
Thursday, April 24. 2014
Giant photoshop eraser sticks to london streets
Via designboom
-----

two creatives behind the ‘street eraser‘ blog are merging the digital world with the analog, sticking their adobe-inspired art throughout london’s urban fabric. the giant playful labels illustrate the familiar grey and white checkerboard pattern, visible when using the eraser tool in photoshop. eliminating graffitti from traffic signs, color from mailboxes and portions of billboards, the intervention seemingly reveals a concealed world beneath our own. the team says of the digital tool interrupting everyday surroundings, ‘we rather like the idea that it’s hiding under the surface of everything around us.’




Smile! New tech creates 3D mug shots from DNA
Via Tech Times
-----

Virtual 3D faces can now be produced from DNA code. The application,
developed by Mark Shriver of Pennsylvania State University, produces a
virtual mug shot of potential criminals. Pictured here is a work flow
diagram showing how facial features were processed for the application.
(Photo : PLOS ONE)
Models of a criminal's face may so be generated from any trace of DNA left at the scene of a crime. Computer-generated 3D maps will show exactly how the suspect would have looked from an angle.
Mark Shriver of Pennsylvania State University and his team developed the application, which produces a virtual mug shot of potential criminals.
Shriver and his team took 3D images of almost 600 volunteers, coming from a wide range of racial and ethnic groups. They superimposed more than 7,000 digital points of reference on the facial features and recorded the exact position of each of those markers. These grids were used to measure how the facial features of a subject differ from the norm. For instance, they would quantify the distance between the eyes of a subject, and record how much more narrow or wide they were than average.
A computer model was created to see how facial features were affected by sex, genes and race. Each of the study participants were tested for 76 genetic variants that cause facial mutations. Once corrected for race and sex, 20 genes with 24 variants appeared to reliably predict facial shape.
"Results on a set of 20 genes showing significant effects on facial features provide support for this approach as a novel means to identify genes affecting normal-range facial features and for approximating the appearance of a face from genetic markers," the researchers wrote in the article announcing the results.
As part of data collection, the team asked participants to rate faces based on perceived ethnicity, as well as gender.
Digital facial reconstructions from DNA have proven to be notoriously unreliable. Even seemingly simple information like height can be difficult to determine through genetic analysis. Other aspects of human physiology, such as eye color, are easier to predict using genetic analysis.
"One thing we're certain of [is] there's no single gene that suddenly makes your nose big or small," Kun Tang, from the Shanghai Institutes for Biological Sciences in China, said.
In order to further refine the system, Shriver has already started sampling more people. Adding further diversity to the database should allow the application to make even more accurate recreations of a person's face. In the next round of testing, 30,000 different points will be used instead of 7,000. Merging this development with 3D printers would make it possible to print out 3D models of a person, just based on a piece of DNA.
Such models - digital or physical - are not likely to be used in courts anytime soon. A more likely scenario is use as modern day version of police sketches, assisting police in finding suspects. Only after an arrest would the DNA of a suspect be compared to that collected at the scene of a crime.
Creating 3D facial models from genetic evidence was detailed in Nature.
Wednesday, April 23. 2014
New Drone Can Hack Into Your Smartphone To Steal Usernames And Passwords
Via Think Progress
-----

