Entries tagged as software
Wednesday, October 05. 2011
Via ExtremeTech
By Sebastian Anthony
-----
The Apple “Let’s Talk iPhone” event has
concluded. Tim Cook and a slew of Apple execs have taken it in turns to
tell us about the latest and greatest Apple goodies, and rather
underwhelmingly there’s no iPhone 5 and just significant takeaways: a
cheaper and faster iPhone 4S, and an interesting software package called
Siri. You can read all about the iPhone 4S on our sister sites Geek and PC Mag — here we’re going to talk about Siri.
If
we look past the rather Indian (and feminine) name, Siri is a portable
(and pocketable) virtual personal assistant. She has a
speech-recognition module which works out what you’re saying, and then a
natural language parser combs through your words to work out what
you’re trying to do. Finally, an artificial intelligence gathers the
possible responses and works out which one is most likely to be
accurate, given the context, your geographical location, iOS’s current
state, and so on.
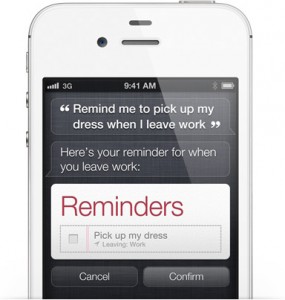 Siri
is, in essence, a computer that you can interrogate for answers, kind
of like a search engine that runs locally on your phone. If you’ve seen IBM’s Watson play Jeopardy,
Siri is basically a cut-down version. She isn’t intelligent per se, but
if she has access to enough data, she can certainly appear intelligent.
Siri’s data sources are open APIs, like Wikipedia or Wolfram Alpha, and
in theory there’s no limit to the number of sources that can be added
(though it does require significant developer time to add a new data
set). For now you can ask Siri about the weather or the definition of a
word, but in the future, if Apple links Siri up to United Airlines,
you’ll be able to book a plane ticket, just by talking. Because Siri
runs locally, she can also send SMSes or set reminders, or anything else
that Apple (or app developers) allow her to do. Siri
is, in essence, a computer that you can interrogate for answers, kind
of like a search engine that runs locally on your phone. If you’ve seen IBM’s Watson play Jeopardy,
Siri is basically a cut-down version. She isn’t intelligent per se, but
if she has access to enough data, she can certainly appear intelligent.
Siri’s data sources are open APIs, like Wikipedia or Wolfram Alpha, and
in theory there’s no limit to the number of sources that can be added
(though it does require significant developer time to add a new data
set). For now you can ask Siri about the weather or the definition of a
word, but in the future, if Apple links Siri up to United Airlines,
you’ll be able to book a plane ticket, just by talking. Because Siri
runs locally, she can also send SMSes or set reminders, or anything else
that Apple (or app developers) allow her to do.
Artificial
intelligence isn’t cheap in terms of processing power, though: Siri is
expected to only run on the iPhone 4S, which sports a new and
significantly faster processor than its predecessors, the A5. Siri
probably makes extensive use of Apple’s new cloud computer cluster, too,
much in the same way that Amazon Silk splits web browsing between the cloud and the local device.
Noise
That’s
enough about what Siri is and how it works. Let’s talk about whether
anyone will actually use Siri, which is fundamentally a glorified voice
control search engine. Voice commands have existed in some semblance
since at least as far back as the Nokia 3310, which was released in
2000. Almost every phone since then has had the ability to voice dial,
or in the case of modern smartphones, voice activate apps and features.
When
was the last time you saw someone talk to their phone? Driving and
other hands-otherwise-occupied activities don’t count. When was the last
time you walked down the street and heard someone loudly dictate “call
mom” into their phone? Can you really see yourself saying “Siri, I want a
kebab” in public?
It might lose its social stigma if everyone
talks to their phone, but isn’t it already annoying enough that people
swan down streets with hands-free headsets, blabbing away? It’s not like
voice recognition is at the stage where you can whisper or mumble a
command into your phone, either: you’re going to have to say, nice and
clearly, “how do I get to the bank?” in public. Now imagine that you’ve
just walked past the guy who’s talking to Siri — is he asking you for
directions, or Siri? Now imagine what it would be like if everyone
around you is having a one-sided phone conversation or talking to Siri.
Finally,
there’re practical implications to consider, which Apple usually
ignores in its press events. For example, will Siri only recognize my
voice? What if I leave my phone in the living room and my girlfriend
shouts out “honey, we should go to that Italian restaurant” — will Siri
then make a reservation? On a more nefarious note, will my wife be able
to say “Siri, show me my husband’s hidden email.” When walking down a
street, will Siri overhear other conversations and react accordingly?
Siri
will be fantastic in the car, that’s for certain. She will also be very
accommodating when you’re on your own — imagine shouting across the
room “Siri, do I need to wear a jacket today?” or “Siri, download the
latest episode of Glee.” Siri will be unusable in public, though, while
on the move — and that’s the one time where you really don’t want to be
looking down at that darn on-screen keyboard.
Via Kotaku
-----
What if one of the world's most popular 3D engines, the same one used to power many of the most popular console games in the world, also ran in your web browser? That would be pretty interesting, right?
Things just got interesting: Epic Games has announced that their incredibly popular Unreal Engine 3 now works in Adobe Flash, demoing a version of Unreal Tournament 3 running inside the new Adobe Flash Player 11.
That means porting existing games to work in a browser-based solution—and there are a ton of games on Unreal Engine 3—would be more or less turnkey.
A quick look at the screenshots provided by Epic indicate that the engine isn't as powerful as a non-browser-based engine—no big surprise there—but that it's still very much a "real" 3D experience. (I haven't yet seen the engine in motion.)
Even better, developers will be able to migrate their games from, say, iOS over to a browser-based environment without much hassle, making it possible to easily sell browser-based games that play the same games as apps on mobile devices.
But the real thing that should make you arch an eyebrow is Facebook. Nearly every game you can play on Facebook runs on Flash. And now Flash can run hardware-accelerated 3D, just like Real Games.
Tuesday, October 04. 2011
Via TechRadar
By Mike Williams
-----
When Microsoft released the Windows 8 Developer Preview
last month it warned that it was unstable, incomplete, a very early
build which has a long way to go before it's ready for release.
That
doesn't sound too promising - but on installing it we were surprised to
see just how many great new features Windows 8 already contained.
From
the shiny new Metro interface and interesting Explorer tweaks, to new
applets and major performance enhancements, Windows 8 is - even at this
early stage - packed with essential functionality.
Here are 18 cool things Windows 8 does that Windows 7 doesn't
1. Boot quickly - by default
Yes, we know - every version of Windows promises boot time improvements. But this time Microsoft has really delivered.
Our test Dell Inspiron 1090 (a seriously basic laptop) took 48 seconds to launch Windows 7 from the boot loader.
Choose the Windows 8 option, though, and the Metro screen appeared in only nine seconds - more than five times faster.
How
does it work? There are many tweaks, but maybe the most important
happens when the system shuts down. It closes all your programs as
normal, but the kernel is now hibernated, its RAM contents saved to your
hard drive. This doesn't take long, and when you reboot your system can
be reinitialised far faster than before.
