, Microsoft,
and Sun Microsystems. It discusses a method for detecting network
attachment in IPv4-based systems.
"In this case, the host may determine whether it has re-attached to
the logical link where this address is valid for use, by sending a
unicast ARP Request packet to a router previously known for that link
(or, in the case of a link with more than one router, by sending one or
more unicast ARP Request packets to one or more of those routers)," the
document states at one point. "The ARP Request MUST use the host MAC
address as the source, and the test node MAC address as the
destination," it says elsewhere.
Of course, only Apple engineers can say for sure if the MAC
disclosure is intentional, and representatives with the company have
declined to discuss the issue with Ars. What's more, if RFC 4436 is the
reason for the behavior, it's unclear why there's no evidence of Windows
and Android devices doing the same thing. If detecting previously
connected networks is such a good idea, wouldn't Microsoft and Google
want to design their devices to do it, too?
In contrast to the findings of Graham and Wuergler were those of Ars writer Peter Bright, who observed different behavior when his iPod touch connected to a wireless network.
While the Apple device did expose a MAC address, the unique identifier
belonged to the Ethernet interface of his router rather than the MAC
address of the router's WiFi interface, which is the identifier
cataloged by Google, Skyhook, and similar databases.
Bright speculated that many corporate networks likely behave the same
way. And for Apple devices that connect to access points with such
configurations, exposure of the MAC address may pose less of a threat.
Still, while it's unclear what percentage of wireless routers assign a
different MAC address to wired and wireless interfaces, Graham and
Wuergler's tests show that at least some wireless routers by default
make no such distinction.
Wuergler also debunked a few other misconceptions that some people
had about the wireless behavior of Apple devices. Specifically, he said
claims that iPhones don't broadcast the SSID they are looking for
from Errata Security's Graham are incorrect. Some Ars readers had
invoked the 2010 blog post from Graham to cast doubt on Wuergler's
findings
"The truth is Apple products do probe for known SSIDs (and no, there is no limit as to how many)," Wuergler wrote in a post published on Friday to the Daily Dave mailing list. He included the following screenshot to document his claim.
Connecting the dots
What all of this means is that there's good reason to believe that
iPhones and other Apple products—at least when compared to devices
running Windows or Android—are unique in leaking MAC addresses that can
uniquely identify the locations of networks you've connected to
recently. When combined with other data often exposed by virtually all
wireless devices—specifically the names of wireless networks you've
connected to in the past—an attacker in close proximity of you can
harvest this information and use it in targeted attacks.
Over the past year or so, Google and Skyhook have taken steps to make
it harder for snoops to abuse the GPS information stored in their
databases. Google Location Services, for instance, now requires the submission of two MAC addresses
in close proximity of each other before it will divulge where they are
located. In many cases, this requirement can be satisfied simply by
providing one of the other MAC addresses returned by the Apple device.
If it's within a few blocks of the first one, Google will readily
provide the data. It's also feasible for attackers to use war dialing
techniques to map the MAC addresses of wireless devices in a given
neighborhood or city.
Since Apple engineers are remaining mum, we can only guess why
iDevices behave the way they do. What isn't in dispute is that, unlike
hundreds of competing devices that Wuergler and Graham have examined,
the Apple products leak connection details many users would prefer to
keep private.
A video demonstrating the iPhone's vulnerability to fake access point attacks is here. Updated to better describe video.
Image courtesy of Robert Graham, Errata Security
Monday, January 23. 2012
Via eurekalert
-----
Researchers have succeeded in combining the power of quantum
computing with the security of quantum cryptography and have shown that
perfectly secure cloud computing can be achieved using the principles of
quantum mechanics. They have performed an experimental demonstration of
quantum computation in which the input, the data processing, and the
output remain unknown to the quantum computer. The international team of
scientists will publish the results of the experiment, carried out at
the Vienna Center for Quantum Science and Technology (VCQ) at the
University of Vienna and the Institute for Quantum Optics and Quantum
Information (IQOQI), in the forthcoming issue of Science.
Quantum computers are expected to play an important role in future
information processing since they can outperform classical computers at
many tasks. Considering the challenges inherent in building quantum
devices, it is conceivable that future quantum computing capabilities
will exist only in a few specialized facilities around the world – much
like today's supercomputers. Users would then interact with those
specialized facilities in order to outsource their quantum computations.
The scenario follows the current trend of cloud computing: central
remote servers are used to store and process data – everything is done
in the "cloud." The obvious challenge is to make globalized computing
safe and ensure that users' data stays private.
The latest research, to appear in Science, reveals that
quantum computers can provide an answer to that challenge. "Quantum
physics solves one of the key challenges in distributed computing. It
can preserve data privacy when users interact with remote computing
centers," says Stefanie Barz, lead author of the study. This newly
established fundamental advantage of quantum computers enables the
delegation of a quantum computation from a user who does not hold any
quantum computational power to a quantum server, while guaranteeing that
the user's data remain perfectly private. The quantum server performs
calculations, but has no means to find out what it is doing – a
functionality not known to be achievable in the classical world.
The scientists in the Vienna research group have demonstrated the
concept of "blind quantum computing" in an experiment: they performed
the first known quantum computation during which the user's data stayed
perfectly encrypted. The experimental demonstration uses photons, or
"light particles" to encode the data. Photonic systems are well-suited
to the task because quantum computation operations can be performed on
them, and they can be transmitted over long distances.