CREDIT: AP – Mel Evans
A new hacker-developed drone can lift your smartphone’s private data from your GPS location to mobile applications’ usernames and passwords — without you ever knowing. The drone’s power lies with a new software, Snoopy, which can turn a benign video-capturing drone into a nefarious data thief.
Snoopy intercepts Wi-Fi signals when mobile devices try to find a network connection. London researchers have been testing the drone and plan to debut it at the Black Hat Asia cybersecurity conference in Singapore next week. Snoopy-equipped drones can aid in identity theft and pose a security threat to mobile device users.
Despite its capabilities, the drone software project was built to raise awareness and show consumers how vulnerable their data is to theft, Glenn Wilkinson, a Sensepost security researcher and Snoopy’s co-creator, told CNN Money.
As a part of its controversial surveillance programs, the U.S. National Security Agency already uses similar technology to tap into Wi-Fi connections and control mobile devices. And even though Snoopy hasn’t hit the market, phone-hacking drones could become a reality in the United States now that a federal judge recently overturned the U.S. Federal Aviation Administration’s commercial drone ban. Because the ban was lifted, filmmakers and tech companies such as Facebook and Amazon are now allowed to fly drones — be it to increase Web access or deliver packages — for profit.
Before latching onto a Wi-Fi signal, mobile devices first check to see if any previously connected are nearby. The Snoopy software picks up on this and pretends to be one of those old network connections. Once attached, the drone can access all of your phone’s Internet activity. That information can tell hackers your spending habits and where you work.
With the right tools, Wi-Fi hacks are relatively simple to pull off, and are becoming more common. Personal data can even be sapped from your home’s Wi-Fi router. And because the number of Wi-Fi hotspots keeps growing, consumers must take steps, such as using encrypted sites, to protect their data.
Data breaches overall are happening more often. Customers are still feeling the effect of Target’s breach last year that exposed more than 100 million customers’ personal data. But as smartphones increasingly becoming the epicenter of personal data storage, hacks targeting the device rather than individual apps pose a greater privacy and security threat.
According to a recent Pew Research study, about 50 percent of Web users publicly post their birthday, email or place of work — all of which can be used in ID theft. Nearly 25 percent of people whose credit card information is stolen also suffer identity theft, according to a study published by Javelin Strategy & Research of customers who received data breach notifications in 2012. Moreover, most people manage about 25 online accounts and only use six passwords, quadrupling the potential havoc from one account’s password breach.
Wednesday, April 09. 2014
The NSA is burning down the web, but what if we rebuilt a spy-proof internet?
Via The guardian
-----

What will life be like after the internet? Thanks to the mass surveillance undertaken by the National Security Agency and the general creepiness of companies like Google and Facebook, I've found myself considering this question. I mean, nothing lasts forever, right?
There's a broad tech backlash going on right now; I wonder just how deep the disillusionment runs. I get the feeling that there are folks out there who would relish putting the internet behind us sooner rather than later. Imagine that: even the internet could be a thing of the past one day. What would that be like? No Facebook. No Google. No government nerds looking through your webcam.
But could we become more secure without abandoning the internet? What if there's a third way? One that doesn't involve either passive resignation to being exploited or a Luddite smash-the-looms fantasy. What if we began to develop and encourage the adoption of machines and a network that are actually secure – through which neither thieves, corporations, nor the NSA could track us – and what if these could be configured by us, to really do what we want them to do? To stop the spying, stealing and monitoring, but to allow other things to continue.
What would that look like?
A problem: maybe the internet wasn't built to be secure
We all know by now that the NSA and the UK's Government Communication Headquarters are reading our emails, listening to our phone conversations, storing our metadata and using our computers and phones to watch us. A bunch of dorky guys amassing huge collections of pictures of tits and dicks. Here they are, hard at work, protecting us:

