Wednesday, November 14. 2012
Spike in government surveillance of Google
Via BBC
-----
Governments around the world made nearly 21,000 requests for access to Google data in the first six months of this year, according to the search engine.
Its Transparency Reportindicates government surveillance of online lives is rising sharply.
The US government made the most demands, asking for details 7,969 times in the first six months of 2012.
Turkey topped the list for requests to remove content.
Government 'bellwether'
Google, in common with other technology and communication companies, regularly receives requests from government agencies and courts around the world to have access to content.
It has been publishing its Transparency Report twice a year since 2009 and has seen a steady rise in government demands for data. In its first report in 2009, it received 12,539 requests. The latest figure stands at 20,939.
"This is the sixth time we've released this data, and one trend has become clear: government surveillance is on the rise," Google said in a blog post.
The report acts as a bellwether for government behaviour around the world, a Google spokeswoman told the BBC.
"It reflects laws on the ground. For example in Turkey there are specific laws about defaming public figures whereas in Germany we get requests to remove neo-Nazi content," she said.
"And in Brazil we get a lot of requests to remove content during elections because there is a law banning parodies of candidates.
"We hope that the report will shed light on how governments interact with online services and how laws are reflected in online behaviour," she added.
The US has consistently topped the charts for data requests. France, Germany, Italy, Spain and the UK are also in the top 10.
In France and Germany it complied with fewer than half of all requests. In the UK it complied with 64% of requests and 90% of requests from the US.
Removing content
Google said the top three reasons cited by government for content removal were defamation, privacy and security.
Worldwide authorities made 1,789 requests for Google to remove content, up from 1,048 requests for the last six months of 2011.
In the period from January to June, Turkey made 501 requests for content removal.
These included 148 requests related to Mustafa Kemal Ataturk - the first president of Turkey, the current government, national identity and values.
Others included claims of pornography, hate speech and copyright.
Google has its own criteria for whether it will remove content - the request must be specific, relate to a specific web address and have come from a relevant authority.
In one example from the UK, Google received a request from police to remove 14 search results that linked to sites allegedly criticising the police and claiming individuals were involved in obscuring crimes. It did not remove the content.
Tuesday, October 30. 2012
The Pirate Bay switches to cloud-based servers
Via Slash Gear
-----
It isn’t exactly a secret that authorities and entertainment groups don’t like The Pirate Bay, but today the infamous site made it a little bit harder for them to bring it down. The Pirate Bay announced today that it has move its servers to the cloud. This works in a couple different ways: it helps the people who run The Pirate Bay save money, while it makes it more difficult for police to carry out a raid on the site.

“All attempts to attack The Pirate Bay from now on is an attack on everything and nothing,” a Pirate Bay blog post reads. “The site that you’re at will still be here, for as long as we want it to. Only in a higher form of being. A reality to us. A ghost to those who wish to harm us.” The site told TorrentFreak after the switch that its currently being hosted by two different cloud providers in two different countries, and what little actual hardware it still needs to use is being kept in different countries as well. The idea is not only to make it harder for authorities to bring The Pirate Bay down, but also to make it easier to bring the site back up should that ever happen.
Even if authorities do manage to get their hands on The Pirate Bay’s remaining hardware, they’ll only be taking its transit router and its load balancer – the servers are stored in several Virtual Machine instances, along with all of TPB’s vital data. The kicker is that these cloud hosting companies aren’t aware that they’re hosting The Pirate Bay, and if they discovered the site was using their service, they’d have a hard time digging up any dirt on users since the communication between the VMs and the load balancer is encrypted.