2. Display alerts immediately
Your
Windows 8 laptop won't just load faster, it'll also display useful
information right away, without you having to do anything at all.
And
that's because your lock screen, where you'll normally log in, can now
be customised with apps which show you details on waiting emails, your
schedule, RSS feeds, whatever you like.
So Windows 8 means you
won't necessarily have to turn on your laptop, wait for an age as it
loads, then wait even longer to launch an application, just to discover
some really basic item of data: it could be available on the lock screen
in seconds.
3. Log on without passwords
If you already
have more than enough passwords to remember, then the good news is that
Windows 8 will offer you an unusual alternative: the picture password.
You'll
be able to point Windows to a picture you'd like to use, which you then
click, tap or draw on with your mouse or using a touch screen. So if
you choose a picture of your house, say, you might draw an outline
around the roof, then tap on a window and the front door. Windows will
remember your gestures, and won't allow anyone to log in later unless
they can repeat them.
If that doesn't sound appealing, don't worry
- you can continue to log in with a regular alphanumeric password if
you prefer, just as before.

4. Enjoy a dynamic desktop
The
Windows 8 Metro interface doesn't give you static shortcuts to launch
its applications. Instead you get dynamic tiles, which you can change in
size to reflect an app's importance, and freely organise into whatever
groups best suits your needs.
And, again, these tiles aren't just
used to launch the apps. They can also display information from them, so
if something interesting has just appeared on an RSS feed you're
watching, then you'll get to see it right away.

5. Synchronise your settings
Of
course, with so much functionality on the Metro desktop, it may take a
while to set it up just the way you like. But don't worry, you only have
to do this once, even if you've several Windows 8 PCs, because you'll
be able to synchronise your Metro apps, their settings and application
histories (as well as login details for applications and websites)
across all your systems, entirely automatically.
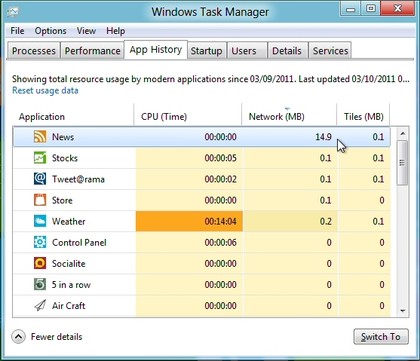
6. Spot resource hogs
All
this syncing, email-checking, RSS monitoring and so on could become a
little expensive if you're using a metered 3G connection, of course. So
it's just as well that the new Windows 8 Task Manager includes an App
History feature which can show you exactly who's hogging all your
network bandwidth (as well as your CPU time, hard drive and RAM).
7. Close apps automatically
Traditionally
Windows has left it up to you to manage the programs you run. So you
can launch as many as you like, and the system won't complain: it'll
just get slower, and slower, and slower as you run out of RAM and it
starts swapping to disk.
Windows 8 is fortunately a little
different, at least when running Metro apps. If you're running short of
resources then it'll close down anything you've not used for a while, to
try to help out. Don't worry, the app's state is saved first, so you
don't lose anything; relaunch it and you'll carry on exactly where you
left off.
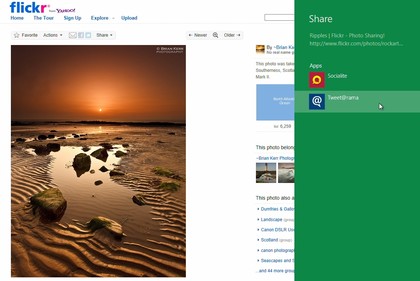
8. Share easily
Sharing something you've found
online is an everyday experience for most web users, and so it's great
to see Microsoft build that idea into Windows 8. If you've discovered a
great photo or web page in IE10
then simply hit the Share button and you'll be able to send its link
via any compatible app you've installed - and they'll then update your
Twitter, Facebook or other account right away.
9. Work on files with ease
The Windows 8 Explorer now uses a
ribbon-style interface, which brings many otherwise tricky to find
options within very easy reach.
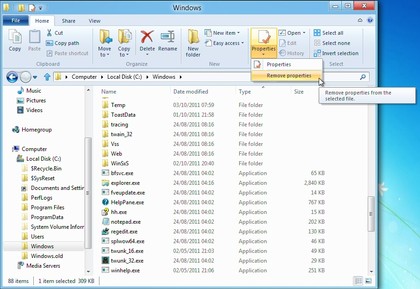
If you want to remove metadata
containing personal information in Windows 7, for instance, you must
right-click the file, select Properties, choose the Details tab, and
click "Remove Properties and Personal Information".
In Windows 8, all you have to do is click the file and choose Remove Properties from the Properties list: much easier.
There
are many similar shortcuts. But if they're not enough, then you can
make any Explorer ribbon option even easier to access it by adding it to
the Quick Access toolbar, which appears in the Explorer title bar.
It'll then only ever be a couple of clicks away.
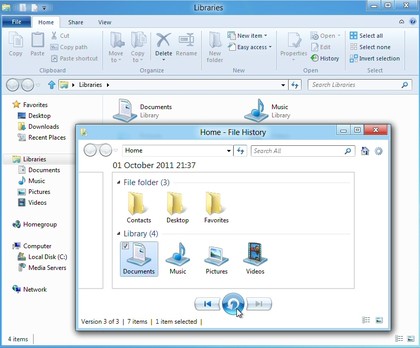
10. Back up automatically
Windows
8 includes a very easy-to-use File History feature, which can
automatically back up whatever folders you like, at the frequency you
specify.
This could be a complete system backup to a network
drive, if you like. But it could also just save key folders like
Documents and Pictures to a USB flash drive, and once you've set this up
there's no further configuration required. Simply plug in the drive
every few days, File History will automatically detect it, and your
preferred files will automatically be backed up.
11. Download safely
Internet
Explorer's SmartScreen filter is a handy technology which can check
downloads against a database of known malicious sites and dangerous
programs, blocking the file if it finds a match. Previously this was
only available within IE, but in Windows 8 SmartScreen will be used
system-wide, so you'll have an extra layer of protection no matter which
browser you're using.
12. Mount ISO files
Windows 7
gained the ability to burn ISO images to disc, but if you just want to
check or access their contents then Windows 8 goes one better. Just
right-click the image, select Mount, and a new virtual optical drive
will appear in Explorer. Double-click this to view the image contents,
launch whatever programs it contains, or generally treat it just like
any other disc.
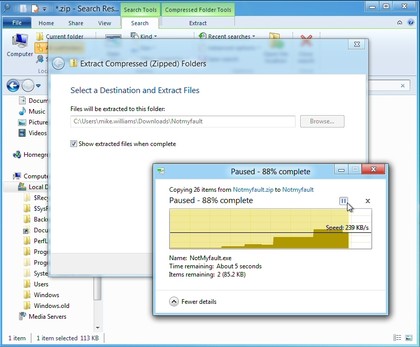
13. Pause file copies
Once you've started a
Windows file copy operation, that used to be it: you had to wait until
it was finished. But not any more. The new File Copy dialog includes a
tiny pause button, so if you need to do something else for a moment,
just click to pause the copies, click again to resume.