I know I feel safer now! Happy viewing, guys! If we had any doubts before, now we know that the government doesn't trust us – so very many of us – and we certainly don't trust it.
Meanwhile, thieves have managed to get their hands on more than 100 million credit card numbers and PINs from Target and Neiman Marcus. Lots of cyber thieves operate in the former Soviet republics, so maybe that new sports car in Baku or that night on the town in Sofia is courtesy of your hard-earned savings.
It's not just the government and thieves who take advantage of the web's weird combination of opacity and insecurity; Google, Apple, Facebook, Microsoft and other tech companies repurpose our phones and tablets into tracking and monitoring devices. Google, for one, makes a lot of money gathering information from us and selling it to advertisers. The free conveniences we enjoy – email, endless web browsing, cats and all sorts of gossip – are not, in fact, free. They are merely clever trade-offs for information about you. In return for access to much of the world's knowledge, we hand over valuable personal information about everything we believe, everything we're curious about, everything we desire or fear – everything that makes us who we are, at least to the retailers, advertisers and secret government agencies on the receiving end.
It is we who are being sold.
Trading our privacy for the convenience of a Google search is not so different from giving up constitutionally protected freedoms in exchange for the "security" that our government claims to offer. At least with Google and other tech services we know we're getting something; whether we actually are more secure because of the NSA's surveillance is an unresolved question. We are frequently told that this indiscriminate data collection has produced valuable results, but those results are "secret," so you'll just have to trust the government. I'm not saying we don't need strong security measures to protect us from lunatics, but this dragnet surveillance has gone way beyond meeting that need.
Cyber thieves, for their part, don't offer the average internet user anything in return – not only that, but they make money selling information about the security gaps they find to the US government. It's an open question whether the government actually wants to patch up those holes and make the internet more secure. For now, it's in its interest to keep these holes open – available for future use, but secret. And we know how good the government is at keeping secrets.
To a lot of folks it appears that the corporations, the thieves and the government are all doing exactly the same thing: the "legal" behavior and the illegal theft are cousins. Spying and cyber theft are not freak phenomena; increasingly, they appear to be unavoidable consequences of online access as it now exists.
As the internet has become more integral to our lives, we've become more vulnerable to its seductions, and the web has started to act like a bully, a drug dealer. It knows we need it, love it and are addicted to it, so it can take advantage of that need.
Moreover, the internet is no longer even egalitarian. And that was one of the big pluses! Once it seemed that everyone had the same access to information. Soon, though, its glories will be available only to those who can afford them. Recently, Verizon won a court ruling against net neutrality, which the Federal Communications Commission has announced it will not appeal, so the way is clear for corporations to play favorites with internet traffic. Clearly this miraculous technology – developed in part with the noble ambition that nuclear scientists might communicate freely – has been perverted into something dark and disturbing.
A thought experiment: what if we broke the internet?
These deteriorating conditions feed into the rapidly growing discontent regarding the internet. What if the disillusionment eventually reaches a point at which many feel that the free services and convenience no longer compensate for the exploitation, control and surveillance? What if, one night, a small group of people decided they've had enough and say, Let's call it a day? What exactly might this imaginary band of outsiders do? Would they or could they shut down the entire internet? Is that even possible? And what would be the consequences? Now, let's be clear, I'm not advocating this, but I also don't think it's entirely outside the realm of possibility.
As we all know by now, the NSA tapped into a vast amount of international and domestic internet communications by installing devices in small rooms in data centers in San Francisco and a few other places. It didn't require an all-out assault to subvert one of these fortresses – just a small intervention with impunity and intent. Here is what the inside of one of these buildings looks like:

That's what makes it all work? My music studio isn't this messy!
The internet, it seems, is not "nowhere". There are nodes in the internet, where great amounts of data come and go, and they do have real physical locations. Intercept a few of these nodes – there are some here in downtown New York, linked to some in Lisbon, where the fiberoptic cables surface – and you can infiltrate the whole world, as the NSA knows. They needed access to only a few undistinguished buildings to get what they wanted.
So… imagine that a hypothetical group of disillusioned citizens obtains access to the same nodes – let's say it's an inside job by some building employees – but instead of tapping the nodes, as the NSA did, they break them. And to avoid any possibility of repair, they detonate a small timed radioactive paintball after they leave. No one gets hurt, but the radioactive splatter creates a no-go zone. As a result, no one can fix the fiber optics or even get near them for, let's say, 100 years. The city outside, and even the rest of the building, might remain safe, but don't go near that room on the 20th floor!
This might sound far-fetched. Surely no one can "break" the internet! The internet is our friend! And how could anyone even get into the buildings that keep it running?! But as we've seen, neither our "security" organizations nor the world's largest corporations are very good at keeping their shit secure.
OK, now, for the sake of this thought experiment…
A wasteland: what if the web as we know it didn't exist?

The internet is a thing of the past. What now?
Obviously business goes haywire, to say nothing of the profitable business of watching us. High-speed automated trading, which makes up half or more of New York's stock market activity (though the proportion is currently declining, ends. Wall Street initially crashes, but eventually it finds a new normal. (There was trading before the internet, after all.) Streaming movies and music, however, is totally over. Skyping your grandmother – over.
Google is now absolutely worthless, though it still has all its existing data housed in massive server farms. No more drones will take flight or drop bombs on Pakistan or Yemen. Cash and checks are still pretty good; credit and debit cards can't rely on internet connections to verify accounts anymore – though they still work, as they did before the web. Amazon has ceased to exist, and huge brick-and-mortar stores like Wal-Mart have lost track of their massive inventories. Small towns and bookstores make a comeback! Even record stores!
No one can unfriend you, and Mark Zuckerberg won't know what and whom you like or don't like ever again. Online courses will halt; teachers will have to teach their students face-to-face. The Singularity will be postponed.
Would the world really be a better place without the internet? Is a complete reset really necessary?
For some, the internet has offered endless moneymaking opportunities, but whether many of the web's touted benefits end up reaching the majority of people is debatable. More and more, it seems that only a minority are making a fortune off what was extolled as a universally liberating technology.
To be fair, the internet offers some egalitarian benefits, besides pictures of cats. There's the well-publicized assistance it lends to movements for human rights and democracy and the instantaneously accessible forum it provides for much of the world's knowledge. Truth be told, the internet didn't actually create any of those movements or that knowledge, but it has certainly empowered a lot of previously voiceless people who now have access to them.
It's hard to weigh the worth of the internet because we can't even imagine life without it. We've internalized it. It's part of us, which explains why we are exploited so easily online. Is the internet a cancer killing us little by little or a wonderful cybernetic extension of our brains? Let's say we wanted to rid ourselves of the cancer. Would the cure be catastrophic or would the liberation be worth it?
A utopia: what would a revised internet look like?