In short, it sounds like The Pirate Bay has taken a huge step in not only protecting its own rear end, but those of users as well. If all of this works out the way The Pirate Bay is claiming it will, then don’t expect to hear about the site going down anytime soon. Still, there’s nothing stopping authorities from trying to bring it down, or from putting in the work to try and figure out who the people behind The Pirate Bay are. Stay tuned
Monday, October 29. 2012
A Stuxnet Future? Yes, Offensive Cyber-Warfare is Already Here
Via ISN ETHZ
By Mihoko Matsubara
-----

Server room at CERN
Mounting Concerns and Confusion
Stuxnet proved that any actor with sufficient know-how in terms of cyber-warfare can physically inflict serious damage upon any infrastructure in the world, even without an internet connection. In the words of former CIA Director Michael Hayden: “The rest of the world is looking at this and saying, ‘Clearly someone has legitimated this kind of activity as acceptable international conduct’.”
Governments are now alert to the enormous uncertainty created by cyber-instruments and especially worried about cyber-sabotage against critical infrastructure. As US Secretary of Defense Leon Panetta warned in front of the Senate Armed Services Committee in June 2011; “the next Pearl Harbor we confront could very well be a cyber-attack that cripples our power systems, our grid, our security systems, our financial systems, our governmental systems.” On the other hand, a lack of understanding about instances of cyber-warfare such as Stuxnet has led to confused expectations about what cyber-attacks can achieve. Some, however, remain excited about the possibilities of this new form of warfare. For example, retired US Air Force Colonel Phillip Meilinger expects that “[a]… bloodless yet potentially devastating new method of war” is coming. However, under current technological conditions, instruments of cyber-warfare are not sophisticated enough yet to deliver a decisive blow to the adversary. As a result, cyber-capabilities still need to be used alongside kinetic instruments of war.
Advantages of Cyber-Capabilities
Cyber-capabilities provide three principal advantages to those actors that possess them. First, they can deny or degrade electronic devices including telecommunications and global positioning systems in a stealthy manner irrespective of national borders. This means potentially crippling an adversary’s intelligence, surveillance, and reconnaissance capabilities, delaying an adversary’s ability to retaliate (or even identify the source of an attack), and causing serious dysfunction in an adversary’s command and control and radar systems.
Second, precise and timely attribution is particularly challenging in cyberspace because skilled perpetrators can obfuscate their identity. This means that responsibility for attacks needs to be attributed forensically which not only complicates retaliatory measures but also compromises attempts to seek international condemnation of the attacks.
Finally, attackers can elude penalties because there is currently no international consensus as to what actually constitutes an ‘armed attack’ or ‘imminent threat’ (which can invoke a state’s right of self-defense under Article 51 of the UN Charter) involving cyber-weapons. Moreover, while some countries - including the United States and Japan - insist that the principles of international law apply to the 'cyber' domain, others such as China argue that cyber-attacks “do not threaten territorial integrity or sovereignty.”
Disadvantages of Cyber-Capabilities
On the other hand, high-level cyber-warfare has three major disadvantages for would-be attackers. First, the development of a sophisticated ‘Stuxnet-style’ cyber-weapon for use against well-protected targets is time- and resource- intensive. Only a limited number of states possess the resources required to produce such weapons. For instance, the deployment of Stuxnet required arduous reconnaissance and an elaborate testing phase in a mirrored environment. F-Secure Labs estimates that Stuxnet took more than ten man-years of work to develop, underscoring just how resource- and labor- intensive a sophisticated cyber-weapon is to produce.
Second, sophisticated and costly cyber-weapons are unlikely to be adapted for generic use. As Thomas Rid argues in "Think Again: Cyberwar,” different system configurations need to be targeted by different types of computer code. The success of a highly specialized cyber-weapon therefore requires the specific vulnerabilities of a target to remain in place. If, on the contrary, a targeted vulnerability is ‘patched’, the cyber-operation will be set back until new malware can be prepared. Moreover, once the existence of malware is revealed, it will tend to be quickly neutralized – and can even be reverse-engineered by the target to assist in future retaliation on their part.