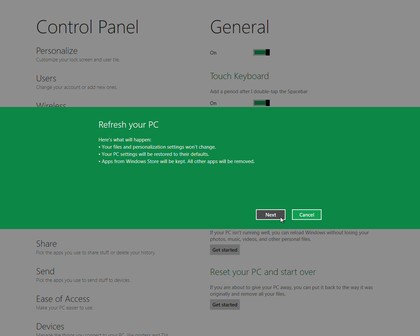
14. Fix problems easily
If
your PC is in a bad way then you've always been able to reinstall
Windows. But you'd have to find your Windows disc, first, and pay close
attention to the installation options to make sure you choose the one
you need.
Windows 8 gets rid of all that hassle by introducing a
"Refresh your PC" option (Control Panel > General). This also
essentially reinstalls Windows, but there's no disc required, no complex
options to consider, not even very long to wait: we've used it two or
three times and it's quickly repaired any glitches we encountered.
15. Run other operating systems
If,
despite all of this, you still feel that Windows 7 has some advantages -
then that may not be a problem. Because Windows 8 now includes
Microsoft's Client Hyper-V virtualisation platform, which allows you to
install other operating systems onto virtual machines and run them on
your desktop.
You will need to be running 64-bit Windows,
however, and have a CPU which supports Second Level Address Translation
(that's Intel's Core i3, i5 and i7 and AMD's Barcelona processors).
But
if your system qualifies then you'll find this is a far better and more
powerful solution than Microsoft's Virtual PC, or Windows 7's XP Mode,
and should be ideal for running most legacy applications on your Windows
8 system.
Friday, September 16. 2011
The technicians at SecureAlert’s monitoring center in Salt Lake City sit in front of computer screens filled with multicolored dots. Each dot represents someone on parole or probation wearing one of the company’s location-reporting ankle cuffs. As the people move around a city, their dots move around the map. “It looks a bit like an animated gumball machine,” says Steven Florek, SecureAlert’s vice-president of offender insights and knowledge management. As long as the gumballs don’t go where they’re not supposed to, all is well.
The company works with law enforcement agencies around the U.S. to keep track of about 15,000 ex-cons, meaning it must collect and analyze billions of GPS signals transmitted by the cuffs each day. The more traditional part of the work consists of making sure that people under house arrest stay in their houses. But advances in the way information is collected and sorted mean SecureAlert isn’t just watching; the company says it can actually predict when a crime is about to go down. If that sounds like the “pre-cogs”—crime prognosticators—in the movie Minority Report, Florek thinks so, too. He calls SecureAlert’s newest capability “pre-crime” detection.
Using data from the ankle cuffs and other sources, SecureAlert identifies patterns of suspicious behavior. A person convicted of domestic violence, for example, might get out of jail and set up a law-abiding routine. Quite often, though, SecureAlert’s technology sees such people backslide and start visiting the restaurants or schools or other places their victims frequent. “We know they’re looking to force an encounter,” Florek says. If the person gets too close for comfort, he says, “an alarm goes off and a flashing siren appears on the screen.” The system doesn’t go quite as far as Minority Report, where the cops break down doors and blow away the perpetrators before they perpetrate. Rather, the system can call an offender through a two-way cellphone attached to the ankle cuff to ask what the person is doing, or set off a 95-decibel shriek as a warning to others. More typically, the company will notify probation officers or police about the suspicious activity and have them investigate. Presumably with weapons holstered. “It’s like a strategy game,” Florek says. (BeforeBloomberg Businessweek went to press, Florek left the company for undisclosed reasons.)
It didn’t used to be that a company the size of SecureAlert, with about $16 million in annual revenue, could engage in such a real-world chess match. For decades, only Fortune 500-scale corporations and three-letter government agencies had the money and resources to pull off this kind of data crunching. Wal-Mart Stores (WMT) is famous for using data analysis to adjust its inventory levels and prices. FedEx (FDX) earned similar respect for tweaking its delivery routes, while airlines and telecommunications companies used this technology to pinpoint and take care of their best customers. But even at the most sophisticated corporations, data analytics was often a cumbersome, ad hoc affair. Companies would pile information in “data warehouses,” and if executives had a question about some demographic trend, they had to supplicate “data priests” to tease the answers out of their costly, fragile systems. “This resulted in a situation where the analytics were always done looking in the rearview mirror,” says Paul Maritz, chief executive officer of VMware (VMW). “You were reasoning over things to find out what happened six months ago.”
In the early 2000s a wave of startups made it possible to gather huge volumes of data and analyze it in record speed—à la SecureAlert. A retailer such as Macy’s (M) that once pored over last season’s sales information could shift to looking instantly at how an e-mail coupon for women’s shoes played out in different regions. “We have a banking client that used to need four days to make a decision on whether or not to trade a mortgage-backed security,” says Charles W. Berger, CEO of ParAccel, a data analytics startup founded in 2005 that powers SecureAlert’s pre-crime operation. “They do that in seven minutes now.”
Now a second wave of startups is finding ways to use cheap but powerful servers to analyze new categories of data such as blog posts, videos, photos, tweets, DNA sequences, and medical images. “The old days were about asking, ‘What is the biggest, smallest, and average?’?” says Michael Olson, CEO of startup Cloudera. “Today it’s, ‘What do you like? Who do you know?’ It’s answering these complex questions.”
The big bang in data analytics occurred in 2006 with the release of an open-source system called Hadoop. The technology was created by a software consultant named Doug Cutting, who had been examining a series of technical papers released by Google (GOOG). The papers described how the company spread tremendous amounts of information across its data centers and probed that pool of data for answers to queries. Where traditional data warehouses crammed as much information as possible on a few expensive computers, Google chopped up databases into bite-size chunks and sprinkled them among tens of thousands of cheap computers. The result was a lower-cost and higher-capacity system that lots of people can use at the same time. Google uses the technology throughout its operations. Its systems study billions of search results, match them to the first letters of a query, take a guess at what people are looking for, and display suggestions as they type. You can see the bite-size nature of the technology in action on Google Maps as tiny tiles come together to form a full map.
Cutting created Hadoop to mimic Google’s technology so the rest of the world could have a way to sift through massive data sets quickly and cheaply. (Hadoop was the name of his son’s toy elephant.) The software first took off at Web companies such as Yahoo! (YHOO) and Facebook and then spread far and wide, with Walt Disney (DIS), the New York Times, Samsung, and hundreds of others starting their own projects. Cloudera, where Cutting, 48, now works, makes its own version of Hadoop and has sales partnerships withHewlett-Packard (HPQ) and Dell (DELL).
Dozens of startups are trying to develop easier-to-use versions of Hadoop. For example, Datameer, in San Mateo, Calif., has built an Excel-like dashboard that allows regular business people, instead of data priests, to pose questions. “For 20 years you had limited amounts of computing and storage power and could only ask certain things,” says Datameer CEO Stefan Groschupf. “Now you just dump everything in there and ask whatever you want.” Top venture capital firms Kleiner Perkins Caufield & Byers and Redpoint Ventures have backed Datameer, while Accel Partners, Greylock Partners, and In-Q-Tel, the investment arm of the CIA, have helped finance Cloudera.
