Thursday, August 18. 2011
Wi-Fi Security: Cracking WPA With CPUs, GPUs, And The Cloud
Is your network safe? Almost all of us prefer the convenience of Wi-Fi over the hassle of a wired connection. But what does that mean for security? Our tests tell the whole story. We go from password cracking on the desktop to hacking in the cloud.
We hear about security breaches with such increasing frequency that it's easy to assume the security world is losing its battle to protect our privacy. The idea that our information is safe is what enables so many online products and services; without it, life online would be so very different than it is today. And yet, there are plenty of examples where someone (or a group of someones) circumvents the security that even large companies put in place, compromising our identities and shaking our confidence to the core.
Understandably, then, we're interested in security, and how our behaviors and hardware can help improve it. It's not just the headache of replacing a credit card or choosing a new password when a breach happens that irks us. Rather, it's that feeling of violation when you log into your banking account and discover that someone spent funds out of it all day.
In Harden Up: Can We Break Your Password With Our GPUs?, we took a look at archive security and identified the potential weaknesses of encrypted data on your hard drive. Although the data was useful (and indeed served to scare plenty of people who were previously using insufficient protection on files they really thought were secure), that story was admittedly limited in scope. Most of us don't encrypt the data that we hold dear.
At the same time, most of us are vulnerable in other ways. For example, we don't run on LAN-only networks. We're generally connected to the Internet, and for many enthusiasts, that connectivity is extended wirelessly through our homes and businesses. They say a chain is only as strong as its weakest link. In many cases, that weak link is the password protecting your wireless network.
There is plenty of information online about wireless security. Sorting through it all can be overwhelming. The purpose of this piece is to provide clarification, and then apply our lab's collection of hardware to the task of testing wireless security's strength. We start by breaking WEP and end with distributed WPA cracking in the cloud. By the end, you'll have a much better idea of how secure your Wi-Fi network really is.
-----
Complete article/survey @tomshardware.com
Thursday, August 11. 2011
Geeks Without Frontiers Pursues Wi-Fi for Everyone
Via OStatic
-----
Recently, you may have heard about new efforts to bring online access to regions where it has been economically nonviable before. This idea is not new, of course. The One Laptop Per Child (OLPC) initiative was squarely aimed at the goal until it ran into some significant hiccups. One of the latest moves on this front comes from Geeks Without Frontiers, which has a stated goal of positively impacting one billion lives with technology over the next 10 years. The organization, sponsored by Google and The Tides Foundation, is working on low cost, open source Wi-Fi solutions for "areas where legacy broadband models are currently considered to be uneconomical."
According to an announcement from Geeks Without Frontiers:
"GEEKS expects that this technology, built mainly by Cozybit, managed by GEEKS and I-Net Solutions, and sponsored by Google, Global Connect, Nortel, One Laptop Per Child, and the Manna Energy Foundation, will enable the development and rollout of large-scale mesh Wi-Fi networks for atleast half of the traditional network cost. This is a major step in achieving the vision of affordable broadband for all."
It's notable that One Laptop Per Child is among the sponsors of this initiative. The organization has open sourced key parts of its software platform, and could have natural synergies with a global Wi-Fi effort.
“By driving down the cost of metropolitan and village scale Wi-Fi networks, millions more people will be able to reap the economic and social benefits of significantly lower cost Internet access,” said Michael Potter, one of the founders of the GEEKS initiative.
The Wi-Fi technology that GEEKS is pursuing is mesh networking technology. Specifically, open80211s (o11s), which implements the AMPE (Authenticated Mesh Peering Exchange) enabling multiple authenticated nodes to encrypt traffic between themselves. Mesh networks are essentially widely distributed wireless networks based on many repeaters throught a specific location.
You can read much more about the open80211s standard here. The GEEKS initiative has significant backers, and with sponsorship from OLPC, will probably benefit from good advice on the topic of bringing advanced technologies to disadvantaged regions of the world. The effort will be worth watching.