Finally, it is difficult to develop precise, predictable, and controllable cyber-weapons for use in a constantly evolving network environment. The growth of global connectivity makes it difficult to assess the implications of malware infection and challenging to predict the consequences of a given cyber-attack. Stuxnet , for instance, was not supposed to leave Iran’s Natanz enrichment facility, yet the worm spread to the World Wide Web, infecting other computers and alerting the international community to its existence. According to the Washington Post , US forces contemplated launching cyber-attacks on Libya’s air defense system before NATO’s airstrikes. But this idea was quickly abandoned due to the possibility of unintended consequences for civilian infrastructure such as the power grid or hospitals.
Implications for Military Strategy
Despite such disadvantages, cyber-attacks are nevertheless part of contemporary military strategy including espionage and offensive operations. In August 2012, US Marine Corps Lieutenant General Richard Mills confirmed that operations in Afghanistan included cyber-attacks against the adversary. Recalling an incident in 2010, he said, "I was able to get inside his nets, infect his command-and-control, and in fact defend myself against his almost constant incursions to get inside my wire, to affect my operations."
His comments confirm that the US military now employs a combination of cyber- and traditional offensive measures in wartime. As Thomas Mahnken points out in “Cyber War and Cyber Warfare,” cyber-attacks can produce disruptive and surprising effects. And while cyber-attacks are not a direct cause of death, their consequences may lead to injuries and loss of life. As Mahnken argues, it would be inconceivable to directly cause Hiroshima-type damage and casualties merely with cyber-attacks. While a “cyber Pearl Harbor” might shock the adversary on a similar scale as its namesake in 1941, the ability to inflict a decisive, extensive, and foreseeable blow requires kinetic support – at least under current technological conditions.
Implications for Critical Infrastructure
Nevertheless, the shortcomings of cyber-attacks will not discourage malicious actors in peacetime. The anonymous, borderless, and stealthy nature of the 'cyber' domain offers an extremely attractive asymmetrical platform for inflicting physical and psychological damage to critical infrastructure such as finance, energy, power and water supply, telecommunication, and transportation as well as to society at large. Since well before Stuxnet, successful cyber-attacks have been launched against vulnerable yet important infrastructure systems. For example, in 2000 a cyber-attack against an Australian sewage control system resulted in millions of liters of raw sewage leaking into a hotel, parks, and rivers.
Accordingly, the safeguarding of cyber-security is an increasingly important consideration for heads of state. In July 2012, for example, President Barack Obama published an op-ed in the Wall Street Journal warning about the unique risk cyber-attacks pose to national security. In particular, the US President emphasized that cyber-attacks have the potential to severely compromise the increasingly wired and networked lifestyle of the global community. Since the 1990s, the process control systems of critical infrastructures have been increasingly connected to the Internet. This has unquestionably improved efficiencies and lowered costs, but has also left these systems alarmingly vulnerable to penetration. In March 2012, McAfee and Pacific Northwest National Laboratory released a report which concluded that power grids are rendered vulnerable due to their common computing technologies, growing exposure to cyberspace, and increased automation and interconnectivity.
Despite such concerns, private companies may be tempted to prioritize short-term profits rather than allocate more funds to (or accept more regulation of) cyber-security, especially in light of prevailing economic conditions. After all, it takes time and resources to probe vulnerabilities and hire experts to protect them. Nevertheless, leadership in both the public and private sectors needs to recognize that such an attitude provides opportunities for perpetrators to take advantage of security weaknesses to the detriment of economic and national security. It is, therefore, essential for governments to educate and encourage --- and if necessary, fund --- the private sector to provide appropriate cyber-security in order to protect critical infrastructure.
Implications for Espionage
The sophistication of the Natanz incident, in which Stuxnet was able to exploit Iranian vulnerabilities, stunned the world. Advanced Persistent Threats (APTs) were employed to find weaknesses by stealing data which made it possible to sabotage Iran’s nuclear program. Yet APTs can also be used in many different ways, for example against small companies in order to exploit larger business partners that may be possession of valuable information or intellectual property. As a result, both the public and private sectors must brace themselves for daily cyber-attacks and espionage on their respective infrastructures. Failure to do so may result in the theft of intellectual property as well as trade and defense secrets that could undermine economic competitiveness and national security.