To be honest, I have a hard time imagining internet 2.0. I'm old enough to remember the utopian enthusiasm that greeted the internet when it emerged 20 years ago. We can't go back – we know too much now – but maybe we can learn from what we loved about the internet back then. Namely, its egalitarian nature – that homemade and small-scale sites were just as accessible as the emerging e-commerce platforms. It was a pleasant, chaotic jumble. Can we revive the feeling of a souk and lose the big-box store feel?
Some folks have advocated that the internet be considered a utility. A "necessary" part of our lives like water, electricity or gas. It might be better to have some fair regulation than to let market forces shape the landscape. Can you imagine if corporations owned our water supply?
Imagine this: in a new internet, we'd still be able to send emails. Academic and nonprofit institutions would still share resources online. Wikipedia and web-based journalism would still exist. But if we can't be tracked as we are now, a lot would change. Google would lose its primary sources of revenue – ads – and return to being a very good search engine, with a lot fewer employees. The NSA and the other data thieves and collectors would be helpless. No one would have data on countless innocent citizens that could be repurposed to God knows what ends. The Chinese couldn't hack into the North American power grid.
All that money that was poured into online surveillance programs could of course now be spent on health and education (I did say "could" – I'm being very optimistic). That would actually increase security – worldwide. It's pretty well accepted that extreme poverty breeds terrorism. Offering attractive alternatives to extremism that lead to better lives is the way to win the "war on terror". Guns, drones and mass surveillance do the opposite: they actually breed terrorism. If we have the imagination to rethink both network security and national security – and that's a big if – then the whole world would have the opportunity to become safer, no matter what the US government claims.
Is there a will to change?
Let's assume that such a secure network structure is technically possible. internet 2.0 for real. Even if it is technically possible, I have a feeling that it might take a lot of willpower to walk away from the tit of convenience. Corporations and governments have built massive economic and political systems based on our accepting things as they are, and they will fight powerfully against any reforms.
What could make that surge of willpower come into existence? The information-hoovering in which corporations engage is of a kind with the government surveillance; in both cases we are prey to distant agendas. The three forms of data-gathering (if one includes cyber crime) are all connected – and none of them make us happier or more secure.
Reassessing what makes us secure might be a start. Real, life-long security comes not from the barrel of a gun or from being able to spy on your fellow citizens like a Stasi informant; it comes with less harsh extremes of wealth and poverty and increased access to health care and education. Embracing the security that comes with a more robust democracy is far preferable to other incentives to change, like all our credit cards becoming worthless or the NSA leaking incriminating webcam pictures of its critics. Before a catastrophic collapse like my hypothetical one ever comes, let's find it within ourselves to give up some convenience and become a little more human.
Tuesday, April 08. 2014
Google's Project Loon balloon goes around the world in 22 days
Via PCWorld
-----