Wednesday, August 03. 2011
A DIY UAV That Hacks Wi-Fi Networks, Cracks Passwords, and Poses as a Cell Phone Tower
Via POPSCI
By Clay Dillow
-----

Just a Boy and His Cell-Snooping, Password-Cracking, Hacktastic Homemade Spy Drone via Rabbit-Hole
Last year at the Black Hat and Defcon security conferences in Las Vegas, a former Air Force cyber security contractor and a former Air Force engineering systems consultant displayed their 14-pound, six-foot-long unmanned aerial vehicle, WASP (Wireless Aerial Surveillance Platform). Last year it was a work in progress, but next week when they unveil an updated WASP they’ll be showing off a functioning homemade spy drone that can sniff out Wi-Fi networks, autonomously crack passwords, and even eavesdrop on your cell phone calls by posing as a cell tower.
WASP is built from a retired Army target drone, and creators Mike Tassey and Richard Perkins have crammed all kinds of technology aboard, including an HD camera, a small Linux computer packed with a 340-million-word dictionary for brute-forcing passwords as well as other network hacking implements, and eleven different antennae. Oh, and it’s autonomous; it requires human guidance for takeoff and landing, but once airborne WASP can fly a pre-set route, looping around an area looking for poorly defended data.
And on top of that, the duo has taught their WASP a new way to surreptitiously gather intel from the ground: pose as a GSM cell phone tower to trick phones into connecting through WASP rather than their carriers--a trick Tassey and Perkins learned from another security hacker at Defcon last year.
Tassey and Perkins say they built WASP so show just how easy it is, and just how vulnerable you are. “We wanted to bring to light how far the consumer industry has progressed, to the point where public has access to technologies that put companies, and even governments at risk from this new threat vector that they’re not aware of,” Perkins told Forbes.
Consider yourself warned. For details on the WASP design--including pointers on building your own--check out Tassey and Perkins site here.
Friday, July 29. 2011
Trafic IP mobile : le streaming vidéo au coeur de la croissance
Via ItEspresso
-----
Selon Allot, la vidéo s'installe au coeur du trafic IP mobile au niveau mondial au grand dam des opérateurs. Sur ce segment, YouTube se distingue.
Le trafic IP sera assuré à 50% par la vidéo en 2012 et il a d’ores et déjà dépassé celui généré par le peer to peer en 2010.
De surcroît, les prévisions de Cisco précisent qu’il ira crescendo. C’est un constat similaire qui peut être fait si l’on dissèque le trafic IP mobile.
Au cours du premier semestre 2011, 39% du trafic IP a été généré par le streaming vidéo selon une enquête* réalisée par Allot Communications.
Sur la même période, le trafic IP mobile a augmenté de 77% (contre 73% sur le deuxième semestre 2010).
YouTube tient les rênes du streaming vidéo sur mobile comptant pour 52% de sa totalité.
Près d’un octet sur quatre atterrissant sur les mobiles (22% du trafic IP précisément) provient des serveurs de la plate-forme vidéos de Google.
Certes, YouTube est un « ténor de la bande passante » mais, dès que l’on parle part de marché, c’est Skype, le service de VoIP acquis récemment par Microsoft, qui se taille la part du lion.
La voix sur IP a augmenté de 101%, et Skype avec 82% du trafic règne sans partage.
Et de partage, il est question lorsqu’on évoque la messagerie instantanée.
Talonné de très près par Windows Live avec 25%, Yahoo Messenger est premier avec 29% du trafic IP mobile lié à la messagerie instantanée.
Suivent la messagerie instantanée QQ en langue chinoise (18%) puis Google Talk avec 12%.
La part substantielle du streaming vidéo dans le trafic IP mobile ne saurait également cacher l’envolée des réseaux sociaux.
Twitter peut s’enorgueillir d’une croissance de 297% sur les mobiles au cours du premier semestre 2011 tandis que Facebook a augmenté de 166%.
On pourra s’en étonner : la navigation sur Internet n’arrive qu’à la troisième place avec 25% du trafic IP, derrière le partage de fichiers (29%).
Et si le trafic IP sera servi par une croissance des infrastructures, de leur côté, les opérateurs mobiles freinent des quatre fers.
51% d’entre eux affirment ne plus proposer d’abonnements avec données illimitées.
C’est un engorgement des réseaux 3G notamment en zone urbaine qui apparait comme le coupable idéal avec en filigrame le retard de la 4G LTE.
Le marché semble également s’orienter vers un usage « téléguidé » de la bande passante.
Ainsi, 32% des opérateurs ont mis en place un service de passe-droit quand il s’agit de certaines applications ou quand l’illimité est limité à certains usages de la 3G.