In an age of cyber espionage, the public and private sectors must also reconsider what types of information should be deemed as “secret,” how to protect that information, and how to share alerts with others without the sensitivity being compromised. While realization of the need for this kind of wholesale re-evaluation is growing, many actors remain hesitant. Indeed, such hesitancy is driven often out of fears that doing so may reveal their vulnerabilities, harm their reputations, and benefit their competitors. Of course, there are certain types of information that should remain unpublicized so as not to damage the business, economy, and national security. However, such classifications must not be abused against balance between public interest and security.
Cyber-Warfare Is Here to Stay
The Stuxnet incident is set to encourage the use of cyber-espionage and sabotage in warfare. However, not all countries can afford to acquire offensive cyber-capabilities as sophisticated as Stuxnet and a lack of predictability and controllability continues to make the deployment of cyber-weapons a risky business. As a result, many states and armed forces will continue to combine both kinetic and 'cyber' tactics for the foreseeable future. Growing interconnectivity also means that the number of potential targets is set to grow. This, in turn, means that national cyber-security strategies will need to confront the problem of prioritization. Both the public and private sectors will have to decide which information and physical targets need to be protected and work together to share information effectively.
Wednesday, October 24. 2012
Molecular 3D bioprinting could mean getting drugs through email
Via dvice
-----
What happens when you combine advances in 3D printing with biosynthesis and molecular construction? Eventually, it might just lead to printers that can manufacture vaccines and other drugs from scratch: email your doc, download some medicine, print it out and you're cured.
This concept (which is surely being worked on as we speak) comes from Craig Venter, whose idea of synthesizing DNA on Mars we posted about last week. You may remember a mention of the possibility of synthesizing Martian DNA back here on Earth, too: Venter says that we can do that simply by having the spacecraft email us genetic information on whatever it finds on Mars, and then recreate it in a lab by mixing together nucleotides in just the right way. This sort of thing has already essentially been done by Ventner, who created the world's first synthetic life form back in 2010.
Vetner's idea is to do away with complex, expensive and centralized vaccine production and instead just develop one single machine that can "print" drugs by carefully combining nucleotides, sugars, amino acids, and whatever else is needed while u wait. Technology like this would mean that vaccines could be produced locally, on demand, simply by emailing the appropriate instructions to your closes drug printer. Pharmacies would no longer consists of shelves upon shelves of different pills, but could instead be kiosks with printers inside them. Ultimately, this could even be something you do at home.
While the benefits to technology like this are obvious, the risks are equally obvious. I mean, you'd basically be introducing the Internet directly into your body. Just ingest that for a second and think about everything that it implies. Viruses. LOLcats. Rule 34. Yeah, you know what, maybe I'll just stick with modern American healthcare and making ritual sacrifices to heathen gods, at least one of which will probably be effective.
Wednesday, October 10. 2012
The mouse faces extinction as computer interaction evolves
-----
Swipe, swipe, pinch-zoom. Fifth-grader Josephine Nguyen is researching the definition of an adverb on her iPad and her fingers are flying across the screen. Her 20 classmates are hunched over their own tablets doing the same.
Conspicuously absent from this modern scene of high-tech learning: a mouse.
Nguyen, who is 10, said she has used one before — once — but the clunky desktop computer/monitor/keyboard/mouse setup was too much for her.
“It was slow,” she recalled, “and there were too many pieces.”
Gilbert Vasquez, 6, is also baffled by the idea of an external pointing device named after a rodent.
“I don’t know what that is,” he said with a shrug.
Nguyen and Vasquez, who attend public schools here, are part of the first generation growing up with a computer interface that is vastly different from the one the world has gotten used to since the dawn of the personal-computer era in the 1980s.