When Jules Verne wrote Around the World in Eighty Days, this probably isn’t what he had in mind: Google’s Project Loon announced last week one of its balloons had circumnavigated the Earth in 22 days.
Granted, we’re not talking a grand tour of the world here: The balloon flew in a loop over the open ocean surrounding Antarctica, starting at New Zealand. According to the Project Loon team, it was the latest accomplishment for the balloon fleet, which just achieved 500,000 kilometers of flight.
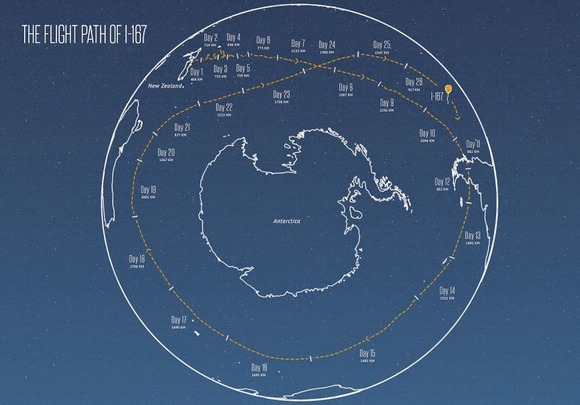 IMAGE: GOOGLE
IMAGE: GOOGLEWheeeeeeee...!
While it may seem like fun and games, Project Loon’s larger goal is to use high-altitude balloons to “connect people in rural and remote areas, help fill coverage gaps, and bring people back online after disasters.”
Currently, the project is test-flying balloons to learn more about wind patterns, and to test its balloon designs. In the past nine months, the project team has used data it’s accumulated during test flights to “refine our prediction models and are now able to forecast balloon trajectories twice as far in advance.”
It also modified the balloon’s air pump (which pumps air in and out of the balloon) to operate more efficiently, which in turn helped the balloon stay on course in this latest test run.
Project Loon’s next step toward universal Internet connection is to create “a ring of uninterrupted connectivity around the 40th southern parallel,” which it expects to pull off sometime this year.
Tuesday, March 25. 2014
Google joins Global Alliance for Genomics and Health
Via Slash Gear
-----

Google has made clear their intent on joining the Global Alliance for Genomics and Health, a worldwide organization dedicated to standards, policies, and technology for the greater good of human health. Google’s role in this group will be to contribute toward refining technology and evolving the health research ecosystem for the whole planet.
Google will also be submitting open-source projects based on a web-based API to "import, process, store, and search genomic data at scale." In doing so, Google is submitting a proposal for this "simple web-based API" alongside a full preview implementation. This implementation will be utilizing the API built on Google’s cloud infrastructure, and will include sample data from public datasets galore.
The Google Genomics API will focus on the following from the start:
• Focus on science, not servers and file formats
- Use simple web APIs to access data wherever it lives
- Let us manage the servers and disks
• Store genomic data securely
- Private data remains private, public data is available to the community anywhere
- Storage space expands to fit your research needs
• Process as much data as you need, all at once
- Import data for entire cohorts in parallel
- Search and slice data from many samples in a single query
At the moment, potential users are being granted access to the Genomics API through a access request process. This process is done through Google itself, but may one day be hosted by the Global Alliance for Genomics and Health.

Google suggests that they are at the beginning of a big change in the global health and healthcare environment, and asks that other Global Alliance for Genomics and Health members contact them to "share your ideas about how to bring data science and life science together."
Monday, March 24. 2014
WiFi capability embedded in 68% of all consumer electronics sold in the US
Via Slash Gear
-----

Just about every electronic device that we buy today has WiFi hardware embedded inside. Our game consoles like the PS3, PS4, Xbox One, and portable devices all ship with wireless connectivity. Strategy Analytics has issued a new report that shows 68% of all consumer electronics devices sold in the US now include WiFi capability.
When the report is expanded to look at the entire world, 57% of all consumer electronics devices have WiFi embedded. There are 4 billion WiFi enabled devices in use around the world today. Breaking that down, Strategy Analytics says that is about seven WiFi equipped devices for every home.
Looking around my house, I have more devices that that with multiple smartphones, game consoles, tablets, DVRs with WiFi, and more. It’s easy to see how 4 billion WiFi devices can be in use around the world. The research firm predicts that by 2017 there will be over 7 billion WiFi devices in use globally.
The most common WiFi equipped devices on the market are mobile phones and tablets. Those two product categories account for 59% of all WiFi enabled CE devices shipped in 2013. Mobile PCs is the next biggest category accounting for 9% of WiFi devices shipped. The massive difference in percentage between mobile phones and tablets compared to mobile computers makes sense with the computer market on the decline. Key growth areas for WiFi moving forward will be in cameras, wireless audio speakers, smart TVs and DVRs according to Strategy Analytics.
Friday, March 07. 2014
Scientists develop a lie detector for tweets
Via The Telegraph
-----