Ces données, si elles sont riches d’enseignement, ne renseignent pas sur les pics de trafic générés.
La 4G LTE (avec son débit pic de 1Gigabit/s) puis sa version avancée seront vitales pour les absorber.
Notamment lorsqu’il s’agira de streaming vidéo d’évènements « live ».
Monday, July 25. 2011
Three remote desktop apps worth a look
Via TechRepublic
-----
By Scott Lowe
If your organization allows remote access to systems via remote desktop tools, there are a number of apps for the iPhone and for Android devices that make it a breeze to work anytime from anywhere. In this app roundup, I feature three remote desktop tools that work in slightly different ways.
Splashtop Remote Desktop
Splashtop Remote Desktop is a high-performance app that supports multiple monitors and desktop-based video. The mobile device-based Splashtop Remote Desktop app connects to a small client that is installed on your desktop PC, which can be running Windows XP, Windows Vista, or Windows 7 or Mac OS X 10.6.Perhaps the most significant downside to Splashtop Remote Desktop is that connections are required to be made solely over Wi-Fi networks; this limits, to a point, the locations from which the tool can be used. However, most Wi-Fi connections are faster than 3G, so performance should be good.
Splashtop Remote Desktop is available for the iPhone and for Android devices. At $1.99 for the iPhone version and $4.99 for the Android version, this app will certainly not break the bank.
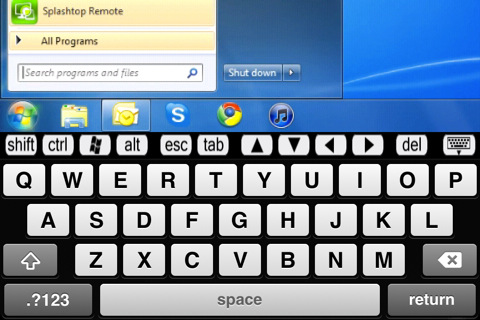
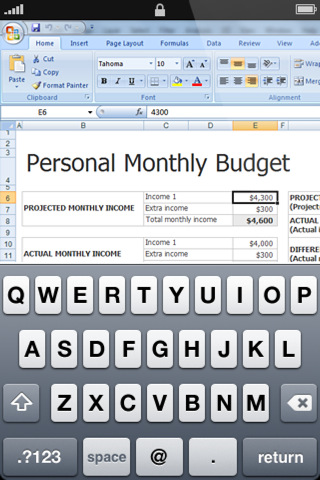
Figures A and B are screenshots of the app from iPhone and Android devices, respectively.
Figure A
Splashtop Remote Desktop for the iPhone
Figure B
The Android version of Splashtop Remote Desktop
LogMeIn Ignition
LogMeIn provides a robust, comprehensive remote desktop tool. LogMeIn Ignition requires you to install a client component on the desktop computer you wish to control.LogMeIn Ignition supports 32-bit and 64-bit Windows 7, Windows Vista, Windows XP, Windows Server 2003, Windows 2008 and 32-bit Windows 2000, and Mac OS X 10.4, 10.5, and 10.6 (PPC and Intel processors are supported). The Mac version is missing features such as drag and drop file transfer, remote sound, and integration with LogMeIn’s centralized reporting tool; although, for occasional remote access from a handheld device, these features are probably not that critical.
LogMeIn Ignition is a client component that works on Android and Apple devices including the iPhone and the iPad. At $29.99, you will need to be able to realize real value from the app in order to justify the purchase. LogMeIn Ignition definitely isn’t a “drive by download.”