Past technology worked with data that fell neatly into rows and columns—purchase dates, prices, the location of a store. Amazon.com (AMZN), for instance, would use traditional systems to track how many people bought a certain type of camera and for what price. Hadoop can handle data that don’t fit into spreadsheets. That ability, combined with Hadoop’s speedy divide-and-conquer approach to data, lets users get answers to questions they couldn’t even ask before. Retailers can dig into not just what people bought but why they bought it. Amazon can (and does) analyze its website logs to see what other items people look at before they buy that camera, how long they look at them, whether certain colors on a Web page generate more sales—and synthesize all that into real-time intelligence. Are they telling their friends about that camera? Is some new model poised to be the next big hit? “These insights don’t come super easily, but the information is there, and we do have the machine power now to process it and search for it,” says James Markarian, chief technology officer at data specialist Informatica (INFA).
Take the case of U.S. Xpress Enterprises, one of the largest private trucking companies. Through a device installed in the cabs of its 10,000-truck fleet, U.S. Xpress can track a driver’s location, how many times the driver has braked hard in the last few hours, if he sent a text message to the customer saying he would be late, and how long he rested. U.S. Xpress pays particular attention to the fuel economy of each driver, separating out the “guzzlers from the misers,” says Timothy Leonard, U.S. Xpress CTO. Truckers keep the engines running and the air conditioning on after they’ve pulled over for the night. “If you have a 10-hour break, we want your AC going for the first two hours at 70 degrees so you can go to sleep,” says Leonard. “After that, we want it back up to 78 or 79 degrees.” By adjusting the temperature, U.S. Xpress has lowered annual fuel consumption by 62 gallons per truck, which works out to a total of about $24 million per year. Less numerically, the company’s systems also analyze drivers’ tweets and blog posts. “We have a sentiment dashboard that monitors how they are feeling,” Leonard says. “If we see they hate something, we can respond with some new software or policies in a few hours.” The monitoring may come off as Big Brotherish, but U.S. Xpress sees it as key to keeping its drivers from quitting. (Driver turnover is a chronic issue in the trucking business.)
How are IBM (IBM) and the other big players in the data warehousing business responding to all this? In the usual way: They’re buying startups. Last year, IBM bought Netezza for $1.7 billion. HP, EMC (EMC), and Teradata (TDC) have also acquired data analytics companies in the past 24 months.
It’s not going too far to say that data analytics has even gotten hip. The San Francisco offices of startup Splunk have all the of-the-moment accoutrements you’d find at Twitter or Zynga. The engineers work in what amounts to a giant living room with pinball machines, foosball tables, and Hello Kitty-themed cubes. Weekday parties often break out—during a recent visit, it was Mexican fiesta. Employees were wearing sombreros and fake moustaches while a dude near the tequila bar played the bongos.
Splunk got its start as a type of nuts-and-bolts tool in data centers, giving administrators a way to search through data tied to the low-level operations of computers and software. The company indexes “machine events”—the second-by-second records produced by computing devices to keep track of their actions. This could include records of every time a server stores information, or it could be the length of a cell phone call and what type of handset was used. Splunk helps companies search through this morass, looking for events that caused problems or stood out as unusual. “We can see someone visit a shopping website from a certain computer, see that they got an error message while on the lady’s lingerie page, see how many times they tried to log in, where they went after, and what machine in some far-off data center caused the problem,” says Erik Swan, CTO and co-founder of Splunk. While it started as troubleshooting software for data centers, the company has morphed into an analysis tool that can be aimed at fine-tuning fraud detection systems at credit-card companies and measuring the success of online ad campaigns.
A few blocks away from Splunk’s office are the more sedate headquarters of IRhythm Technologies, a medical device startup. IRhythm makes a type of oversize, plastic band-aid called the Zio Patch that helps doctors detect cardiac problems before they become fatal. Patients affix the Zio Patch to their chests for two weeks to measure their heart activity. The patients then mail the devices back to IRhythm’s offices, where a technician feeds the information into Amazon’s cloud computing service. Patients typically wear rivals’ much chunkier devices for just a couple of days and remove them when they sleep or shower—which happen to be when heart abnormalities often manifest. The upside of the waterproof Zio Patch is the length of time that people wear it—but 14 days is a whole lot of data.
IRhythm’s Hadoop system chops the 14-day periods into chunks and analyzes them with algorithms. Unusual activity gets passed along to technicians who flag worrisome patterns to doctors. For quality control of the device itself, IRhythm uses Splunk. The system monitors the strength of the Zio Patch’s recording signals, whether hot weather affects its adhesiveness to the skin, or how long a patient actually wore the device. On the Zio Patch manufacturing floor, IRhythm discovered that operations at some workstations were taking longer than expected. It used Splunk to go back to the day when the problems cropped up and discovered a computer glitch that was hanging up the operation.
Mark Day, IRhythm’s vice-president of research and development, says he’s able to fine-tune his tiny startup’s operations the way a world-class manufacturer like Honda Motor (HMC) or Dell could a couple years ago. Even if he could have afforded the old-line data warehouses, they were too inflexible to provide much help. “The problem with those systems was that you don’t know ahead of time what problems you will face,” Day says. “Now, we just adapt as things come up.”
At SecureAlert, Florek says that despite the much-improved tools, extracting useful meaning from data still requires effort—and in his line of work, sensitivity. If some ankle-cuff-wearing parolee wanders out-of-bounds, there’s a human in the process to make a judgment call. “We are constantly tuning our system to achieve a balance between crying wolf and catching serious situations,” he says. “Sometimes a guy just goes to a location because he got a new girlfriend.”
Wednesday, September 14. 2011
Via InfoWorld
-----
The operators of the TDSS botnet are renting out access to infected computers for anonymous Web activities
Cloud computing isn't just opening up new opportunities for
legitimate organizations worldwide; it's also proving a potential boon
for cyber criminals as it inexpensively and conveniently puts disposal
powerful computing resources at their fingertips, which helps them
quickly and anonymously do their dirty deeds.
Among the latest examples of this unfortunate trend comes via Kaspersky Labs:
The company has reported that the operators of TDSS, one of the world's
largest, most sophisticated botnets, are renting out infected computers
to would-be customers through the awmproxy.net storefront. Not only has
TDSS developed a convenient Firefox add-on, it's accepting payment via
PayPal, MasterCard, and Visa, as well as e-currency like WebMoney and Liberty Reserve.
Also
known as TDL-4, the TDSS malware employs a rootkit to infect
Windows-based systems, allowing outsiders to use affected machines to
anonymously surf the Web, according to Kaspersky researchers Sergey Golobanov and Igor Soumenkov.
The malware also removes some 20 malicious programs from host PCs to
sever communication with other bot families. (Evidently, botnet
operators are becoming increasingly competitive with one another.)
According
to the researchers, the operators of TDSS are effectively offering
anonymous Internet access as a service for about $100 per month. "For
the sake of convenience, the cyber criminals have also developed a
Firefox add-on that makes it easy to toggle between proxy servers within
the browser," they reported.
According to Golovanov, once
machines are infected, a component called socks.dll notifies
awmproxy.net that a new proxy is available for rent. Soon after, the
infected PC starts to accept proxy requests.