The Twitter logo displayed on a smart phone Photo: PA
Scientists have developed the ultimate lie detector for social media – a system that can tell whether a tweeter is telling the truth.
The creators of the system called Pheme, named after the Greek mythological figure known for scandalous rumour, say it can judge instantly between truth and fiction in 140 characters or less.
Researchers across Europe are joining forces to analyse the truthfulness of statements that appear on social media in “real time” and hope their system will prevent scurrilous rumours and false statements from taking hold, the Times reported.
The creators believe that the system would have proved useful to the police and authorities during the London Riots of 2011. Tweeters spread false reports that animals had been released from London Zoo and landmarks such as the London Eye and Selfridges had been set on fire, which caused panic and led to police being diverted.
Kalina Bontcheva, from the University of Sheffield’s engineering department, said that the system would be able to test information quickly and trace its origins. This would enable governments, emergency services, health agencies, journalists and companies to respond to falsehoods.
Tuesday, March 04. 2014
Should Students Be Able To Take Coding Classes For Language Credits?
Via Gizmodo
-----

The Kentucky Senate just passed a law that will let students take computer programming classes to satisfy their foreign language requirements. Do you think that's a good move?
What this new law means is, rather than taking three years of Spanish or French or whatever, kids can choose to learn to code. Sure, whether it's Java or German, they're both technically languages. But they're also two very different skills. You could easily argue that it's still very necessary for students to pick up a few years of a foreign tongue—though, on the other hand, coding is a skill that's probably a hell of a lot more practically applicable for today's high school students.
I, for one, have said countless times that if I could travel through time, I probably would have taken some computer science classes in college. Too late now, but not for Kentucky teenagers. So what do you think of this new law?
Image by Olly/Shutterstock
Monday, March 03. 2014
Osaka train station set for large face-recognition study
Via PCWorld
-----

Japan’s Osaka Station could become another focal point in the global battle over personal privacy protection as a Japanese research center prepares for a long-term face-recognition study there.
The independent research group National Institute of Information and Communications Technology (NICT) plans to begin the experiment in April to study crowd movements in order to better plan for emergency procedures during disasters.
The train station is western Japan’s busiest, with an average of 413,000 passengers boarding trains there every day. Over a million people use it and neighboring Umeda Station daily.
NICT will deploy cameras in Osaka Station and the adjacent Osaka Station City, a multipurpose complex, that can track faces as they move around the premises. The cameras will be separate from any security cameras that are already installed by operator West Japan Railway (JR West), a spokesman for the railway said.
"The purpose of the study is to determine whether or not sensor data on crowd movements can be used to validate the safety measures of emergency exits for when a disaster strikes,” a NICT spokesperson said.
JR West referred all questions about the protection of passenger privacy to NICT, but the research institute said the experiment was still being prepared.
"At this time, we are considering the technology to be used to obtain statistics on crowd flows,” the NICT spokesman said. “Depending on the technique used, the data that can be obtained on pedestrian flows will be different. So, it’s difficult to say how many people could be subject (to the experiment).”
NICT would not elaborate on technical aspects of the study, but it said previously that it is slated to run for two years and will involve about 90 cameras and 50 servers.
It said the facial-recognition system can track dozens of points on a face. It emphasized that the data cannot be used to identify people and it will abide by Japan’s Personal Information Protection Law when handling it.
The NICT spokesperson said the institute is not aware of any similar large-scale study.
A report in the Yomiuri Shimbun newspaper said computers linked to the cameras will run face-recognition algorithms and assign IDs to faces, which will be tracked for a week.
The dozens of cameras would be able to track the movements of people the algorithms recognize, and record whether they go to a coffee shop or through a ticket gate, for instance.
The technology under consideration for the study can identify faces with an accuracy of 99.99 percent, according to the report.
Quicksearch
Popular Entries
- The great Ars Android interface shootout (131054)
- Norton cyber crime study offers striking revenue loss statistics (101667)
- MeCam $49 flying camera concept follows you around, streams video to your phone (100065)
- Norton cyber crime study offers striking revenue loss statistics (57896)
- The PC inside your phone: A guide to the system-on-a-chip (57461)
Categories
Show tagged entries
Syndicate This Blog
Calendar
|
|
February '26 | |||||
| Mon | Tue | Wed | Thu | Fri | Sat | Sun |
| 1 | ||||||
| 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 | 21 | 22 |
| 23 | 24 | 25 | 26 | 27 | 28 | |