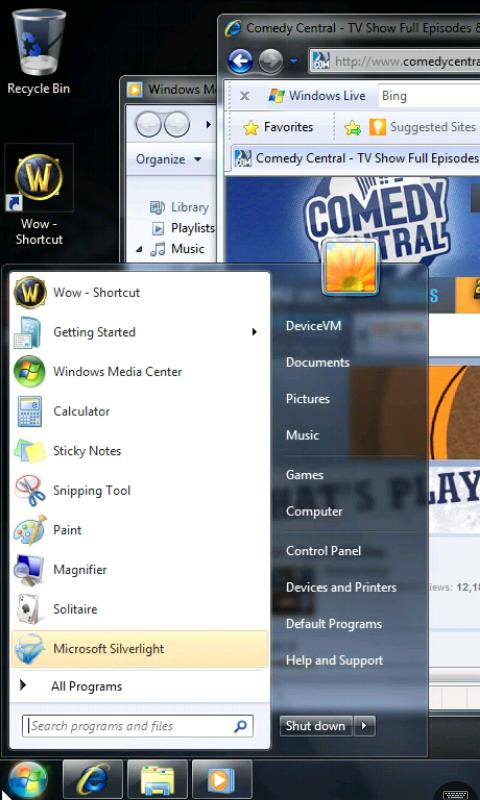
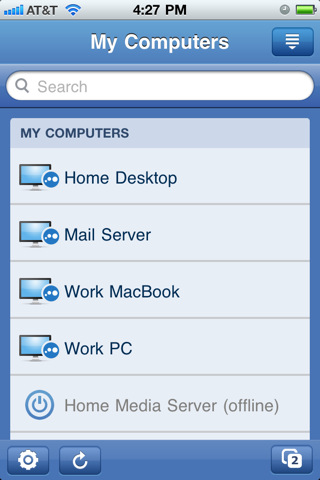
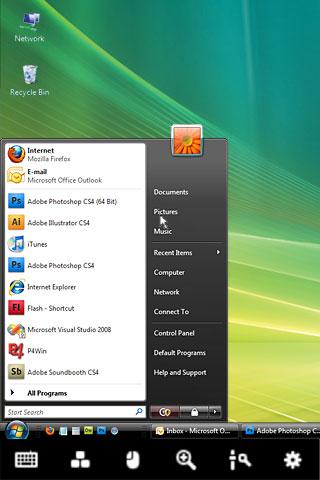
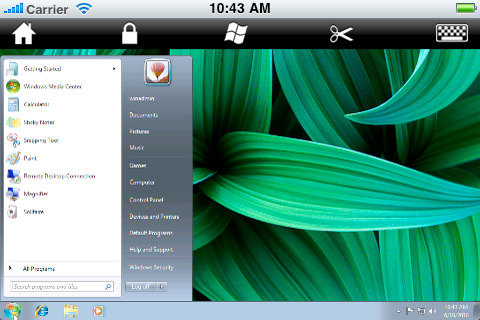
LogMeIn Ignition is not intended to be a “one off” remote access tool; it aggregates all of your remote connections into one view, making it easier to manage a plethora of remote systems (Figure C). Again, each managed system must have the LogMeIn client installed.
Figure C
LogMeIn Ignition’s computer selection page
Figures D and E are screenshots of LogMeIn Ignition on an Android device and an iPhone, respectively.Figure D
Android-based version of LogMeIn Ignition
Figure E
iPhone-based version of LogMeIn Ignition
WinAdmin
WinAdmin is another tool I have used for remote access. The app relies on Microsoft’s standard RDP implementation and does not require the installation of additional client software on managed computers, which makes it a good solution for remote desktop access as well as remote server desktop access. If you’re using WinAdmin to remotely access servers, you’ll probably need some kind of VPN tunnel in place, or you’ll need to be sitting behind your organization’s firewall in order to allow the tool to work its magic.WinAdmin is available for the iPhone, iPad, and iPod Touch; there is no Android version. At $7.99, this app might be considered in the moderately high price range for some, but if it’s being used to support a server farm, it’s certainly affordable.
The screenshots in Figures F, G, and H give you a look at WinAdmin.
Figure F
WinAdmin’s landscape-mode view is more natural for most users.
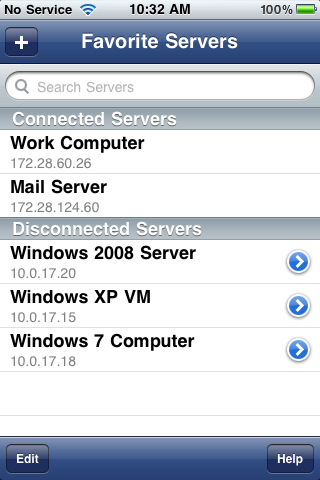
Figure G
Store connection information for all of your remote systems… just lock your phone when not using WinAdmin.