This fall, for the first time, sales of iPads are cannibalizing sales of PCs in schools, according to Charles Wolf, an analyst for the investment research firm Needham & Co. And a growing number of even more sophisticated technologies for communicating with your computer — such as the Leap Motion boxes and Sony Vaio laptops that read hand motions, as well as voice recognition services such as Apple’s Siri — are beginning to make headway in the commercial market.
John Underkoffler, a former MIT researcher who was the adviser for the high-tech wizardry that Tom Cruise used in “Minority Report,” says that the transition is inevitable and that it will happen in as soon as a few years.
Underkoffler, chief scientist for Oblong, a Los Angeles-based company that has created a gesture-controlled interface for computer systems, said that for decades the mouse was the primary bridge to the virtual world — and that it was not always optimal.
“Human hands and voice, if you use them in the digital world in the same way as the physical world, are incredibly expressive,” he said. “If you let the plastic chunk that is a mouse drop away, you will be able to transmit information between you and machines in a very different, high-bandwidth way.”
This type of thinking is turning industrial product design on its head. Instead of focusing on a single device to access technology, innovators are expanding their horizons to gizmos that respond to body motions, the voice, fingers, eyes and even thoughts. Some devices can be accessed by multiple people at the same time.
Keyboards might still be used for writing a letter, but designing, say, a landscaped garden might be more easily done with a digital pen, as would studying a map of Lisbon by hand gestures, or searching the Internet for Rihanna’s latest hits by voice. And the mouse — which many agree was a genius creation in its time — may end up as a relic in a museum.
The mouse is born
The first computer mouse, built at the Stanford Research Institute in Palo Alto, Calif., by Douglas Englebart and Bill English in 1963, was just a block of wood fashioned with two wheels. It was just one of a number of interfaces the team experimented with. There were also foot pedals, head-pointing devices and knee-mounted joysticks.
But the mouse proved to be the fastest and most accurate, and with the backing of Apple founder Steve Jobs — who bundled it with shipments of Lisa, the predecessor to the Macintosh, in the 1980s — the device suddenly became a mainstream phenomenon.
Englebart’s daughter, Christina, a cultural anthropologist, said that her father was able to predict many trends in technology over the years, but she said the one thing he has been surprised about is that the mouse has lasted as long as it has.
“He never assumed the mouse would be it,” said the younger Englebart, who wrote her father’s biography. “He always figured there would be newer ways of exploring a computer.”
She was 8 years old when her father invented the mouse. Now 57, she says she is finally seeing glimpses of the next stage of computing with the surging popularity of the iPad. These days her two children, 20 and 23, do not use a mouse anymore.
San Antonio and LUCHA elementary schools in eastern San Jose, just 17 miles south of where Englebart conducted his research, provide a glimpse at the future. The schools, which share a campus, have integrated iPod Touches and iPads into the curriculum for all 700 students. The teachers all get Mac Airbooks with touch pads.
“Most children here have never seen a computer mouse,” said Hannah Tenpas, 24, a kindergarten teacher at San Antonio.
Kindergartners, as young as 4, use the iPod Touch to learn letter sounds. The older students use iPads to research historical information and prepare multimedia slide-show presentations about school rules. The intuitive touch-screen interface has allowed the school to introduce children to computers at an age that would have been impossible in the past, said San Antonio Elementary’s principal, Jason Sorich.
Even toddlers are able manipulate a touch screen. A popular YouTube video shows a baby trying to swipe the pages of a fashion magazine that she assumes is a broken iPad.
“For my one-year-old daughter, a magazine is an iPad that does not work. It will remain so for her whole life,” the creator of the video says in a slide at the end of the clip.
The iPad side of the brain
“The popularity of iPads and other tablets is changing how society interacts with information,” said Aniket Kittur, an assistant professor at the Human-Computer Interaction Institute at Carnegie Mellon University. “.?.?. Direct manipulation with our fingers, rather than mediated through a keyboard/mouse, is intuitive and easy for children to grasp.”
Underkoffler said that while desktop computers helped activate the language and abstract-thinking parts of a child’s brain, new interfaces are helping open the spatial part.