Notably, Kapersky does offer a utility to remove TDSS dubbed TDSSKiller.
This
isn't the first instance of an organization making expansive
cloud-based systems available to potential ne'er-do-wells, though it's
arguably among the most brazen examples. Amazon Web Services have proven
possible to exploit to pull off cheap brute-force attacks and could be abused for other unsavory deeds as well, such as spam propagation.
Via SlashGear
By Chris Burns
-----
During a lovely September week in 2011, Microsoft Windows 8 was announced and launched for developers. The event this launch occurred at was what Microsoft was presenting as a welcome to Windows 8, especially in regards to the 5,000 developers at BUILD, launching the platform with there eyes directly fixed on applications, the whole situation a large opportunity for developers. This is the beginning of Windows 8 as it exists in a sense that there’s no product launch here from Microsoft, instead there’s an opportunity for 3rd party developers to get on board here right at the start of the next-wave OS. What lies beneath is a living document which takes what Microsoft Windows 8 is at the start here in 2011 and how it will evolve over time.

Three years ago was when Windows 7 launched, since then 450 million copies have sold. Inside September 2011, the amount of users using Windows 7 has finally trumped the amount of users using Windows XP on the consumer market. Microsoft tells us they know this because they’re working with the numbers coming from machines hitting the Windows Update Service. As with any update to a new version of a major operating system, one must ask a similar question as – and you’ll have to allow me to nerd out for a moment here – Alan Bradley from TRON when he asked what changes had REALLY been made to the system that Microsoft would find it necessary to give it a whole new number.
Turns out 1,502 product changes have been made to Windows XP since Microsoft released it to manufacturing, these all being non-security updates. Improvements galore! Now what does this mean for Windows 8? Does it mean that the software will be continuously updated as the folks at Microsoft see ways to improve it? Of course, that’s a given. How many changes have been made between the Windows XP and Windows 7 we’ve known between their inception date and this end-of-summer 2011 timeframe where Windows 8 is released? That’s a number we’ll have to figure out on our own.
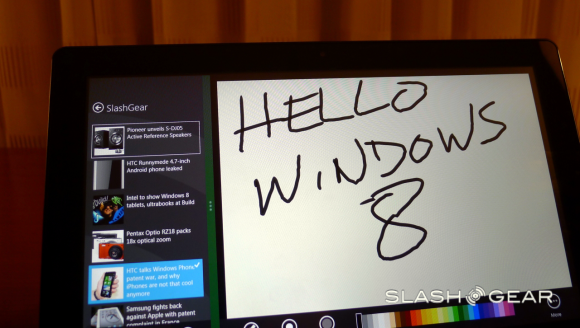
Reimagining Windows
Microsoft brings you Windows 8 as a operating system that is said to improve everything they brought forth in Windows 7, and what’s more, every bit of software that runs currently on Windows 7 will be able to run on Windows 8 without a problem.
Chipsets
ARM chips equal integrated engineering. Where X86, Microsoft says, was the same for every system, ARM chips are optimized for unique situations. Like what Microsoft says about software made for working on Windows 7 now also working on Windows 8, so too does everything they present here work on ARM chips.

Boldness
What’s so bold about Windows 8 is that they’re envisioning an operating system that scales from small form factors, keyboardless tablets, all the way up to gigantic servers running hundreds of processors.
Julie Larson Green, Corporate Vice President of the Windows Experience at Microsoft noted during the week of the reveal of Windows 8 that they had started planning Windows 8 in June of 2009, before they even shipped Windows 7 out the door. Of course changes in both industry and technology spark change, and in this mobile landscape and move by many from one platform to another and/or the adoption of several platforms happening by the public, Microsoft planned accordingly. Microsoft wanted to top the release of Windows 7, but they did not want to do it in a way that was either linear or reactive – this being an interesting goal of course at that time as the idea of a tablet computer simply wasn’t a reality at the time – so what is there to react to?
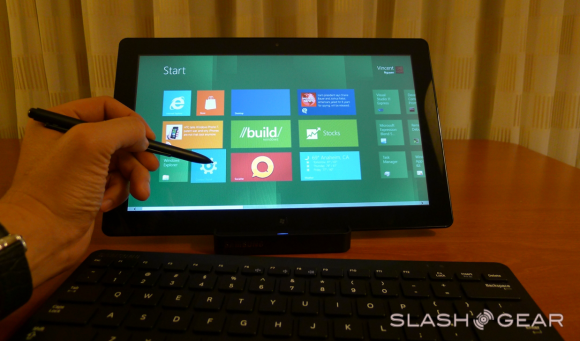
In Windows 7 there were studies on form factor, user action models, and best of all touch. Microsoft has noted that they were the first group to add touch to a major operating system. As you know well, since that time, touch has all but consumed the mobile market, and recent developments in non-mobile computing have trended toward touch as well to a degree. With this, the demand for developers to create apps for every single little function, one by one, this showing itself prevalently again on mobile, but non-mobile beginning to take back what is theirs in the recent past as well with on-device app stores on all machines. These are only two of a whole slew of points Microsoft touched on during the BUILD conference showing off the first real look at Windows 8 in September of 2011.
Tablets and PCs
You begin with a lockscreen (seen at the top of this post). This screen doesn’t look unlike what you’re used to with Windows Phone devices, giving you pre-opening updates about time, date, updates, and of course its all displayed with a background of your choice. One of the new ideas Microsoft has to make this experience unique is “Picture Password”.

What Picture Password consists of is a specific photo or digital image that, when you see it, you’ll know to draw a certain combination of shapes and lines on your display. If you draw the correct combination, you will be logged in. Circles and lines are what’s at play here – perhaps drawing a hat on a squirrel will be your password combo?
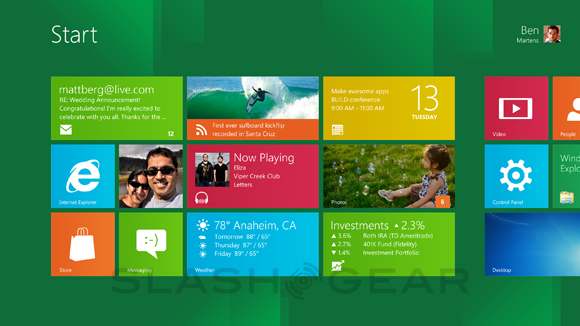
Then there’s a Start Screen. This is the place where you’ll return all the time before and after moving to other screens and apps. You’ll again recognize the look of this space as being a rather Windows Phone experience, and as each app is represented by what Microsoft calls a “tile”, you’ll certainly feel at home if you’re an avid Windows Phone user. Each tile has the ability to show off different actions before its activated to reveal the app inside, movement and, for example, feeds showing social networking news. The “serendipity of the web” has here been brought into Windows.
Tiles can express essentially anything you want and are themselves resizable and customizable. Tiles can open up to apps or they can sit by themselves and work. There are “groups” that can hold tiles “like folders” as they say, and there’s a new feature called “Semantic Zoom.” What this Semantic Zoom does is to pull you back from your interface in a way that you’ve never been able to do on a Windows device before. Fast and fluid touch language throughout, allowing you access to all of your media, all of your content, all of your apps at once.