The process works in the following manner. The user prepares qubits –
the fundamental units of quantum computers – in a state known only to
himself and sends these qubits to the quantum computer. The quantum
computer entangles the qubits according to a standard scheme. The actual
computation is measurement-based: the processing of quantum information
is implemented by simple measurements on qubits. The user tailors
measurement instructions to the particular state of each qubit and sends
them to the quantum server. Finally, the results of the computation are
sent back to the user who can interpret and utilize the results of the
computation. Even if the quantum computer or an eavesdropper tries to
read the qubits, they gain no useful information, without knowing the
initial state; they are "blind."
The research at the Vienna Center for
Quantum Science and Technology (VCQ) at the University of Vienna and at
the Institute for Quantum Optics and Quantum Information (IQOQI) of the
Austrian Academy of Sciences was undertaken in collaboration with the
scientists who originally invented the protocol, based at the University
of Edinburgh, the Institute for Quantum Computing (University of
Waterloo), the Centre for Quantum Technologies (National University of
Singapore), and University College Dublin.
Publication: "Demonstration of Blind Quantum Computing"
Stefanie Barz, Elham Kashefi, Anne Broadbent, Joseph Fitzsimons, Anton Zeilinger, Philip Walther.
DOI: 10.1126/science.1214707
Wednesday, September 14. 2011
Via InfoWorld
-----
The operators of the TDSS botnet are renting out access to infected computers for anonymous Web activities
Cloud computing isn't just opening up new opportunities for
legitimate organizations worldwide; it's also proving a potential boon
for cyber criminals as it inexpensively and conveniently puts disposal
powerful computing resources at their fingertips, which helps them
quickly and anonymously do their dirty deeds.
Among the latest examples of this unfortunate trend comes via Kaspersky Labs:
The company has reported that the operators of TDSS, one of the world's
largest, most sophisticated botnets, are renting out infected computers
to would-be customers through the awmproxy.net storefront. Not only has
TDSS developed a convenient Firefox add-on, it's accepting payment via
PayPal, MasterCard, and Visa, as well as e-currency like WebMoney and Liberty Reserve.
Also
known as TDL-4, the TDSS malware employs a rootkit to infect
Windows-based systems, allowing outsiders to use affected machines to
anonymously surf the Web, according to Kaspersky researchers Sergey Golobanov and Igor Soumenkov.
The malware also removes some 20 malicious programs from host PCs to
sever communication with other bot families. (Evidently, botnet
operators are becoming increasingly competitive with one another.)
According
to the researchers, the operators of TDSS are effectively offering
anonymous Internet access as a service for about $100 per month. "For
the sake of convenience, the cyber criminals have also developed a
Firefox add-on that makes it easy to toggle between proxy servers within
the browser," they reported.
According to Golovanov, once
machines are infected, a component called socks.dll notifies
awmproxy.net that a new proxy is available for rent. Soon after, the
infected PC starts to accept proxy requests.
Notably, Kapersky does offer a utility to remove TDSS dubbed TDSSKiller.
This
isn't the first instance of an organization making expansive
cloud-based systems available to potential ne'er-do-wells, though it's
arguably among the most brazen examples. Amazon Web Services have proven
possible to exploit to pull off cheap brute-force attacks and could be abused for other unsavory deeds as well, such as spam propagation.
Thursday, August 18. 2011
Is your network safe? Almost all of us prefer the convenience
of Wi-Fi over the hassle of a wired connection. But what does that mean
for security? Our tests tell the whole story. We go from password
cracking on the desktop to hacking in the cloud.
We hear about security breaches with
such increasing frequency that it's easy to assume the security world is
losing its battle to protect our privacy. The idea that our information
is safe is what enables so many online products and services; without
it, life online would be so very different than it is today. And yet,
there are plenty of examples where someone (or a group of someones)
circumvents the security that even large companies put in place,
compromising our identities and shaking our confidence to the core.

Understandably, then, we're interested in security, and how our
behaviors and hardware can help improve it. It's not just the headache
of replacing a credit card or choosing a new password when a breach
happens that irks us. Rather, it's that feeling of violation when you
log into your banking account and discover that someone spent funds out
of it all day.
In Harden Up: Can We Break Your Password With Our GPUs?,
we took a look at archive security and identified the potential
weaknesses of encrypted data on your hard drive. Although the data was
useful (and indeed served to scare plenty of people who were previously
using insufficient protection on files they really thought were secure),
that story was admittedly limited in scope. Most of us don't encrypt
the data that we hold dear.
At the same time, most of us are vulnerable in other ways. For
example, we don't run on LAN-only networks. We're generally connected to
the Internet, and for many enthusiasts, that connectivity is extended
wirelessly through our homes and businesses. They say a chain is only as
strong as its weakest link. In many cases, that weak link is the
password protecting your wireless network.
There is plenty of information online about wireless security.
Sorting through it all can be overwhelming. The purpose of this piece
is to provide clarification, and then apply our lab's collection of
hardware to the task of testing wireless security's strength.
We start by breaking WEP and end with distributed WPA cracking in the
cloud. By the end, you'll have a much better idea of how secure your
Wi-Fi network really is.
-----
Complete article/survey @tomshardware.com
|