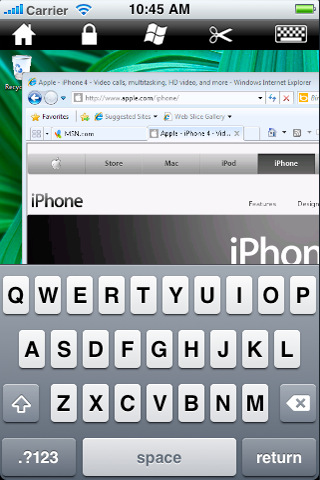
Figure H
WinAdmin’s portrait mode shows the keyboard at the bottom and menu across the top of the display.
What remote desktop app do you recommend?
These are just three tools that are worthy of consideration for your organization’s remote access needs.
-----
Personal comments:
Remote access to desktops are not a 21th century innovation, as it almost exists since the first network was set up, but above solutions and Splashtop in particular bring to us one cross platform solution (streamer available on Mac and PC and remote clients available on all mobile platforms) that may help us to determine what can we seriously do with these tablets! :-)
Thursday, July 14. 2011
Why Is There Steady Migration to the Cloud Despite Reliability and Security Concerns?
-----
Over the past few months, there have been a number of notable service quality incidents and security breaches of online services, including Sony’s PlayStation network, Amazon’s cloud service, Dropbox’s storage in the cloud, and countless others. The bar talk around “cloud” computing and online services would have you think that businesses and consumers are shying away from using hosted services, using Software as a Service (SaaS) applications, from storing their data “in the cloud,” or from migrating some or all of their computing infrastructure to virtual machines hosted by cloud service providers. However, there’s actually an uptick in the uptake of cloud computing in all of its various incarnations.
We (consumers and businesses) are using “cloud” services for all of the following kinds of activities:
1. Accessing and downloading media.
2. Accessing and downloading mobile apps.
3. Accessing and running business applications (CRM, hiring, ecommerce, logistics, provisioning, etc.).
4. Collaborating with colleagues, clients, and customers (project management, online communities, email, meeting scheduling).
5. Analyzing large amounts of data.
6. Storing large amounts of data (much of it unstructured, like video, images, text files, etc.).
7. Developing and testing new applications and online services.
8. Running distributed applications that need high performance around the globe. (All of the social media apps we use are essentially “cloud” applications—they run on virtual machines hosted in mostly 3rd-party data centers all over the world.)
9. Scaling our operations to handle seasonal and other peaking requirements—where we can take advantage of buying computing capabilities by the hour, rather than pre-paying for capacity we rarely need.
10. Back up and Disaster Recovery—keeping copies of our systems and data in remote locations, ready to run if a natural disaster impacts our normal operations.
In short, “cloud computing” in all of its instantiations—Software as a Service, Platform as a Service, Infrastructure as a Service, Cloud Storage, Cloud Computing, etc.—is here to stay. Taking advantage of the cloud (virtual computers running software in data centers distributed around the globe) is the most scalable and the most cost-effective way to provide computing resources and services to anyone who has reliable access to high bandwidth networking via the Internet.
What About Security and Back Up?
Most of us now realize that we’re responsible for the security and
integrity of our information no matter where it sits on the planet.
And we are better off if we have more than one copy of anything
that’s really important.
SaaS and cloud providers have had a lot of experience helping IT organizations migrate some or all of their computing and/or storage to the cloud. And most of them report that most IT organizations’ data security practices leave quite a bit to be desired before they migrate to the cloud. Their customers’ data security and integrity typically improves dramatically as a result of re-thinking their requirements and implementing better policies and practices as they migrated some or all of their computing. (Just because data is in your own physical data center doesn’t mean it’s safe!)
It’s Time to Run Around in Front of the Cloud Parade
We’re now committed to living in the mobile Internet era. We treasure
our mobility and our unfettered access to information,
applications, media, and services. Cloud computing, in all its
forms, is here to stay. Small businesses and innovative service
providers have embraced cloud computing and services wholeheartedly
and are already reaping the benefits of “pay as you consume” for
software and computing and storage services. Medium-sized
businesses are the next to embrace cloud computing, because they
typically don’t have the inertia and overhead that comes with a
huge centralized IT organization. Large enterprises’ IT
organizations are the last to officially accept cloud computing as a
safe and compliant alternative for corporate IT. Yet many
departments in those same large enterprise organizations have been
the early adopters of cloud computing for the development and
testing of new software products and for the departmental (or even
corporate) adoption of SaaS for many of their companies’ most
critical applications.