We got hands-on with the first Windows 8 tablet at BUILD 2011 as well, see the video unboxing and hands-on here:
Metro-Style Apps
There is a new kind of app called Metro-Style Apps. The first thing that makes a Metro-Style app what it is full immersion. What Windows has done here is to change what they’ve done in the past, that is adding widgets and “doodads” all around the majority of apps and is now being a bit more humble, letting the app take the show.
Any app on Windows Phone 8 can be turned into a Secondary Tile. You can, for instance, “pin” a webpage to your Start Screen – in this case you’ll have all the same features your original app had, here because this is a webpage and your original app was a web-based app, you’re able to see a changing feed straight from your desktop.
Charms
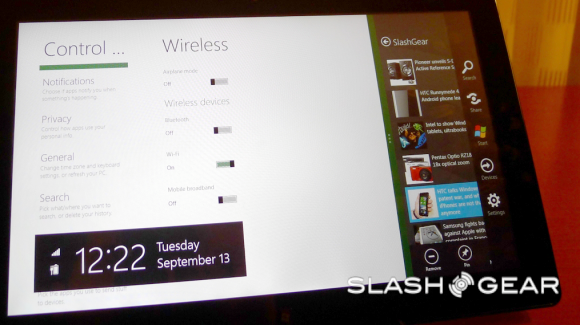
Charms are next – what this feature, activated by a swipe across your screen, is comprised of several icons, these depending on the app or location inside your system you are at. This may seem intuitive to those of you who’ve been using computers for years and years now, but as software engineers make the transition between mobile and stationary OS being separate to being one in the same, it’s little points like this that make all the difference.
What Microsoft is showing us here in Windows 8 is their next step towards a singularity in operating systems. Moving in and out of apps, shutting them down and opening them up, and even having more than one application open and working at once on the same page. This again is something that desktop mobile operating systems have been able to do for many years now, but as mobile moves into the fold, this is a big step taken.
Windows Key
There’s a button, be it physical or on the screen, wherever, that will always bring you back to your Start Screen. This is your Windows Key. If you’re using a Windows 8 tablet, you’ll likely have a physical or haptic-feedback-filled Windows Key. If you’re using a device with no physical keys, the Windows Key will be in some sneaky places for you to access.
Windows Store
For developers (who will be mentioned many more times before this guide is through), it’s the newly minted Windows Store that should be paid attention to. Windows users will be able to access this store for apps anywhere Windows is sold worldwide. Go wild!
Apps
Microsoft feels that all apps should be able to work together, all of this without any extra work done by the developers of the apps in question. One of the most obvious “contracts” this connectedness will be working on is sharing. Have a bit of content you’d like to share? Grab your Charms, hit the Share Charm, and share it through, for example, “Friend Share.” Here you’re able to contact your contacts through a huge variety of ways – share and go! The data package is taken by one app and sent to another app, all of this possible with any set of apps that have sharing activated.
Sharing can happen from any app in Windows.
Search is next, it being one the most essential bits in any successful computer system, operating systems a must. The Search Charm is present in quite a few apps and in the system to search files. You expect Windows to know how to search files, but here we’ve got a few new options, one of them being autocomplete of options if you like. You search your term and you get results PLUS you get a list of apps that are able to also search themselves. Search a term and find results on your own computer, then search through your web app, search a social networking site, search anything that supports search.
A hypothetical situation for this ability to search and select content from a variety of apps and services is if you’re creating an album of photos on a website. You can search from your local device, your app which seeks photos you’ve got on a cloud on the internet, and an app that seeks photos on your local network. Grab em all without having to launch every single app, all at once with search only. The selling point, if I may be so bold here, is that the apps are what makes up the system. Just like console video game systems, inkjet printers, and… well… every home computer in history, essentially, this system relies on the apps that it runs to run. That’s the promotion in part.

Spellcheck, auto-correct, “squiggle” underlining of words to show you they’re not necessarily understood by the system as English (or whatever language(s) you’ve got running). All of this is what you remember it as being from your current and past tens of years on your Windows machine – all of it’s intact here and is available free as part of Microsoft’s dealings with third party app developers. The same is true of the on-screen touch keyboard keyboard.
Measuring Style Device App / Connections
As you may well know by now, computers of all types, most recently mobile devices like tablets are able to connect to a plethora of other devices via Bluetooth, HDMI cable, USB, and a bunch of other slightly less popular means right this moment. In Windows 8, these connections will be handled by your Charms. Much in the same way that selecting File-Print works in most Windows systems now (though I’m sure some developers would disagree), you’re able to hit a charm, hit print, and if you like, work with a selection of settings. This interface has another name: Measuring Style Device App.
What a Measuring Style Device App does is represent a device in the system. This could be compared, if you wish, to drivers provided by manufacturers for specific devices, instead here it’s a whole new entity called a MSDA (for short) and has the ability to bring you a large set of options in, for example, a Charm.
Internet Explorer 10
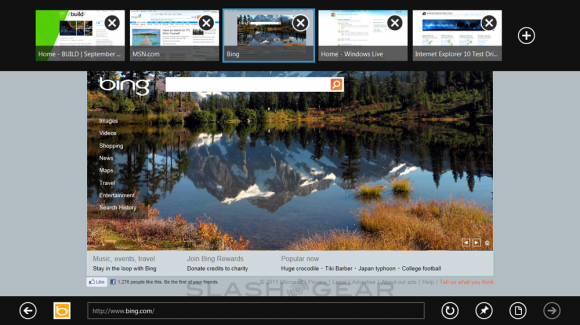
The newest version of IE aka Internet Explorer will be available as a metro-style app. Full screen action for you lovers of your monitors with all of the same hardware acceleration (even more than IE 9 does), same performance and better, same compliance and standards as IS and better, same security and same privacy as IE 9. But it’s better, better I tell you! Here you’ve got a totally immersive mode like with the other metro-style apps, and you’ve got four big gestures that, like with a lot of the rest of your system here, do the following:
Top to Bottom: Use the User Interface, in this case see your controls for webpages.
Right Side: Charms.
Left Side: Go back.
Of course you can create new tabs including the forever helpful “private” tab, you can travel to webpages, go back and forth, and use the internet in the same sort of hands-off way that all great web browsers work with. Internet Explorer 10 is able to go full screen and will, with gestures, be able to access the same lovely menus many other Windows 8 optimized apps will be able to as well.
Whispers of Photoshop
Adobe’s photo editing app has become so well known and used that an edited photo in our modern world is better known as having been “Photoshopped” than it is as having been “modified” or “photo manipulated”. We know this week at BUILD 2011 that Windows 8 will work with Photoshop on a touch platform. This isn’t the first time we’ve seen Adobe bring a Photoshop branded app to a mobile platform, but it is the first time we’ve seen what appears very much to be a full-fledged Photoshop app that, as you know from above, will be able to work with keyboard and mouse, but will here be able to work with touch in a way that’s only been available through third party touchscreen displays and drawing pads. What we can hope for is a much more optimized experience in the near future.