“Once our user interface can start to talk to us that way .?.?. we sort of blow the barn doors off how we learn,” he said.
That may explain why iPads are becoming so popular in schools. Apple said in July that the iPad outsold the Mac 2 to 1 for the second consecutive quarter in the education market. In all, the company sold 17 million iPads in the April-to-June quarter; at the same time, mouse sales in the United States are down, some manufacturers say.
“The adoption rate of iPad in education is something I’d never seen from any technology product in history,” Apple chief executive Tim Cook said in July.
At San Antonio Elementary and LUCHA, which started their $300,000 iPad and iPod experiment last school year, the school board president, Esau Herrera, said he is thrilled by the results. Test scores have gone up (although officials say they cannot directly correlate that to the new technology), and the level of engagement has increased.
The schools are now debating what to do with the handful of legacy desktop PCs, each with its own keyboard and mouse, and whether they should bother teaching students to move a pointer around a monitor.
“Things are moving so fast,” said LUCHA Principal Kristin Burt, “that we’re not sure the computer and mouse will even be around when they get old enough to really use them.”
Monday, October 08. 2012
There Really Is a Smartphone Inside ‘EW Magazine’
Via Mashable
-----
They told us, but we did not believe them: The Oct. 5 print edition of Entertainment Weekly, which features a one-of-a-kind digital ad running video and live tweets, actually has a smartphone inside of it. A real, full-sized 3G cellphone inside a print magazine.
The digital ad is designed to promote the CW network’s fresh lineup of action shows (The Arrow and Emily Owens, M.D.) and, when you open the magazine to the ad, the small LCD screen shows short clips of the two shows and then switches to live tweets from CW’s Twitter account.
When we spoke to CW representatives earlier this week, they did tell us that “the ad is powered by a custom-built, smartphone-like Android device with an LED screen and 3G connectivity; it was manufactured in China.” This is all true, though the device is far more than just “smartphone-like.”
During our teardown, we discovered a smartphone-sized battery, a full QWERTY keyboard hidden under black plastic tape, a T-Mobile 3G card, a camera, speaker and a live USB port that will accept a mini USB cable, which you can then plug into a computer and recharge the phone. We could also see from the motherboard that the smartphone was built by Foxconn. You may have heard of it.
Once we extracted the phone from its clear plastic housing (which was sandwiched between two rather thick card-stock pages), we were able to use a screw driver to close the open contacts on the touch pad and access the on-screen Android menu, which has a full complement of apps. It wasn’t easy, but we even made a phone call.
That’s right, there’s nothing wrong with this phone, other than it being old, under powered and partially in Chinese. Oh, yes, and the fact that it’s jammed inside a print magazine.
Mashable Senior Tech Analyst Christina Warren, who assisted in our teardown, did some research (including using the number on the motherboard) and is now fairly certain that guts come from this $86 ABO smartphone. Don’t worry, it’s unlikely that it cost the CW anywhere near that much.
Entertainment Weekly is only producing 1,000 of these digital advertising-enhanced issues, so if you want a nearly free smartphone that, with a good deal of nudging, actually works, you better run, not walk, to your nearest newsstand.
In the meantime, we’ll keep playing with the phone to see if we can make it perform other tricks, like calling the phone number we desire and crafting our own tweets. We did finally get the camera working, but without a lens over it, the images are a blurry mess. More challenges for what I’m officially naming our Entertainment Weekly Digital Ad/Smartphone Print Insert Hackathon!
Tuesday, September 18. 2012
Stretchable, Tattoo-Like Electronics Are Here to Check Your Health
Via Motherboard
-----

Wearable computing is all the rage this year as Google pulls back the curtain on their Glass technology, but some scientists want to take the idea a stage further. The emerging field of stretchable electronics is taking advantage of new polymers that allow you to not just wear your computer but actually become a part of the circuitry. By embedding the wiring into a stretchable polymer, these cutting edge devices resemble human skin more than they do circuit boards. And with a whole host of possible medical uses, that’s kind of the point.