Tuesday, July 12. 2011
Early Glimpse of Firefox 8 Shows Vast Performance Increases
Via OStatic
-----
 Mozilla has faced some backlash from IT administrators for its move to a rapid release cycle with the Firefox browser,
but you have to hand it to Mozilla for staying the course. For years,
Firefox saw upgrades arrive far less frequently than they arrove for
competitive browsers such as Google Chrome. Since announcing its new
rapid release cycle earlier this year,
Mozilla has released versions 4 and 5 of Firefox, and steadily gotten
better at ironing out short-term kinks, most of which have had to do
with extensions causing problems. Now, Firefox 8 is already being seen
in nightly builds, although it's not released in final form yet, and
early reports show it to be faster than current versions of Chrome
across many benchmarks.
Mozilla has faced some backlash from IT administrators for its move to a rapid release cycle with the Firefox browser,
but you have to hand it to Mozilla for staying the course. For years,
Firefox saw upgrades arrive far less frequently than they arrove for
competitive browsers such as Google Chrome. Since announcing its new
rapid release cycle earlier this year,
Mozilla has released versions 4 and 5 of Firefox, and steadily gotten
better at ironing out short-term kinks, most of which have had to do
with extensions causing problems. Now, Firefox 8 is already being seen
in nightly builds, although it's not released in final form yet, and
early reports show it to be faster than current versions of Chrome
across many benchmarks.
Firefox 7 and 8 run a new graphics engine called Azure, which you can read more about here. And, in broad benchmark tests, ExtremeTech reports the following results:
"Firefox 8, which only just appeared on the Nightly channel, is already 20% faster than Firefox 5 in almost every metric: start up, session restore, first paint, JavaScript execution, and even 2D canvas and 3D WebGL rendering. The memory footprint of Firefox 7 (and thus 8) has also been drastically reduced, along with much-needed improvements to garbage collection."
Mozilla has already done extensive work on how memory is handled in Firefox 7, and these issues are likely to be addressed further with release 8. At this point, Chrome is Firefox's biggest competition, and ExtremeTech also reports:
"While comparison with other browsers has become a little passe in recent months — they’re all so damn similar! — it’s worth noting that Firefox 8 is as fast or faster than the latest Dev Channel build of Chrome 14. Chrome’s WebGL implementation is still faster, but with Azure, Firefox’s 2D performance is actually better than Chrome. JavaScript performance is also virtually identical."
I use Firefox and Chrome, but my primary reason for using Chrome is that it has been faster. With the early glimpse of Firefox 8, the performance gap stands a chance of being closed, and it looks like these two open source browsers have never competed more closely than they do now.
Monday, June 27. 2011
comScore offers digital traffic stats for May 2011, Android dominates US smartphones
-----
It’s very clear that in the smartphone world the Android OS is dominating when it comes to the number of phones selling and popularity with buyers. The Android smartphone is also dominating when it comes to the number of people surfing the web on the OS, at least in some countries. The latest numbers from metrics firm comScore are in and they show the amount of non-computer device internet traffic based on OS. The stats are broken down by iOS, Android, other smartphones, and feature phones.

In the US, Android smartphones are generating 35.6% of the traffic to the web from a smartphone. The iPhone is generating 23.5% of the traffic in the US. Interestingly in the UK, iPhone generated 29.9% of web traffic with the Android platform at 15.1%. Some of that is likely the fact that the iPhone is on all carriers in the UK and only two in the US.
When it comes to the tablet market, the iPad makes 21.8% of web traffic with all Android tablets accounting for 0.6% of traffic from tablets. The numbers in the UK looks similar on the tablet front with 21.3% for iPad and 0.3% on Android tablets.
-----
Tuesday, June 14. 2011
iTunes costs as much as $1.3B to run yearly
Via asymco
-----
The iTunes store continues to grow. The data that Apple published in the last event included the following:
- 15 Billion iTunes song downloads
- 130 million book downloads
- 14 billion app downloads
- $2.5 billion paid to developers
- 225 million accounts
- 425k apps
- 90k iPad apps
- 100k game and entertainment titles
- 50 million game center accounts
As this data is added to the existing data and cross-referenced additional insight into the economics of iTunes is emerging.
Since we know something about the average price of songs and apps, and we know the split between developers and Apple (and roughly between music labels and Apple) we can get a rough estimate of the amount Apple retains to run its store.