Pen (Stylus)

Handwriting, drafting, and graphic arts are promoted in Windows 8 by a new optimization and integration of the pen, or the stylus as you may call it. You may use pen with touch at the same time and you may navigate the whole system with pen as well. Much in the same way that the on-screen keyboard, the physical mouse, and the physical keyboard are all supported for 3rd party developers by Microsoft, so too is the Pen. Get your drawing hand out and try to remember what it was like to use a pencil!
Cloud Connections
Windows 8 will have the ability to work with online clouds of information, developers at Microsoft keeping in mind that this new operating system is most certainly going to be used to access the connected web on many levels and with many different devices and types of devices. Microsoft gives one of the most obvious reasons for this: what if you reach an awesome level on your favorite game, then you’ve got to switch to a new device? You’d have to start over if it wasn’t for the idea of cloud computing – all that information can be stored for access by multiple computers without a hassle, and Windows 8 is built with this idea deep in its heart. Settings down to the state you last left your app in can be saved to the cloud with this system. One you, one system, any number of multiple machines to work with.
Mail and Calendar
Improvements have been made to your basic Mail app on Windows 8. You’ve now got the simple addition of Folders to your Mail app, this right next to Inbox and Content. Organization is key, and the ability to place pieces of content in folders has been a tried and true way to make this happen. As far as Calendar goes, you’re now able to view more than one person’s Calendar at once. For instance if you need to see your wife’s calendar at the same time as your own to plan an event, this dual display mode can come in extremely handy.
People
There’s an app called People which organizes all the humans you know, each of the people displayed with connections to their Facebook, Linkedin, phone number, email(s), and more. This app People acts as an all-encompassing social network hub as you’re not only able to connect to People’s different profile pages on social networks, you can instant messenge them through what appears to be every single instant messenger network in existence, threads of conversation set up, organization abound. The networks take a back seat, Microsoft hopes here, to your connection to the person.
Photos

Your Photos library app connects you to your local photos as well as photos (and other types of images) you’ve got on a large number of photo hosting services and apps. This app, like the rest of the content browsing and interaction apps, appears to be working quite quickly and efficiently on every platform Microsoft is using to show off Windows 8 at BUILD 2011. This Photos app brings your photos together in a way that Microsoft hopes is easy to manifest and understand. Select photos, place them in your digital basket, and share them, only a few gestures from start to finish.
Skydrive
Connected applications is at the heart of Windows 8. Using Windows Phone, you likely know about Skydrive which allows you to place media for later editing and access from the cloud. Your Skydrive Camera Roll on Windows Phone automatically collects photos you’ve taken and uploads them to the cloud. When you’re emailing photos from your Photos app, you’ll automatically be doing so using Skydrive, this allowing you to have these photos hosted by Skydrive instead of having to pack them into the email. You’ve got the option of attaching to the email in a traditional way as well, but Skydrive gives you the ability to, in many cases, send a whole lot quicker.
Heading online to Windows Live and Skydrive will also be optimized to work with Windows 8 to give you access to any of your connected computers. For example if you’re out in the park and you meet Auntie Sue and you want to show her a picture of your half-uncle Fred but all your Fred photos are at your PC at home, you can connect to your PC at home with your mobile device by accessing Windows Live in a web browser and check your Skydrive, there’s your content.
Windows Phone
Along these same lines, syncing and cloud connectedness flows freely through Windows Phone which, at the time Windows 8 is revealed at BUILD 2011, is currently at Windows Phone 7.5 Mango. On Windows Phone here you have only to log in once and you’ve got all of your connections to your various services you
Monday, September 12. 2011
Via Nexus 404
by J Angelo Racoma
-----
Automatic content generators are the scourge of most legitimate writers and publishers, especially if these take some original content, spin it around and generate a mashup of different content but obviously based on something else. An app made by computer science and journalism experts involves artificial intelligence that writes like a human, though.

Developers at the Northwestern University’s Intelligent Information Laboratory have come up with a program called Narrative Science, which composes articles and reports based on data, facts, and styles plugged in. The application is worth more than 10 years’ work by Kris Hammond and Larry Birnbaum who are both professors of journalism and computer science at the university.
Artificial vs Human Intelligence
Currently being used by 20 companies, an example of work done by Narrative Science include post-game reports for collegiate athletics events and articles for medical journals, in which the software can compose an entire, unique article in about 60 seconds or so. What’s striking is that even language experts say you won’t know the difference between the software and an actual human, in terms of style, tone and usage. The developers have recently received $6 million in venture capital, which is indicative that the technology has potential in business and revenue-generating applications.
AI today is increasingly becoming sophisticated in terms of understanding and generating language. AI has gone a long way from spewing out pre-encoded responses from a list of sentences and words in reaction to keywords. Narrative Science can actually compose paragraphs using a human-like voice. The question here is whether the technology will undermine traditional journalism. Will AI simply assist humans in doing research and delivering content? Or, will AI eventually replace human beings in reporting the news, generating editorials and even communicating with other people?
What Does it Mean for Journalism and the Writing Profession?
Perhaps the main indicator here will be cost. Narrative Science charges about $10 each 500-word article, which is not really far from how human copy writers might charge for content. Once this technology becomes popular with newspapers and other publications, will this mean writers and journalists — tech bloggers included — need to find a new career? It seems it’s not just the manufacturing industry that’s prone to being replaced by machines. Maybe we can just input a few keywords like iPhone, iOS, Jailbreak, Touchscreen, Apple and the like, and the Narrative Science app will be able to create an entirely new rumor about the upcoming iPhone 5, for instance!
The potential is great, although the possibility for abuse is also there. Think of spammers and scammers using the software to create more appealing emails that recipients are more likely to act on. Still, with tools like these, it’s only up for us humans to up the ante in terms of quality.
And yes, in case you’re wondering, a real human did write this post.
-----
Personal comments:
One book to read about this: "Exemplaire de démonstration" by Philippe Vasset
Thursday, September 08. 2011
Via OStatic
By Sam Dean
-----
 Now
that Chromebooks--portable computers based on Google's Chrome OS--are
maturing, it's easier to gauge the prospects for Google's first-ever
operating system. As Jon Buys discussed
here on OStatic, these portables have a number of strong points.
However, there are criticisms appearing about them, too, and some of
them echo ones made here on OStatic before.
Specifically, Chrome OS imposes a very two-fisted, cloud-centric model
for using data and applications, where traditional, local storage of
data and apps is discouraged. Recently, Google has sought to close
this gap with its own apps, allowing users to work with its Gmail,
Calendar and Docs apps offline. Will these moves help boost Chrome OS
and use of Chromebooks? In enterprises, they may do so. Now
that Chromebooks--portable computers based on Google's Chrome OS--are
maturing, it's easier to gauge the prospects for Google's first-ever
operating system. As Jon Buys discussed
here on OStatic, these portables have a number of strong points.
However, there are criticisms appearing about them, too, and some of
them echo ones made here on OStatic before.
Specifically, Chrome OS imposes a very two-fisted, cloud-centric model
for using data and applications, where traditional, local storage of
data and apps is discouraged. Recently, Google has sought to close
this gap with its own apps, allowing users to work with its Gmail,
Calendar and Docs apps offline. Will these moves help boost Chrome OS
and use of Chromebooks? In enterprises, they may do so.