A Cambridge, Massachusetts startup called MC10 is leading the way in stretchable electronics. So far, their products are fairly simple. There’s a patch that’s meant to be installed right on the skin like a temporary tattoo that can sense whether or not the user is hydrated as well as an inflatable balloon catheter that can measure the electronic signals of the user’s heartbeat to search for irregularities like arrythmias. Later this year, they’re launching a mysterious product with Reebok that’s expected to take advantage of the technology’s ability to detect not only heartbeat but also respiration, body temperature, blood oxygenation and so forth.
The joy of stretchable electronics is that the manufacturing process is not unlike that of regular electronics. Just like with a normal microchip, gold electrodes and wires are deposited on to thin silicone wafers, but they’re also embedded in the stretchable polymer substrate. When everything’s in place, the polymer substrate with embedded circuitry can be peeled off and later installed on a new surface. The components that can be added to stretchable surface include sensors, LEDs, transistors, wireless antennas and solar cells for power.
For now, the technology is still the nascent stages, but scientists have high hopes. In the future, you could wear a temporary tattoo that would monitor your vital signs, or doctors might install stretchable electronics on your organs to keep track of their behavior. Stretchable electronics could also be integrated into clothing or paired with a smartphone. Of course, if all else fails, it’ll probably make for some great children’s toys.
Wednesday, September 12. 2012
Twenty-nine of history’s most iconic scientists in one photograph – now in color!
Via io9
-----
It was originally captured in 1927 at the fifth Solvay Conference, one of the most star-studded meetings of scientific minds in history. Notable attendees included Albert Einstein, Niels Bohr, Marie Curie, Erwin Schrödinger, Werner Heisenberg, Wolfgang Pauli, Paul Dirac and Louis de Broglie — to name a few.
Of the 29 scientists in attendance (the majority of whom contributed to the fields of physics and chemistry), over half of them were, or would would go to become, Nobel laureates. (It bears mentioning that Marie Curie, the only woman in attendance at the conference, remains the only scientist in history to be awarded Nobel Prizes in two different scientific fields.)
All this is to say that this photo is beyond epic. Now, thanks to the masterful work of redditor mygrapefruit, this photo is more impressive, still. Through a process known as colorization, mygrapefruit has given us an an even better idea of what this scene might have looked like had we attended the conference in person back in 1927; and while the Sweden-based artist typically charges for her skills, she's included a link to a hi-res, print-size download of the colorized photo featured below, free of charge.
You can learn more about the colorization process, and check out more of mygrapefruit's work, over on her website.
Friday, August 31. 2012
How Does the Curiosity Rover Nuclear Battery Work?
Via About Robots
-----

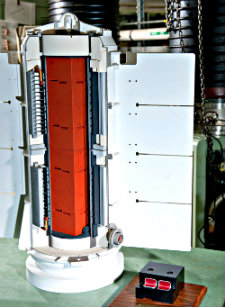
The nuclear battery is the black 'tail'
Photo courtesy of NASA
First, I'll tell you its real name: NASA calls it the Multi-Mission Radioisotope Thermoelectric Generator, or MMRTG. And the principle is quite simple: the radioactive plutonium generates heat by splitting naturally into more stable atoms. The heat is used to 'cook' a thermocouple that generates electricity to the whole system.
Okay, so just like you, my next question was: what is a thermocouple? When you make 2 different metals touch each other, it creates a tension (voltage) that is dependant on the temperature. It is very reliable to calculate the tension from the temperature if you use the right metals. Now, if you want to make a battery, you just need to have 2 junctions at 2 different temperatures. You can get more info from Wikipedia's page on thermocouple. That's it: the Plutonium generates very regular heat over several years, the heat hits up the warm part of the thermocouple, and the thermocouple generates electricity to the system.
The whole system is safe enough and small enough that even if the rocket explodes at launch, the Plutonium would most likely not be released, and it's release wouldn't even be a problem.