The following chart shows iTunes “content margin” by month. This margin is what Apple “keeps” after paying content owners but before paying for other costs like payment processing and delivery/fulfillment which should be accounted as variable costs. Strictly speaking this margin is not “gross margin”.
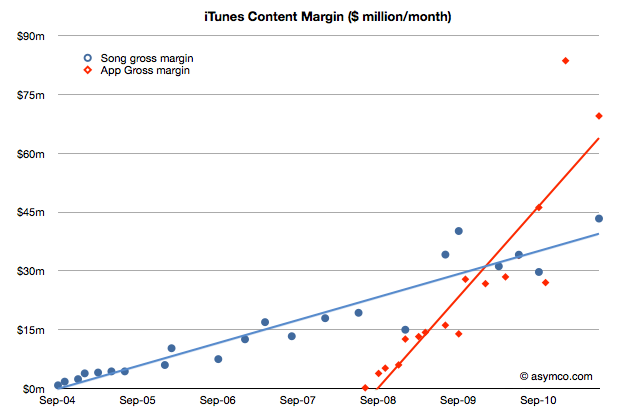
If we add the content margins from music and apps and assume the store runs at break even we can get an idea of what it costs to operate the store. The latest number is $113 million per month (from a total income of $313 million/mo.). It implies over $1.3 billion per year.
Much of that cost does go into serving the content (traffic and payment processing). Some of it goes to curation and support. But it’s very likely that there is much left over to be invested in capacity increases.
I would like to hear alternative opinions, but my guess is that much of the capex that went into the new data centers Apple built came from the iTunes operating margin.
Monday, May 16. 2011
NXP GreenChip: Internet Addresses for every light bulb
Via ubergizmo
-----

With the GreenChip, each bulb becomes a small networked device
NXP has just announced its GreenChip, which gives every light bulb the potential of being connected to a TCP/IP network to provide real-time information and receive commands, wirelessly. This feels a bit like science-fiction talk, but NXP has managed to build a chip that is low-cost enough to be embedded into regular light bulbs (and more in the future) with an increase of about $1 in manufacturing cost. Obviously, $1 is not small relative to the price of a bulb but, in absolute terms, it’s not bad at all — and the cost is bound to fall steadily, thanks to Moore’s law.
But what can you do with wirelessly connected bulbs? For one, you can dim, or turn them on and off using digital commands from any computer, phone or tablet.
You can also do it remotely: those chips have the potential of making home automation much easier and more standard than anything that came before. Better home automation can also mean smarter (and automated) energy -and money- savings. the bulbs are also smart enough to know how much energy they have consumed.
Although the bulbs use internet addresses, they are not connected directly to the web. They don’t use WIFI either, because that protocol is too expensive and not energy-efficient for this usage. Instead, the bulbs are linked through a 2.4-GHz IEEE 802.15.4 network and in standby mode, the GreenChip consumes about 50mW.
The network itself is a mesh network that is connected to a “box” that will itself be connected to your home network. Computers and mobile devices send commands to the box, which sends them to the bulbs. Because it is a mesh network, every bulb is considered to be a “network extender”, so as long as there is 30 meters between two bulbs, the network can be extended across very large surfaces. In a typical house, that would mean no “dead spots”.
The first products will be manufactured by TCP, which manufactures about 1M efficient light bulbs (of all sorts) per day. TCP supplies other brands like Philips or GE. The prices of the final products have yet to be determined, but NXP expect them to be attractive to consumers. Of course, we need to see what the applications will look like too.
This is an interesting first step in embedding low-cost smart chips in low-cost goods. Yet, this is a critical step in creating a smarter local energy grid in our homes.
Quicksearch
Popular Entries
- The great Ars Android interface shootout (131080)
- Norton cyber crime study offers striking revenue loss statistics (101713)
- MeCam $49 flying camera concept follows you around, streams video to your phone (100101)
- Norton cyber crime study offers striking revenue loss statistics (57942)
- The PC inside your phone: A guide to the system-on-a-chip (57524)
Categories
Show tagged entries
Syndicate This Blog
Calendar
|
|
March '26 | |||||
| Mon | Tue | Wed | Thu | Fri | Sat | Sun |
| 1 | ||||||
| 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 | 21 | 22 |
| 23 | 24 | 25 | 26 | 27 | 28 | 29 |
| 30 | 31 | |||||