Google officials have explained the logic behind allowing offline usage of key Google apps in this post, where they write:
"Today’s
world doesn’t slow down when you’re offline and it’s a great feeling to
be productive from anywhere, on any device, at any time. We’re pushing
the boundaries of modern browsers to make this possible, and while we
hope that many users will already find today’s offline functionality
useful, this is only the beginning. Support for offline document editing
and customizing the amount of email to be synchronized will be coming
in the future. We also look forward to making offline access more widely
available when other browsers support advanced functionality (like
background pages)."
While Google had previously
announced its intent to deliver this offline functionality, the need for
it was undoubtedly accelerated by some of the criticisms of the way
Chrome OS forces users to work almost exclusively in the cloud. It's
also not accidental that the offline capabilities are focused on Google
applications that enterprises care about: mail, document-creation apps,
etc.
Guillermo Garron has gone so far as to reverse his previous
criticisms of Chrome OS based on the new offline functionality, as seen in his post here. He writes:
"This
is something specially good for Chromebooks. Now they are not just new
toys, they can be real productive tools…now Chromebooks are ready for
Prime Time at least to do what they were designed for, with no
limitations."
Researchers at Microsoft have produced
data before that shows that most people use a maximum of five software
applications on a regular basis. In delivering offline functionality for
mail, document creation, and other absolutely key tasks for working
people, Google is hedging the cloud-only bet that it made with Chrome OS
upon its debut. It's the right move for Google to be making, and is
likely to help win over some enterprises that would find working
exclusively in the cloud to be too limiting.
Via MyCE
-----
Symantec, the company behind Norton Anti-Virus, has published a
startling report which estimates nearly $388 billion is lost each year
to cyber crime – $274 billion in sheer wasted time, and the remaining
$114 billion either spent to combat it or deposited into the bank
accounts of criminals.
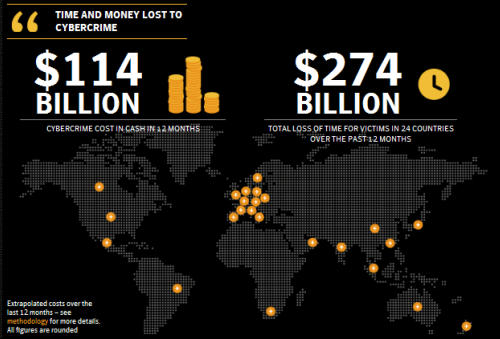
Source: Norton
According to the “Norton Cybercrime Report 2011,”
viruses and malware are the “preventable yet more prevalent” methods
employed by cyber criminals. Conducted earlier this year by StrategyOne,
who polled 19,636 adults, kids and teachers in 24 countries, the study
revealed over 54 percent of online adults have indeed encountered either
threat despite the fact 59 percent incorporate active, up-to-date
anti-virus software. Online scams and phishing rounded out the most
common methods.
Resolving a cyber crime is also a huge hassle for those affected.
Norton’s research found the entire process takes anywhere from four to
16 days depending on where you live; on average, victims spend 10 days.
“These latest cyber crime statistics reflect crime rates in the
physical world, where young adults and men are more often victims of
crime,” said Adam Palmer, Norton Lead Cyber Security Analyst. “Countries
like South Africa and Brazil, where physical crimes against people are
among the highest in the world, are clearly emerging as cyber crime
capitals, too.”
China topped Norton’s list of countries most affected by cyber crime,
boasting an ignominious 85 percent of adults affected. The U.S. wasn’t
too far behind at 73 percent.
The fact the Internet is such a huge part of everyday life in many
countries means cyber thieves have ample prey. 24 percent of respondents
said that they “can’t live without the Internet,” while 41 percent
“need the Internet in their everyday life.” Considering that level of
dependency, it’s not too shocking that nearly 70 percent of adults
reported being the victim of some form of cyber crime.
Joseph LaBrie, an Associate Professor of Psychology at Loyola Marymount University, addressed the mental state of online users and their resistance to educating or protecting themselves.
“Often, because people feel the Internet is too complicated and the
threats are unknown or ambiguous, they default to a learned helplessness
where they simply accept cyber crime as part of the cost of going
online,” said LaBrie. “Also, they cannot visualize online protection
like they can offline security systems like a fence or alarm that act as
a physical deterrent.”
Norton asserts that each day cyber crime affects over one million
people and that 431 million people have been victims of cyber crime in
the last year alone. (via Threat Post)
-----
The study
Thursday, September 01. 2011
Via SlashGear
-----
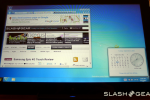
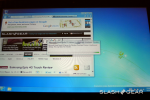
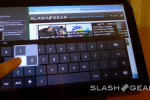
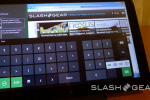
Microsoft Windows chief Steven Sinofsky has taken to the Building Windows 8 blog to explain the company’s decision to keep two interfaces: the traditional desktop UI and the more tablet-friendly Metro UI. His explanation seemed to be in response to criticism and confusion after the latest details were revealed on the new Windows 8 Explorer interface.

On Monday, details on the Windows 8 Explorer file manager interface were revealed showing what looked to be a very traditional Windows UI without any Metro elements. Reactions were mixed with many confused as to what direction Microsoft was heading with its Windows 8 interface. Well, Sinofsky is attempting to answer that and says that it is a “balancing act” of trying to get both interfaces working together harmoniously.
Sinofsky writes in his post:
Some of you are probably wondering how these parts work together to create a harmonious experience. Are there two user interfaces? Why not move on to a Metro style experience everywhere? On the other hand, others have been suggesting that Metro is only for tablets and touch, and we should avoid “dumbing down” Windows 8 with that design.
He proceeds to address each of these concerns, saying that the fluid and intuitive Metro interface is great on the tablet form factor, but when it comes down to getting serious work done, precision mouse and keyboard tools are still needed as well as the ability to run traditional applications. Hence, he explains that in the end they decided to bring the best of both worlds together for Windows 8.
With Windows 8 on a tablet, users can fully immerse themselves in the Metro UI and never see the desktop interface. In fact, the code for the desktop interface won’t even load. But, if the user needs to use the desktop interface, they can do so without needing to switch over to a laptop or other secondary device just for business or work.
A more detailed preview of Windows 8 is expected to take place during Microsoft’s Build developer conference in September. It’s been rumored that the first betas may be distributed to developers then along with a Windows 8 compatible hardware giveaway.
-----
Personal comments:
In order to complete the so-called 'Desktop Crisis' discussion, the point of view of Microsoft who has decided to avoid mixing functionalities between desktop's GUI and tablet's GUI.
The Subjectivity of Natural Scrolling
Switched On: Destop Divergence
Is The Desktop Having an Identity Crisis
|
































 Now
that Chromebooks--portable computers based on Google's Chrome OS--are
maturing, it's easier to gauge the prospects for Google's first-ever
operating system.
Now
that Chromebooks--portable computers based on Google's Chrome OS--are
maturing, it's easier to gauge the prospects for Google's first-ever
operating system. 