Has it been used before?
 |
Yes it has! It has been used since the Apollo mission. The first time I heard about the Curiosity Rover nuclear battery, I was thinking this must be top notch technology. What a surprised I had when I saw it has been used for more that 40 years already. It's never too late to learn how it works anyway.
Let's quote NASA: "The Apollo missions to the moon, the Viking missions to Mars, and the Pioneer, Voyager, Ulysses, Galileo, Cassini and New Horizons missions to the outer solar system all used radioisotope thermoelectric generators."
Still, the Curiosity Rover nuclear battery is a new generation battery that is used for the first time on this Mars rover. As NASA says, it is more flexible and can be used on a wide variety of missions since they have better control over the tension delivered by the new system.
In particular, only the new generation can deliver 14 years of energy within a 45kg, 60X60X60cm box. Yes, it is not much different from the boiler in your house, but so much more powerful.
Let's compare to Solar Panels
Why didn't they send the Mars Science Laboratory with solar panels like the 2 previous generations of Mars rovers?
In short, NASA wanted to make this mission better and faster. The 2 main drawbacks of solar panels is that they don't work during the night, and they don't work during the Martian winter. One consequence is that the Mars Exploration Rovers couldn't work for more that half of the time.
 |
The Curiosity Rover Nuclear Battery will supply the system with constant power, allowing it to work as much as needed, all year long for as long as 14 years. Imagine the difference when the rover is traveling from one point to another if it doesn't have to stop every night.
Another thing is that the new rover is much bigger and holds more experimental tools, and can go a little faster. All in all, the power supply from the nuclear battery is nearly 3 times more than the solar panels (in day time).
All these are clear good reasons for the Mars Science Laboratory to go to Mars with some Plutonium in its backpack.
Wednesday, August 29. 2012
Swiss sheep to warn shepherds of wolf attacks by SMS
Via Phys Org
-----

"It's the first time that such a system has been tried outdoors," said biologist Jean-Marc Landry, who took part in testing on a Swiss meadow this week. In the trial, reported by the country's news agency ATS, around 10 sheep were each equipped with a heart monitor before being targeted by a pair of Wolfdogs -- both of which were muzzled. During the experiment, the change in the flock's heartbeat was found to be significant enough to imagine a system whereby the sheep could be fitted with a collar that releases a repellent to drive the wolf away, while also sending an SMS to the shepherd. The device is aimed at owners of small flocks who lack the funds to keep a sheepdog, Landry said, adding that it could also be used in tourist areas where guard dogs are not popular. A prototype collar is expected in the autumn and testing is planned in Switzerland and France in 2013. Other countries including Norway are said to be interested. The issue of wolves is a divisive one in Switzerland where the animals appear to be back after a 100-year absence. On July 27 a wolf killed two sheep in St Gall, the first such attack in the eastern canton. (c) 2012 AFP
Read more at: http://phys.org/news/2012-08-swiss-sheep-shepherds-wolf-sms.html#jCp
Read more at: http://phys.org/news/2012-08-swiss-sheep-shepherds-wolf-sms.html#jCp
Read more at: http://phys.org/news/2012-08-swiss-sheep-shepherds-wolf-sms.html#jCp
Read more at: http://phys.org/news/2012-08-swiss-sheep-shepherds-wolf-sms.html#jCp
Quicksearch
Popular Entries
- The great Ars Android interface shootout (131055)
- Norton cyber crime study offers striking revenue loss statistics (101667)
- MeCam $49 flying camera concept follows you around, streams video to your phone (100067)
- Norton cyber crime study offers striking revenue loss statistics (57896)
- The PC inside your phone: A guide to the system-on-a-chip (57463)
Categories
Show tagged entries
Syndicate This Blog
Calendar
|
|
February '26 | |||||
| Mon | Tue | Wed | Thu | Fri | Sat | Sun |
| 1 | ||||||
| 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 | 21 | 22 |
| 23 | 24 | 25 | 26 | 27 | 28 | |




